Blob Service Not Immutable
Risk Level: Low
Description
The plugin checks for data immutability configuration for blob services to ensure the integrity of the data that is being maintained. Immutable storage for Azure Blob Storage feature allows users to store sensitive information in a WORM (Write Once, Read Many) states. This state ensures that data cannot be modified or deleted for a user-specified interval.
About the Service
Storage Accounts: An azure storage account is used to store the customer’s data objects such as files, queues, shares, etc. The storage accounts ensure high availability for the clients and allot a unique namespace for the storage data and are accessible from anywhere around the world using HTTP or HTTPS protocols.
Impact
In case the immutable policy is not created for the application, the blob objects might suffer unauthorised edits or deletion. While the creation of the time-based policy will ensure that the file’s integrity is maintained for the specified time period; the legal hold identifier will make sure the data is non-erasable and non-editable for an indefinite time period.
Steps to Reproduce
- Login to azure portal.
- Click on Storage accounts for Services.
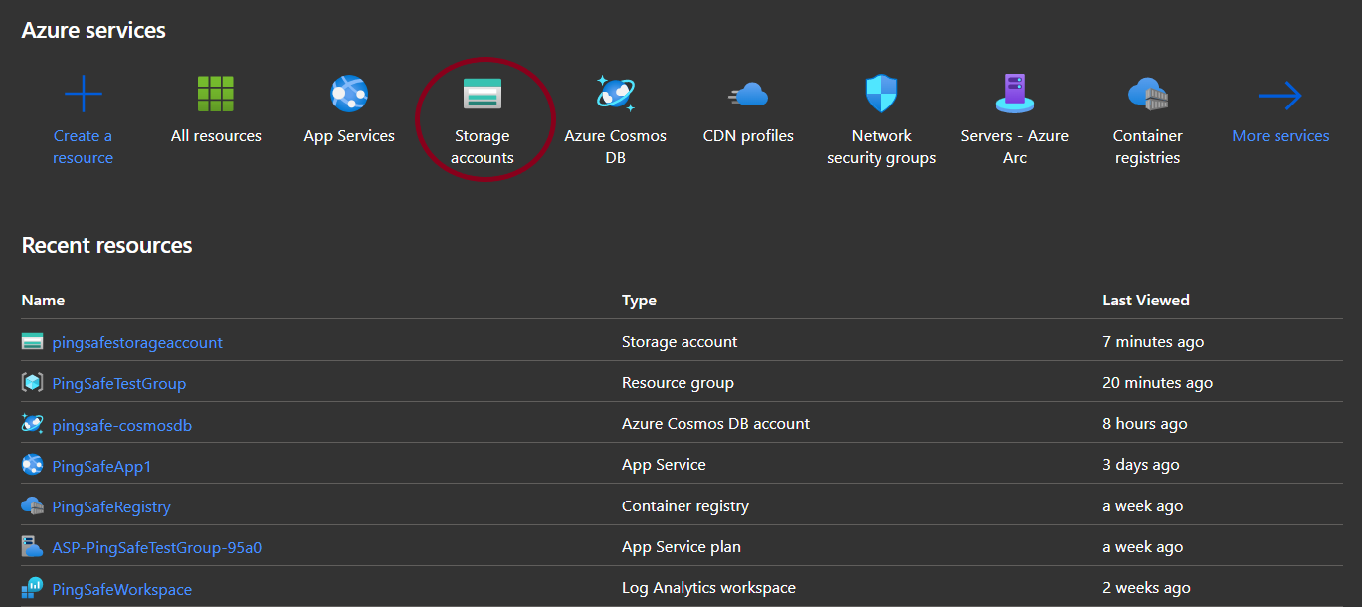
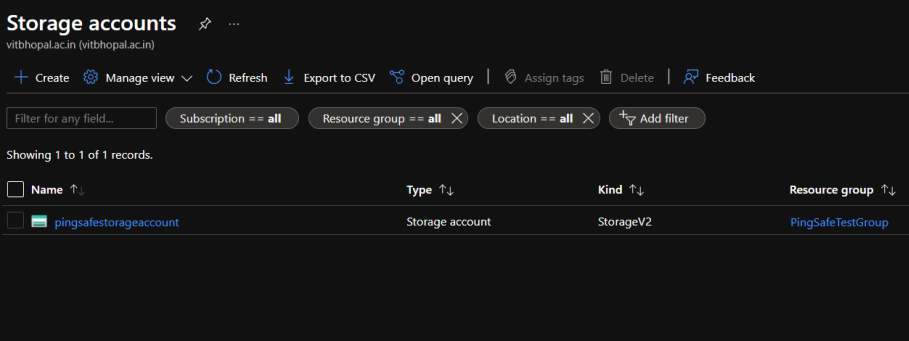
- Select any one of the provided accounts to check for the policy.
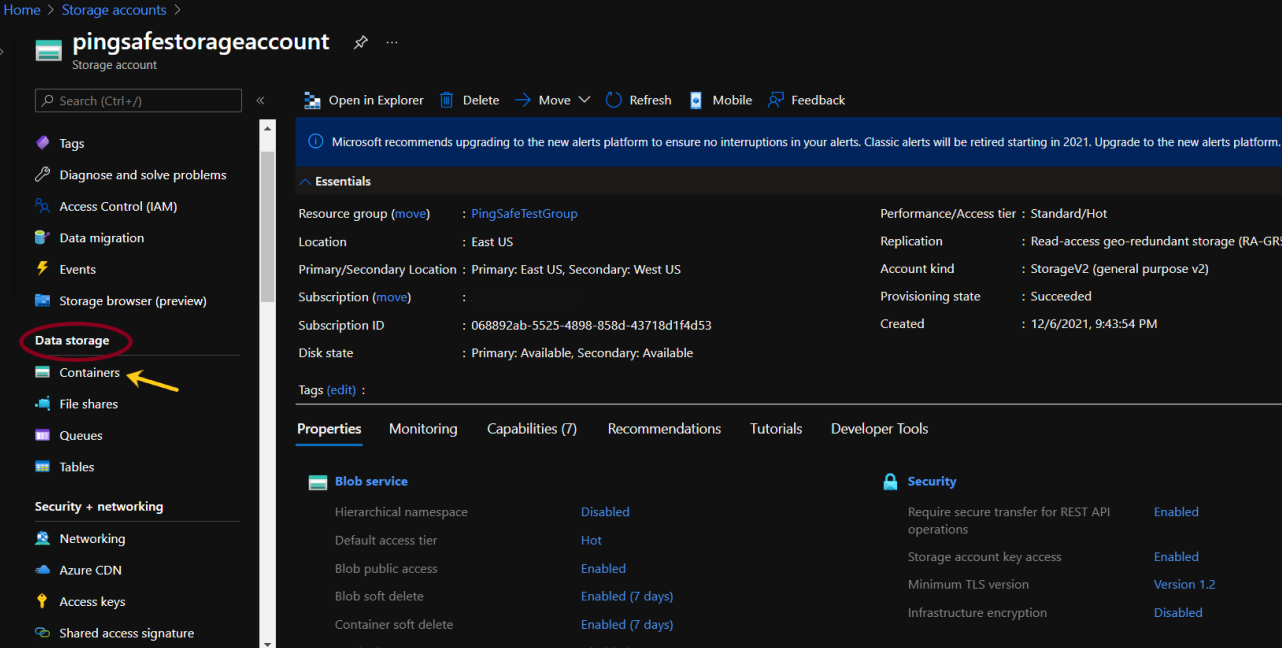
- From the navigation bar, select Containers from Data storage.
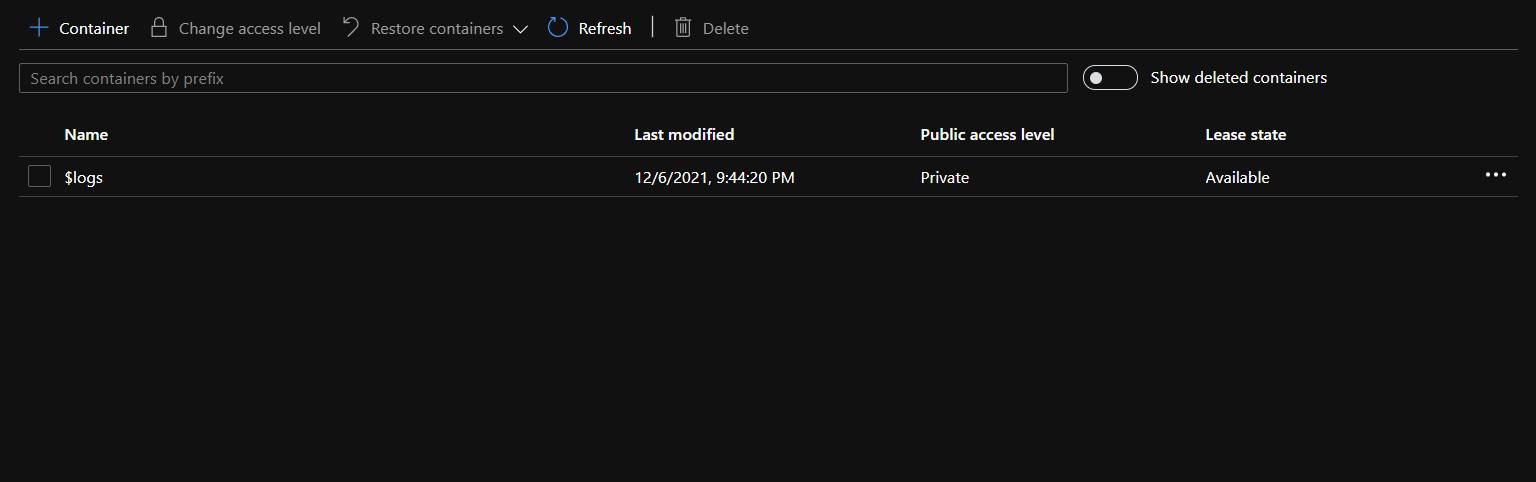
- Select a container from the provided list.
- From the navigation pane select Access policy under Settings.
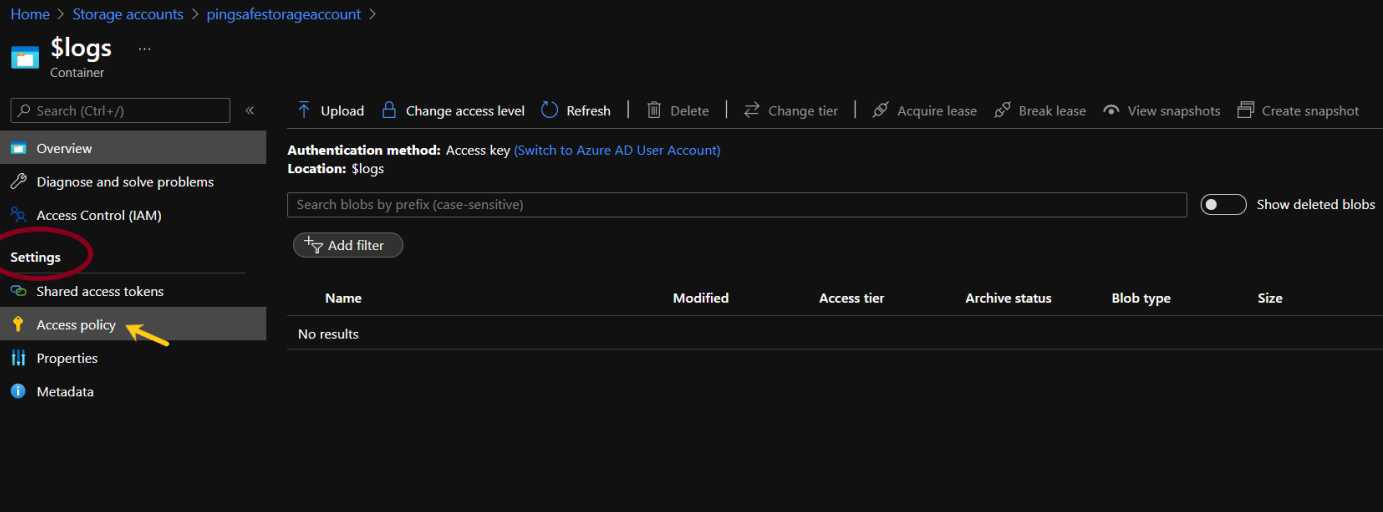
- If there is no policy configured under Immutable blob storage, go to Steps for Remediation section.
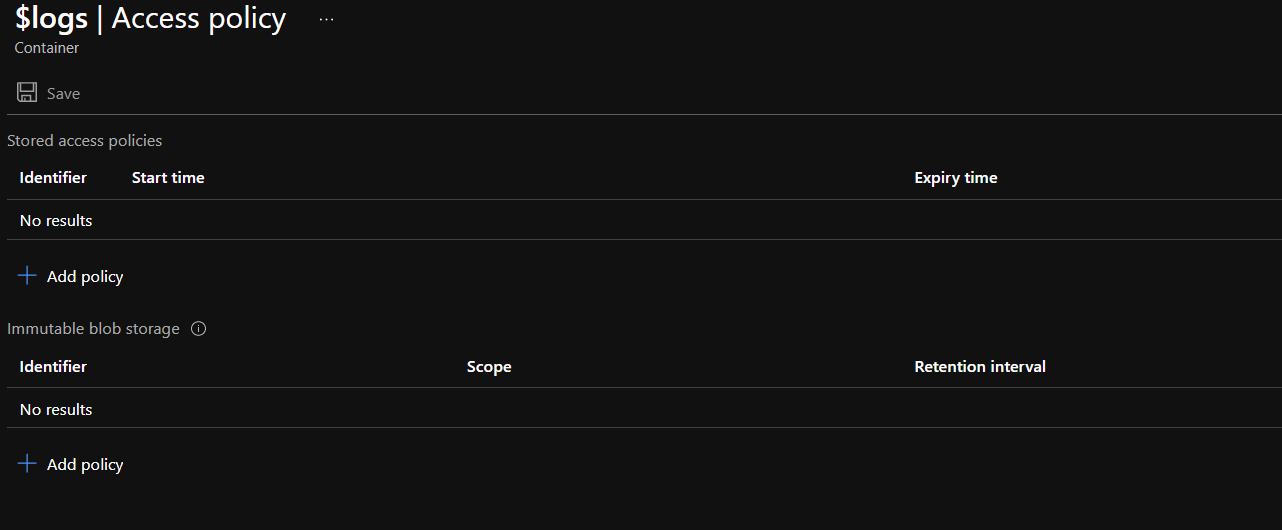
Steps for Remediation
- Log in to the Azure portal.
- Click on Storage accounts for Services.

- Select any one of the provided accounts to check for the policy.

- From the navigation bar, select Containers from Data storage.

- Select a container from the provided list.

- From the navigation pane select Access policy under Settings.

- If there is no policy configured under Immutable blob storage, click on +Add Policy.
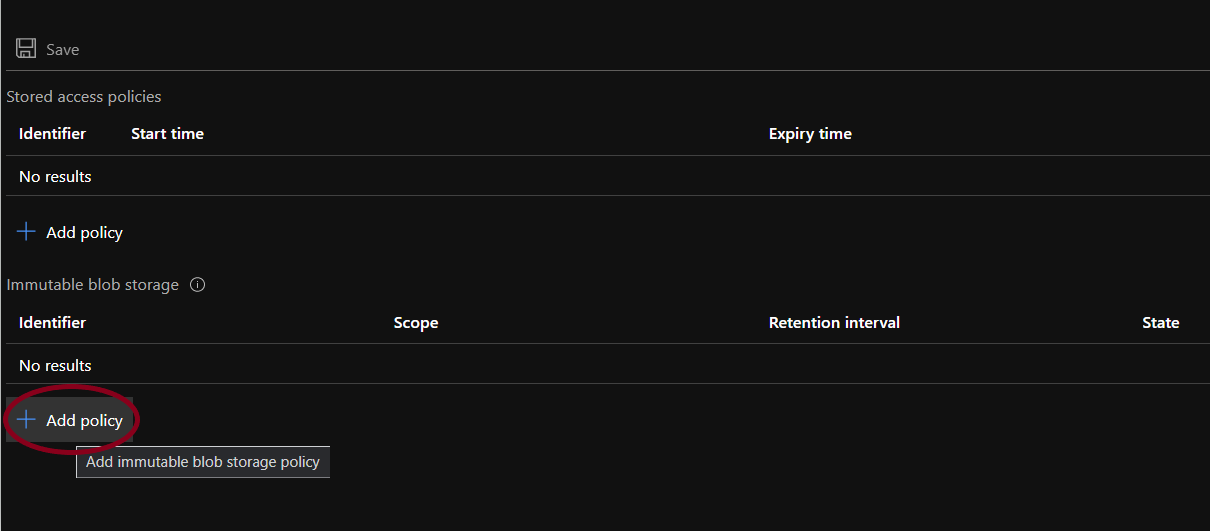
- There are two policy types for the immutability of blob storage. One is time-based and the other is policy-based. Both the policies can be defined for a container if the user wishes to do so.
- Time-based Retention Policy:
- To apply a time-based retention move to policy type and click on Time-based retention. Under Set retention period for: mention the number of days (between 1 to 146000 days) for retention. Click on OK.
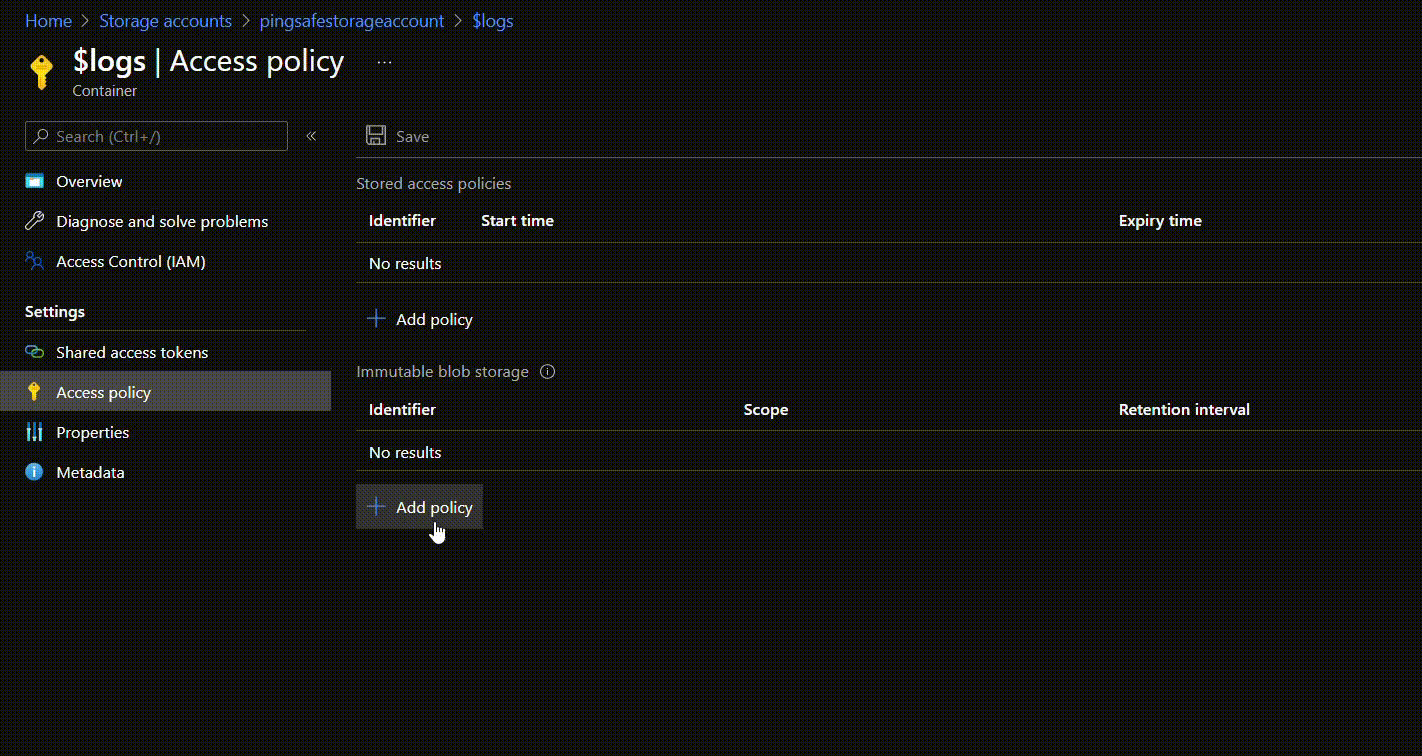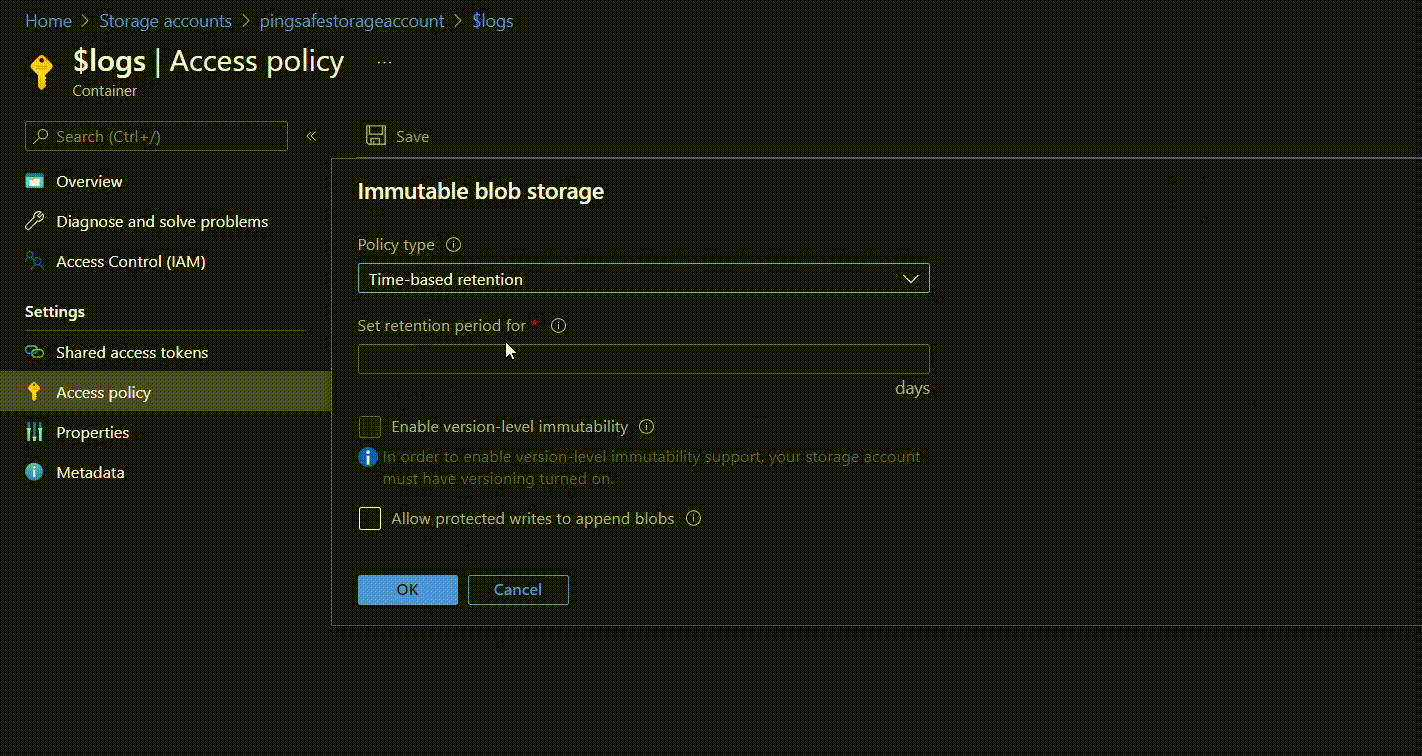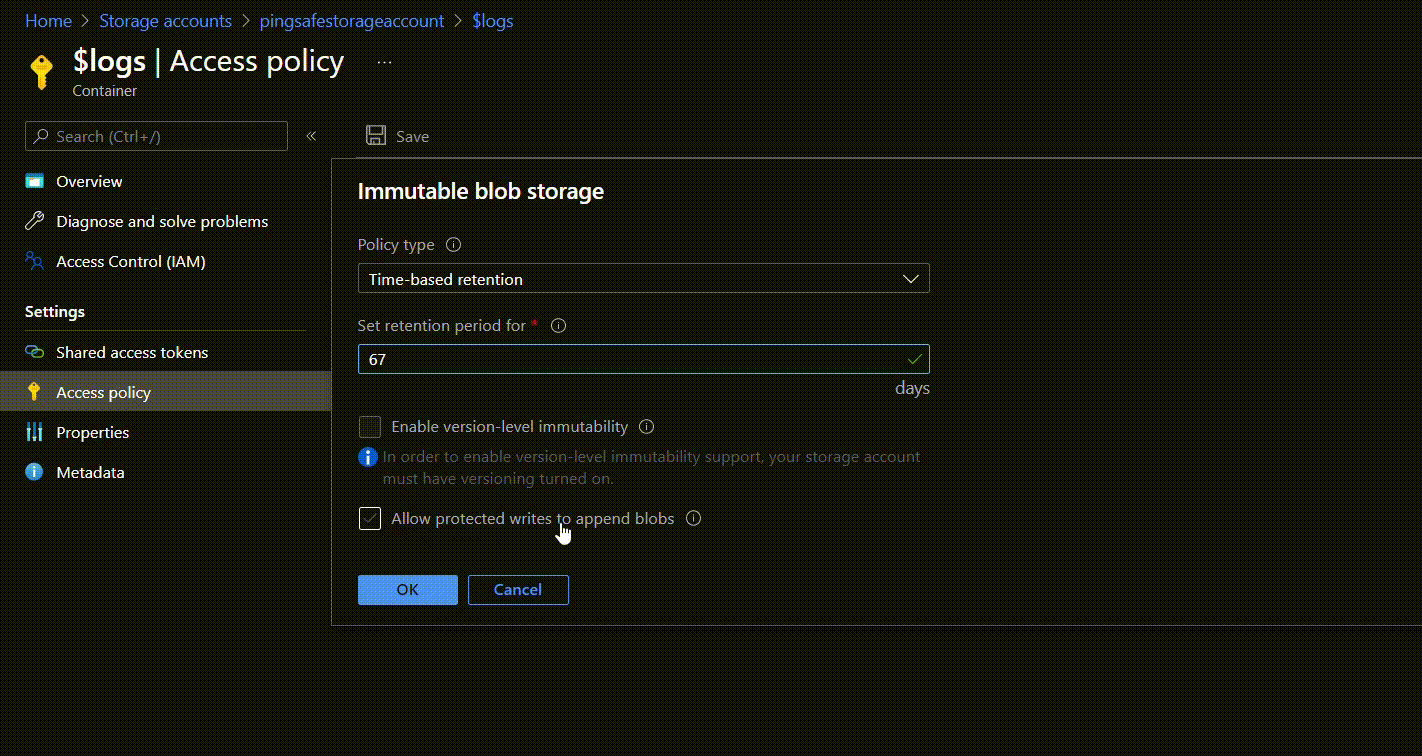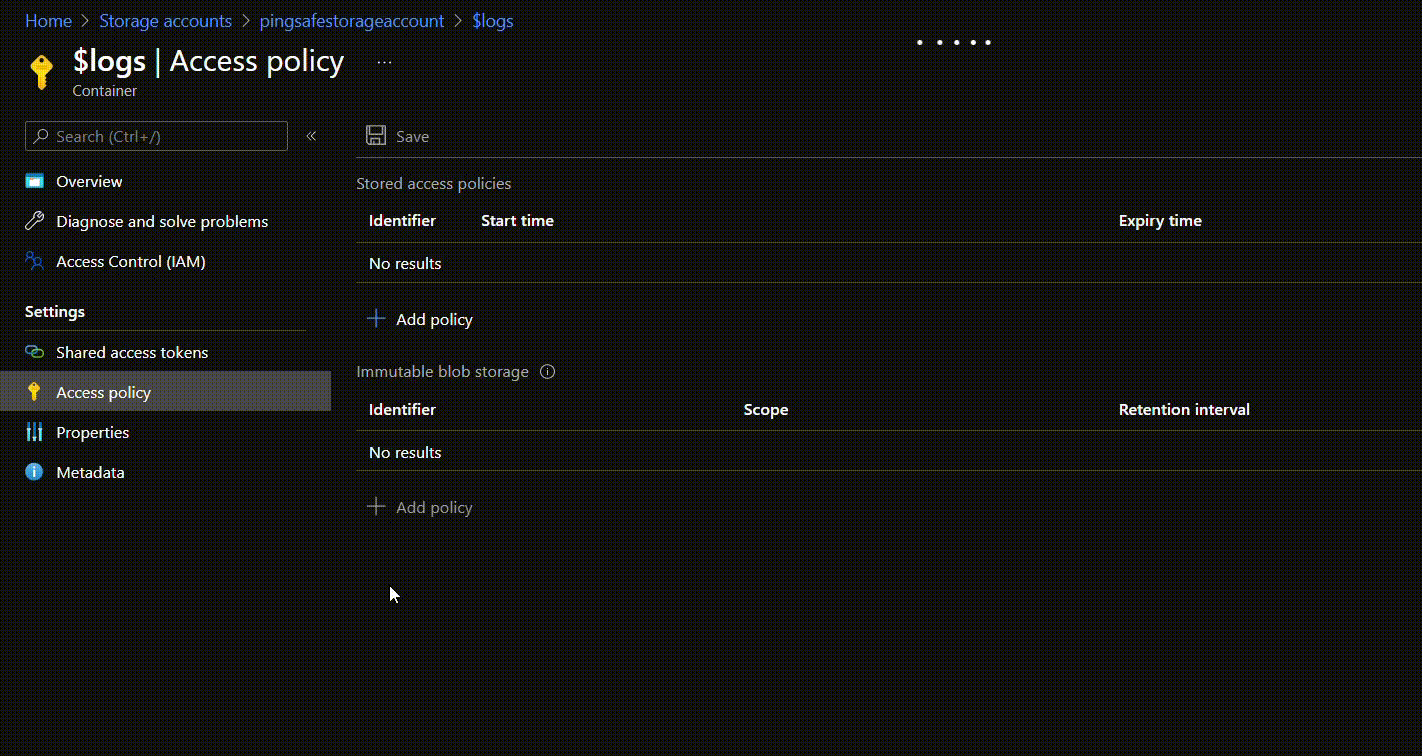
- Once the policy is created, users can first check the suitability of the policy and if required can edit or delete it. Once the user is sure they can lock the policy. This will ensure that the policy does not get edited or deleted in the future. To lock the policy, click on the options given at the rightmost side of the ribbon and select Lock policy. Type “yes” in the given field and click on OK.
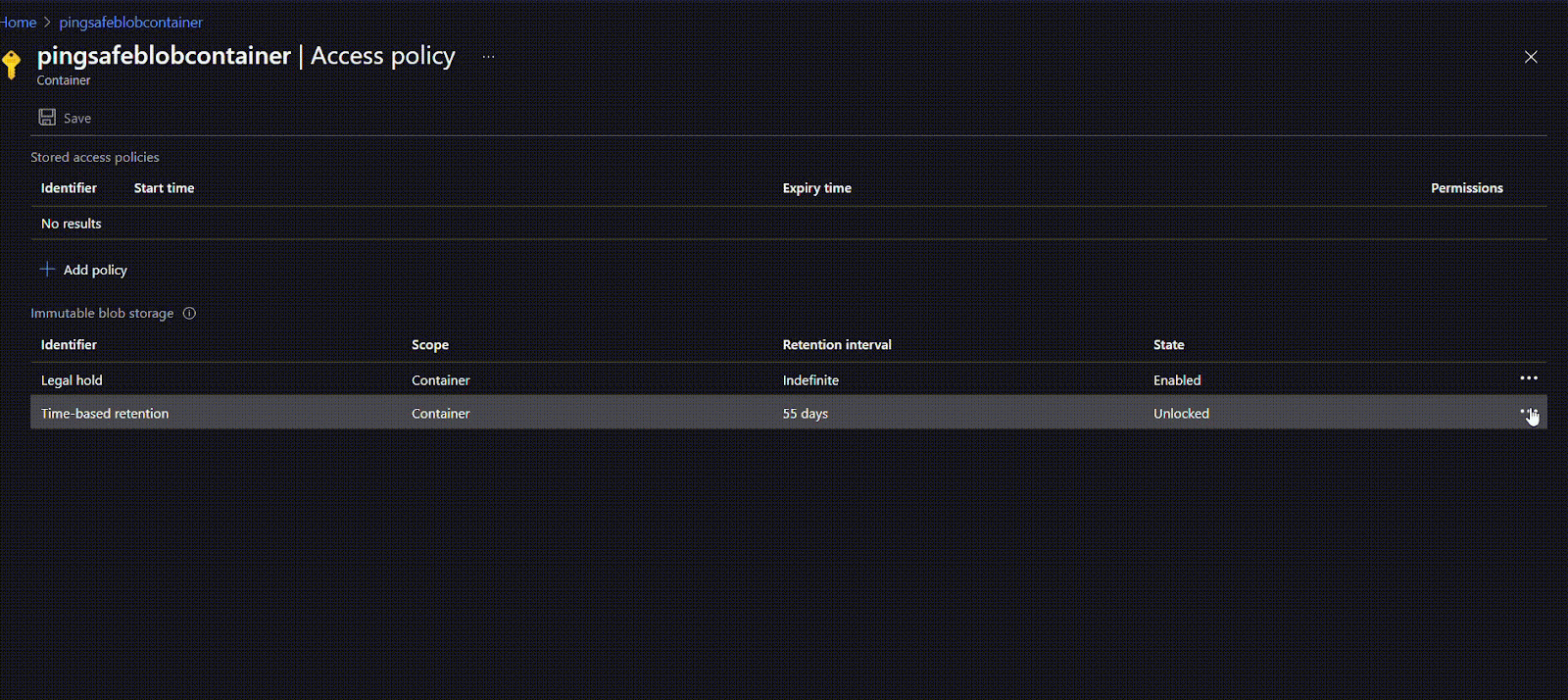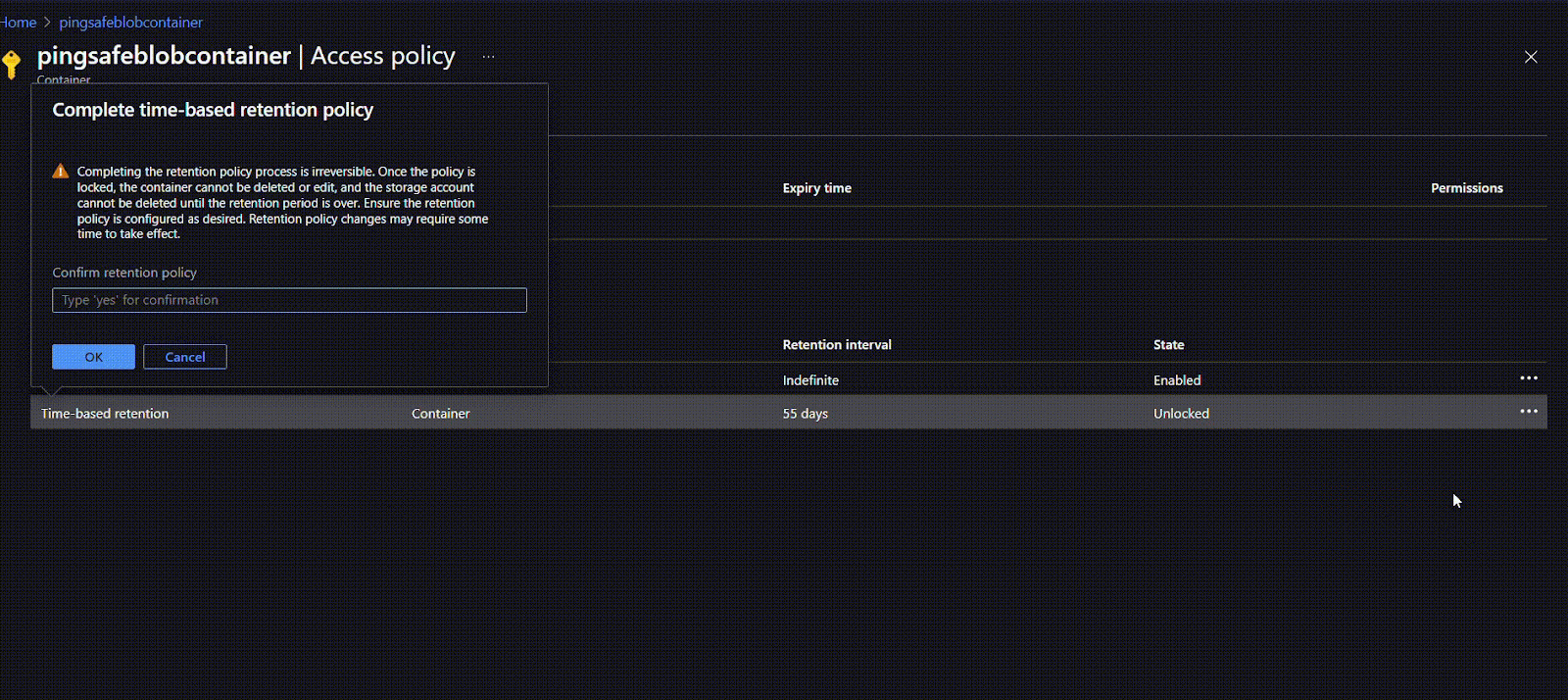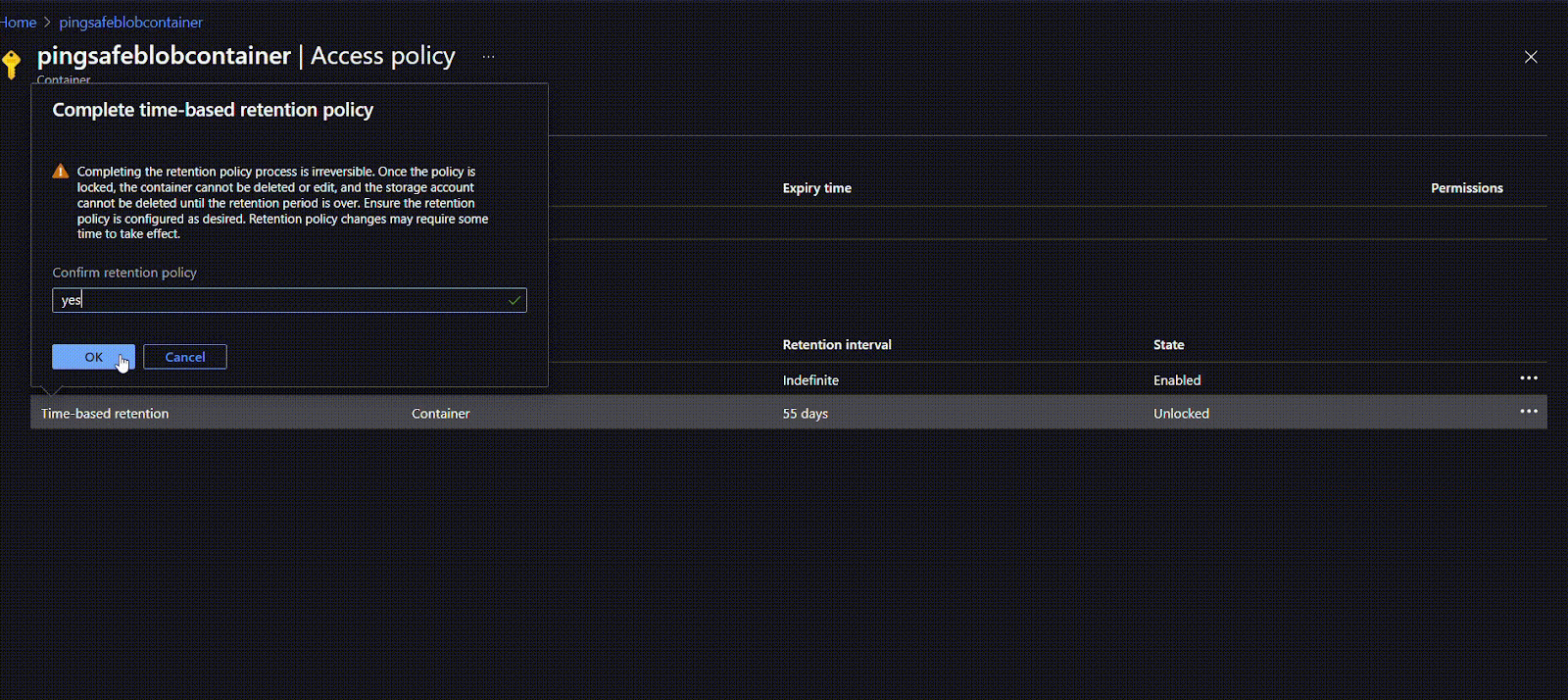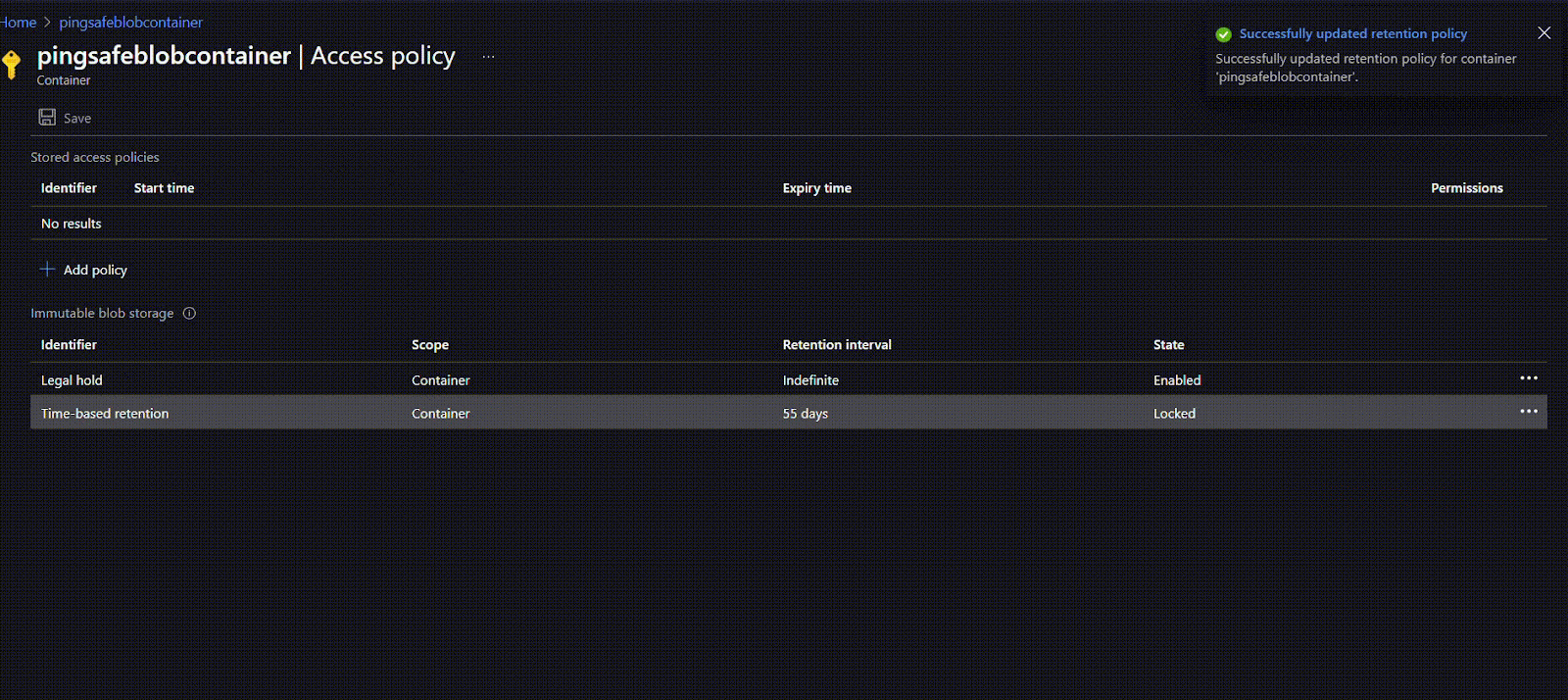
- To apply a time-based retention move to policy type and click on Time-based retention. Under Set retention period for: mention the number of days (between 1 to 146000 days) for retention. Click on OK.
- Policy-based Retention Policy
- For policy-based retention, click on Add policy. Enter the tag name or identifier in the given input field under Tag. Click on OK.

- For policy-based retention, click on Add policy. Enter the tag name or identifier in the given input field under Tag. Click on OK.
Please feel free to reach out to support@pingsafe.ai with any questions that you may have.
Thanks
PingSafe Support