SSM Parameters Poorly Encrypted
Risk Level: Low
Description:
This plugin guarantees that SSM parameters are encrypted to the specified degree of encryption. SSM parameter values are encrypted to allow them to be utilised by permitted systems while prohibiting access to other account users.
PingSafe strongly recommends recreating SSM Parameters with Type set to SecureString and encrypting with KMS key of configured type.
Configuration Parameters
SSM Minimum Encryption Level: This parameter denotes minimum level of encryption the SSM must-have. The values it can have are (lowest to highest): awskms=AWS-managed KMS; awscmk=Customer managed KMS; externalcmk=Customer managed externally sourced KMS; cloudhsm=Customer managed CloudHSM sourced KMS. An alert will be generated if the found level is less than the specified threshold.
By default, the threshold is set to ‘awskms’. Therefore, issues will be generated for SSM without KMS encryption enabled.
About the Service :
AWS Systems Manager or SSM is an AWS service that allows you to manage and see your AWS infrastructure. You may examine operational data from numerous AWS services and automate operational operations across your AWS resources using the Systems Manager UI. By monitoring your managed instances and reporting on (or taking remedial action on) any policy breaches it identifies, the Systems Manager assists you in maintaining security and compliance.
Impact :
You may segregate secrets and configuration data from code and typical administrative activities with encrypted AWS SSM parameters, ensuring that only allowed users have access to the protected parameter values.
Steps to reproduce :
- Log in to your AWS Management Console.
https://ap-south-1.console.aws.amazon.com/console/ - Navigate to the SSM dashboard.
https://ap-south-1.console.aws.amazon.com/systems-manager/
- Next, move to Parameter Store under the Application Management.
- Choose the parameter that you want to examine and look at the Value, if it is set to String that means that the SSM parameter is poorly encrypted.
- Repeat the same procedure for other parameters as well.
Steps for remediation :
- Log in to your AWS Management Console.
https://ap-south-1.console.aws.amazon.com/console/ - Navigate to the SSM dashboard.
https://ap-south-1.console.aws.amazon.com/systems-manager/
- Next, move to Parameter Store under the Application Management.
- Choose the parameter that you want to examine and look at the Value, if it is set to String that means that the SSM parameter is poorly encrypted.
- Click on the parameter to recreate and copy the Name, Description and Value. Once the information is copied click on Delete and confirm the deletion.
- Next, click on Create Parameter to start the setup of encrypted SSM parameter.
- In the parameter details, enter the Name, Description and then select the Tier and set Type as SecureString. Next, enter the Value and click Create parameter.
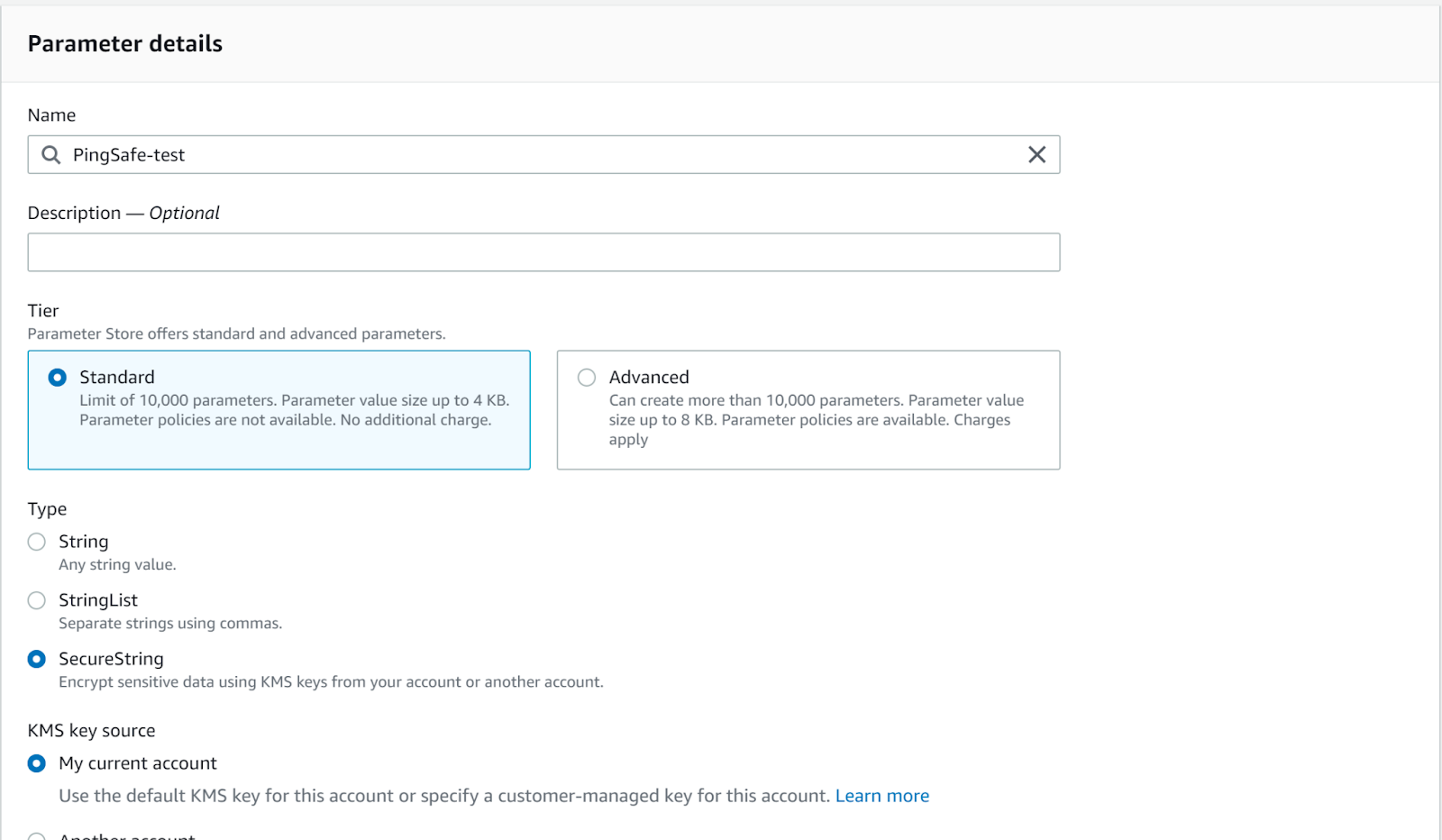
- Next enter the copied Name, Description and Value.
- Repeat the same procedure for other parameters as well.
References: