Open Hadoop HDFS NameNode Metadata Service
Risk Level: High
Description:
This plugin determines if the TCP or UDP port 53 for DNS (Domain Name Server) is open to the public. Unlike HTTP and HTTPS, which can be available to public access, port 53 of the DNS must be restricted to known IP addresses. Domain Name Service uses Port 53 of TCP/UDP during DNS resolution (DNS lookup) when the requests are sent between DNS clients and servers. To minimize false positives, this plugin reports only those firewalls with public IP associated with any of its networks.
About the Service :
DigitalOcean Firewall:
DigitalOcean Cloud Firewalls are an organization-based, stateful firewall administration for Droplets given at no extra expense. Cloud firewalls block all traffic that isn't explicitly allowed by a standard. Firewalls place an obstruction between your servers and different machines in the organization to safeguard them from outer assaults. Firewalls can behave based, which are designed on a for every waiter premise utilizing administrations like IPTables or UFW. Others, such as DigitalOcean Cloud Firewalls, are network-based and stop traffic at the organization layer before it arrives at the server.
Impact :
Firewalls for the droplets are used to control the incoming and outgoing traffic. There are rules defined under firewalls that can allow specific IP addresses to access the droplets with the protocol and the Ports specified. A misconfigured DNS server can result in increased opportunities for malicious activities such as Distributed Denial of Service (DDoS) attacks. Attackers can use publicly accessible open DNS servers and flood the target systems with DNS response traffic.
Steps to Reproduce :
- Login to the digital ocean console.
- Select Networking under the MANAGE section.
- Switch to the Firewalls tab.
- Select a firewall from the given lists.

- Check under Inbound Rules and/or Outbound Rules, if the Type is set to All TCP/custom, Protocol as TCP and Port Range includes either All ports or port 8020, visit the Steps for Remediation section.
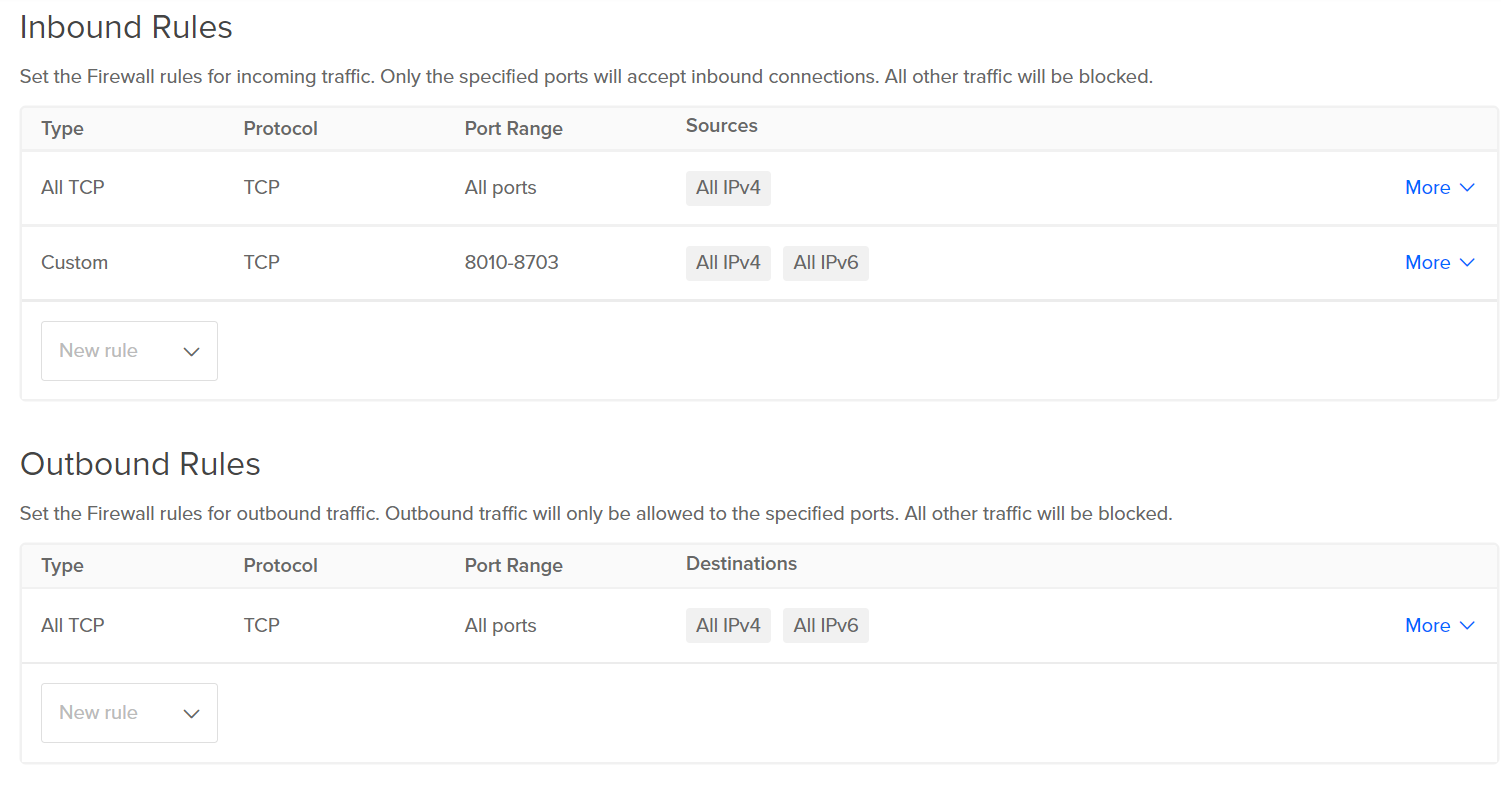
- Repeat the process for other firewalls with open Hadoop Metadata service as well.
Steps for Remediation :
- Login to the digital ocean console.
- Select Networking under the MANAGE section.

- Switch to the Firewalls tab.

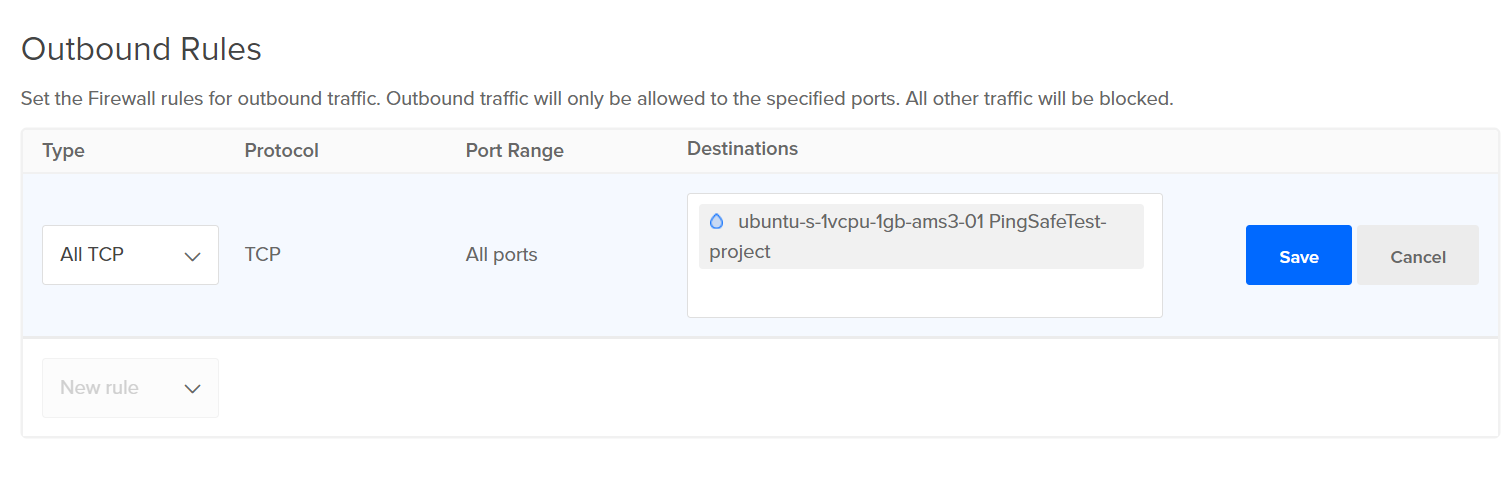
- Select a firewall from the given lists.

- Check under Inbound Rules and/or Outbound Rules, if the Type is set to All TCP/custom, Protocol as TCP and Port Range includes either All ports or port 8020, we will have to change the source and destination for the port to enhance security.

- Select the rule in which port 8020 is open to all source or destination by clicking on More, click on Edit Rule.
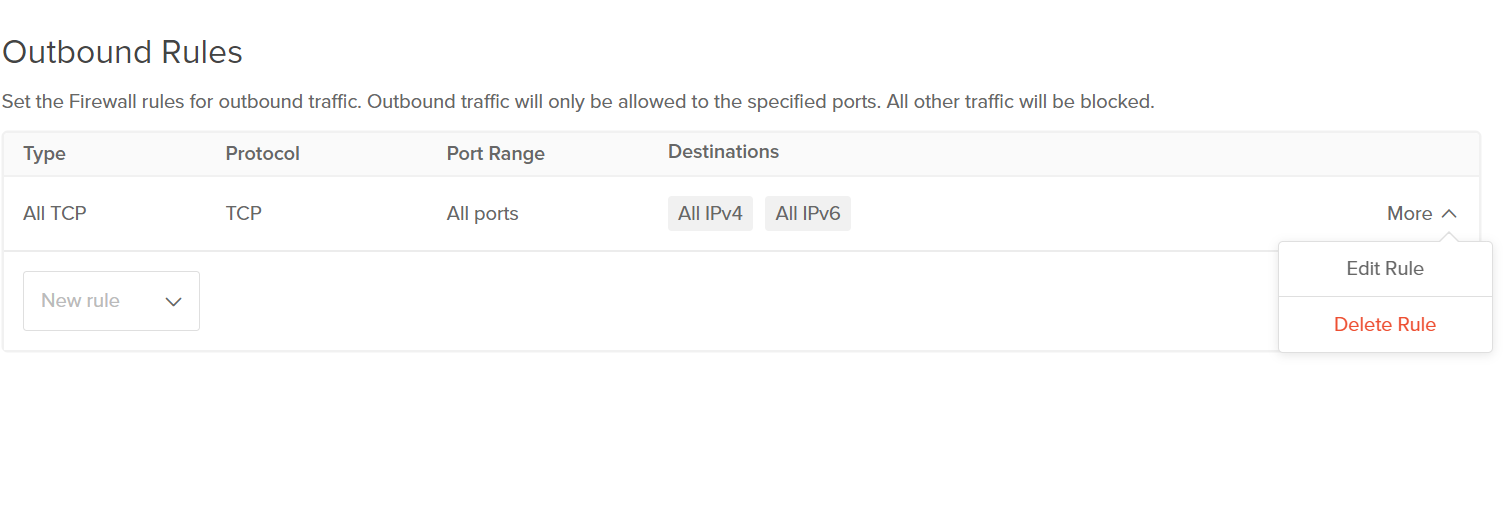
- Under Sources remove All IPv4 and All IPv6 options, add the eligible source (in Inbound Rules) / destination (in Outbound Rules) IP address and click on Save.
- Repeat the process for other open hadoop metadata service as well.