CosmosDB Public Access Enabled
Risk Level: High
Description
This plugin ensures that Microsoft Azure CosmosDB accounts are configured to deny public access. Microsoft Azure CosmosDB accounts should not be accessible from the internet and only be accessed from within a VNET.
About the Service
Azure Cosmos DB: Azure Cosmos DB is a fully managed NoSQL database service for application developments. It provides single-digit millisecond response time and ensures full-time availability of the database.
Impact
In case the CosmosDB public access is disabled anyone from the internet can access the Azure CosmosDB account leading to compromise of confidentiality, integrity and thus availability of the application’s data. This can have serious consequences for your organization’s reputation and growth.
Steps to Reproduce
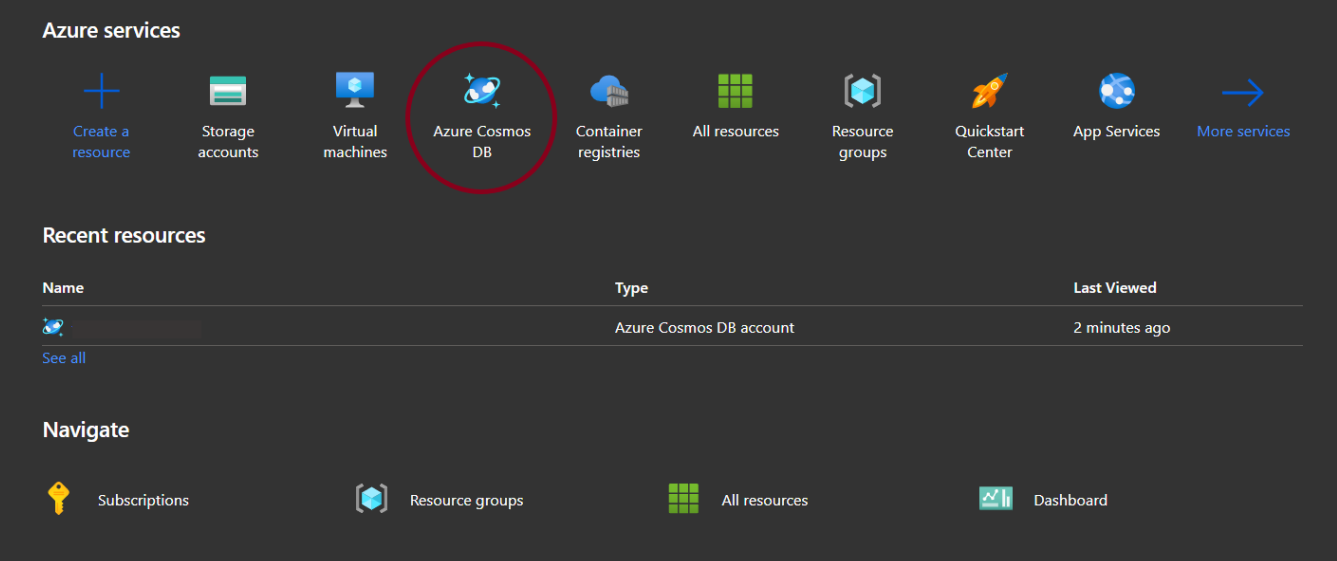
- Login to azure portal.
- Click on Azure Cosmos DB under Azure services.
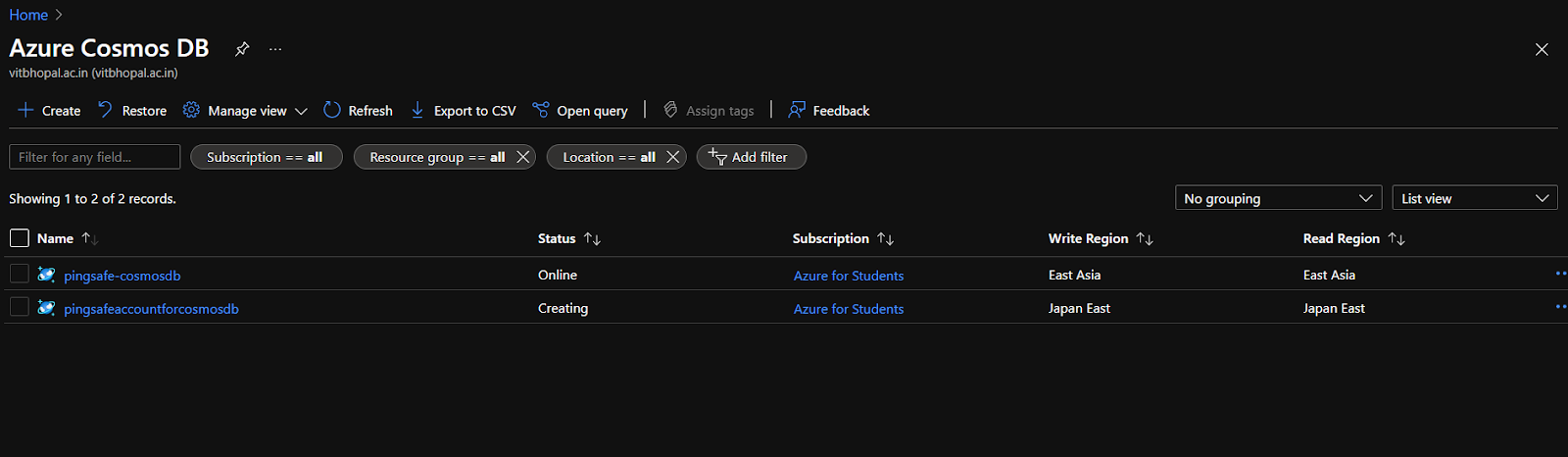
- Select an account for which the issue has to be detected.
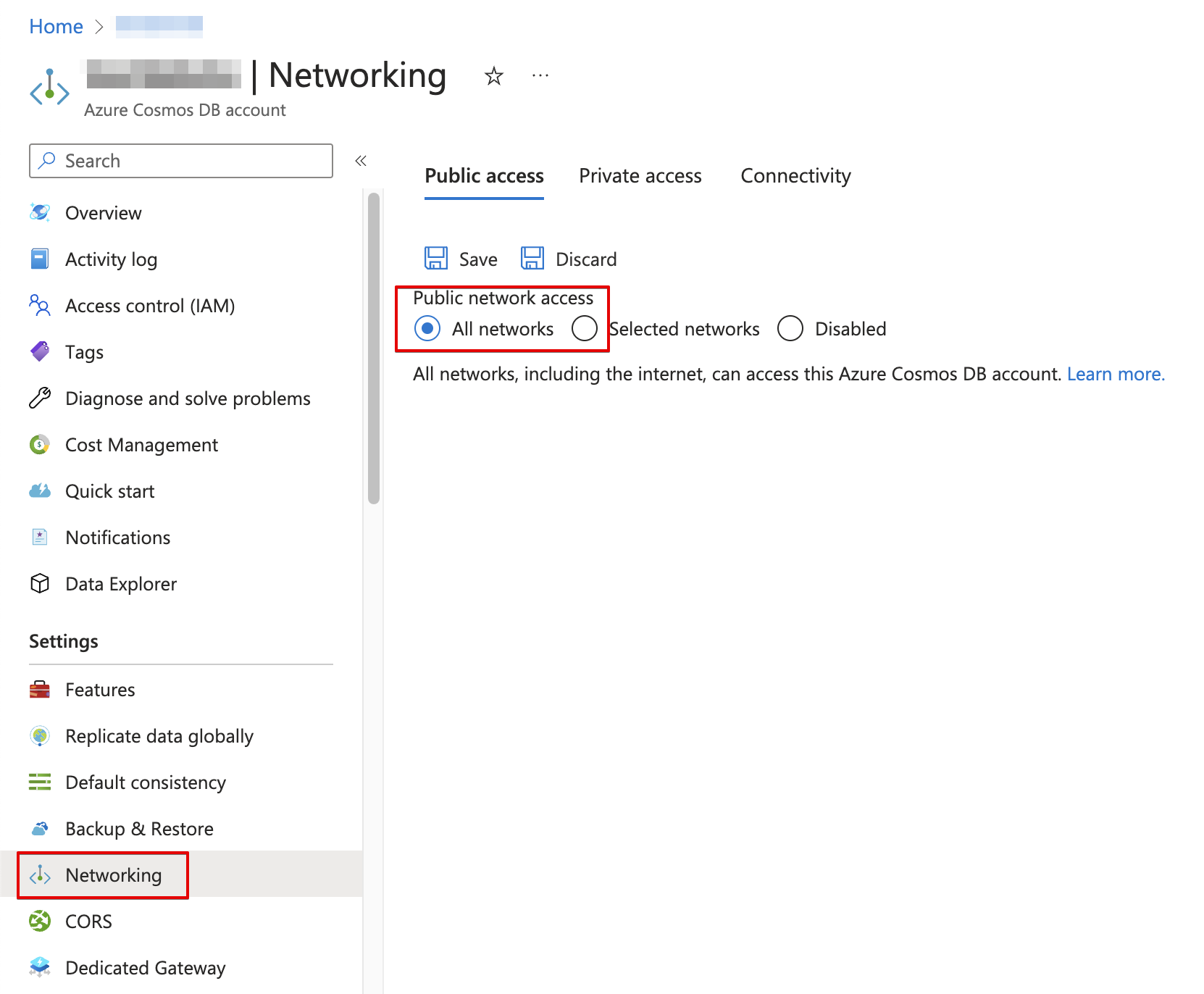
- Click on Networking under the Settings section.
- If the Public network access is set to ‘All networks’, go to the Steps to remediation section to remediate the problem.
- Repeat the process for other accounts as well.
Steps for Remediation
- Login to azure portal.
- Click on Azure Cosmos DB under Azure services.

- Select an account for which issue has to be resolved.

- Click on Networking under the Settings section.
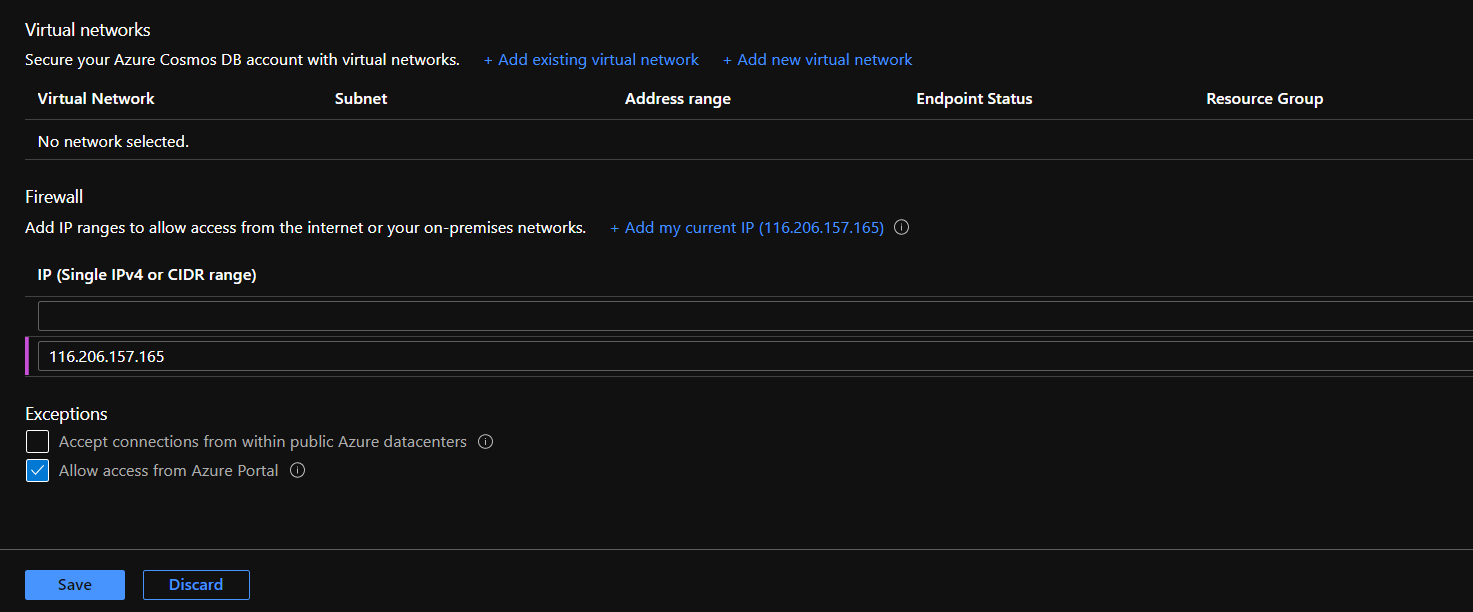
- If the Allow access from is set to ‘All networks’, click on ‘Selected networks’.

- Click on Add existing virtual network and Add new virtual network as per requirement under Virtual networks. And configure IP whitelisting under Firewall. Select Exceptions value as required for the organization. Click on Save.
- Repeat the process for other accounts as well.
Please feel free to reach out to support@pingsafe.ai with any questions that you may have.
Thanks
PingSafe Support