Access Keys Not Rotated
This plugin ensures access keys are not older than configured time in order to reduce accidental exposures.
Risk Level: MEDIUM
Description:
This plugin ensures access keys are not older than configured time in order to reduce accidental exposures. Access keys should be rotated frequently to avoid having them accidentally exposed.
SentinelOne CNS strongly recommends rotating an access key, first create a new key, replace the key and secret throughout your app or scripts, then set the previous key to disabled. Once you ensure that no services are broken, then fully delete the old key.
Configuration Parameters
Access Keys Rotated Threshold: The parameter determines the number of days after which the rotation of access keys is required. By default, the value is 730 days and if the keys are not rotated within the set duration an issue is generated.
About the Service :
AWS ID and Access Management (IAM) allows you to securely manage access to AWS services and resources. With IAM, AWS users and groups can be established and managed and permissions used to enable access by AWS resources and prohibit them.
We can discover and adjust the rules so that only the services are accessible. We can thus adhere better to the less privileged principle.
Impact :
If the access keys older than configured time are not rotated frequently this may cause accidental exposures. Accidental exposures of access keys can be lethal because they can result in compromises of access keys.
Steps to reproduce :
- Sign-in to AWS management console.
- Navigate to the “IAM” dashboard.
https://console.aws.amazon.com/iamv2/ - Select “Users” in the left navigation panel.
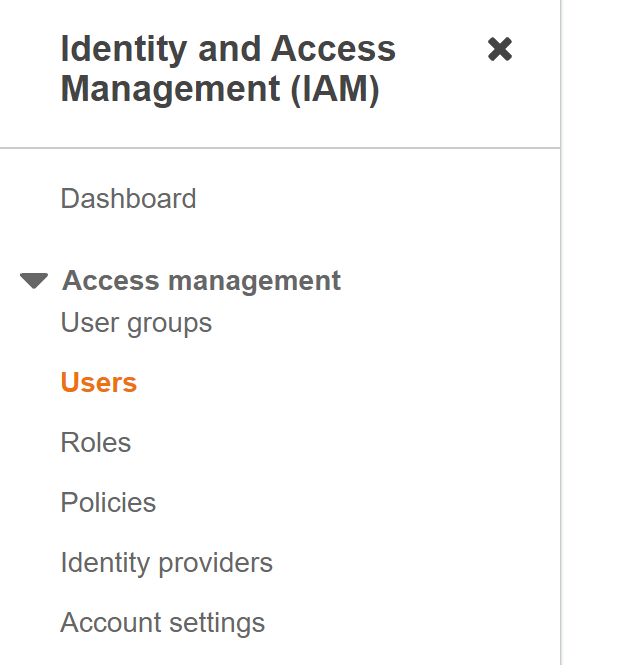
- Click on the User that you want to examine and select “Security Credentials”.
- In the “Created Column” check for any keys older than 100 days with the status “Active”. The users can also set the number of days.
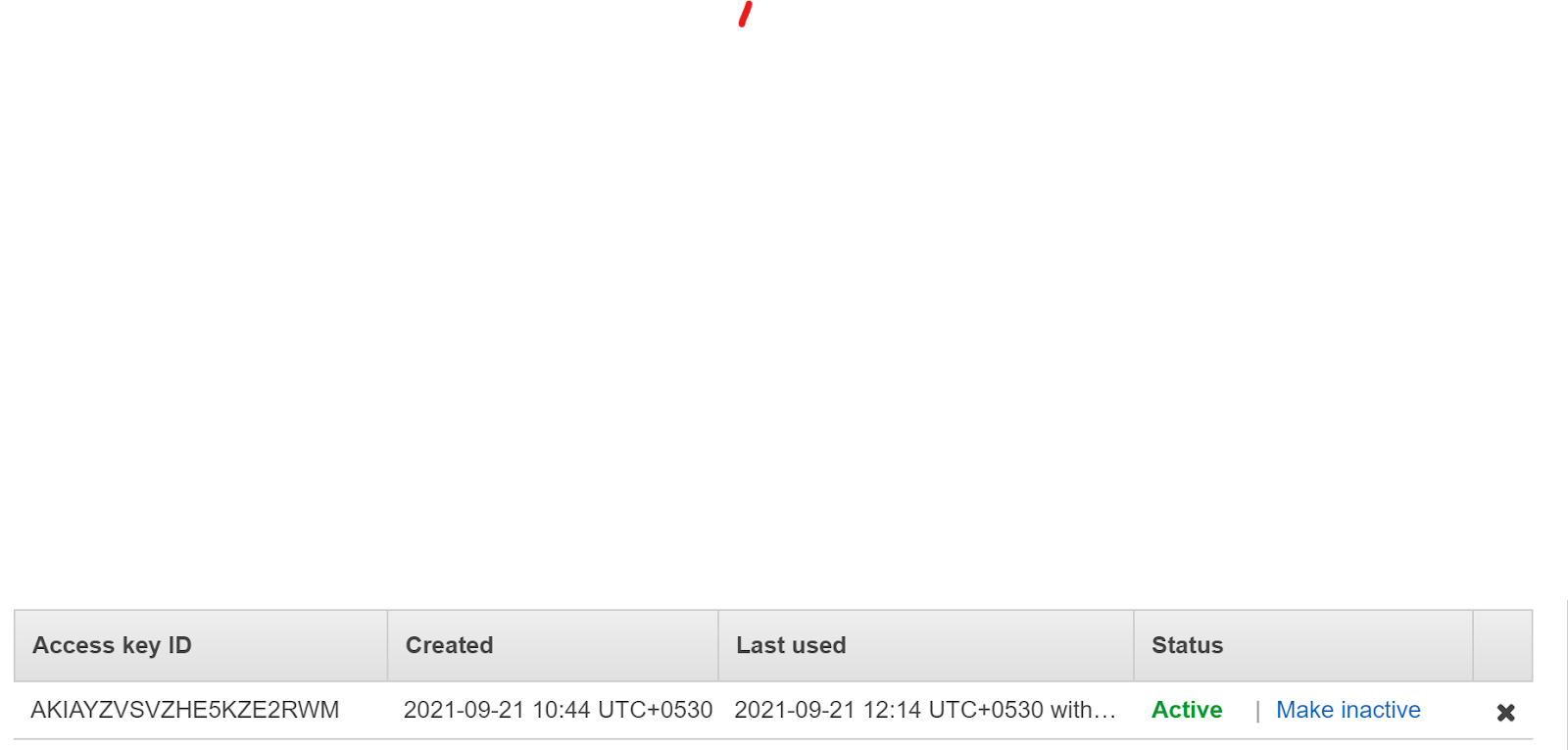
- If an Active key is older than 100 days, the key is outdated and needs to be changed.
Steps for remediation :
- Sign-in to AWS management console.
- Navigate to the “IAM” dashboard.
https://console.aws.amazon.com/iamv2/ - Select “Users” in the left navigation panel.

- Click on the User that you want to examine and select “Security Credentials”.
- Click “Create Access Key” to create a new set of access keys that will replace the old one.
- In the Create Access Key dialogue box click “Download Credentials” to save the newly created access key ID and secret access key to a CSV file on your system.
- Click Close to close the dialog box, then update the existing access key ID and secret access key with the new ones.
- Return to the Configuration page and “Make Inactive” the outdated access key.
- After the key has become Inactive, delete the key.
References: