Amazon GuardDuty Master Account Missing
This plugin ensures Amazon GuardDuty master account is configured.
Risk Level: Low
Description
This plugin ensures Amazon GuardDuty master account is configured. SentinelOne CNS recommends organizations with large numbers of AWS accounts should configure GuardDuty Master Account so that findings from all member accounts are sent to a consistent master account. GuradDuty provides a detailed analysis of various AWS data sources and potential security risks. Unauthorized API calls from malicious IP addresses can also be monitored with GuardDuty.
About the Service
Amazon GuradDuty: It provides intelligent threat detection for your AWS Accounts. With regular scans, it monitors your AWS account and workloads to provide detailed findings of potential security threats and remediation.
Amazon GuardDuty threat detection which can be broadly classified into - account compromise, instance compromise, malicious reconnaissance, and bucket compromise. GuardDuty delivers more accurate findings using machine learning to filter out lists of malicious IPs and domains.
All the findings can be generated with just a few clicks by enabling the Amazon GuardDuty detector.
Impact
Amazon GuardDuty generates findings related to potential security threats. They can range from unprotected ports, possible brute force SSH attacks to API operations invoked by malicious IP addresses. Such findings are extremely important to secure the AWS infrastructure from potential attacks related to aforementioned threats.
Organizations with a large number of accounts can have these findings scattered across individual accounts and thus, managing them becomes difficult.
It is recommended that all the findings are passed on to the master account. Therefore, none of the important threats can be missed.
Steps to Reproduce
Using AWS Console-
- Log In to the AWS Console of the Master Account.
- Open the Amazon GuardDuty Console. You can use this link (https://console.aws.amazon.com/guardduty) to navigate directly if already logged in.
- The Findings page is displayed. Click on Account from the left panel.
- From the list of added accounts, find the account ID of your account. If it is not present, GuardDuty is not sending findings to the Master Account. Also, the Status must be ENABLED
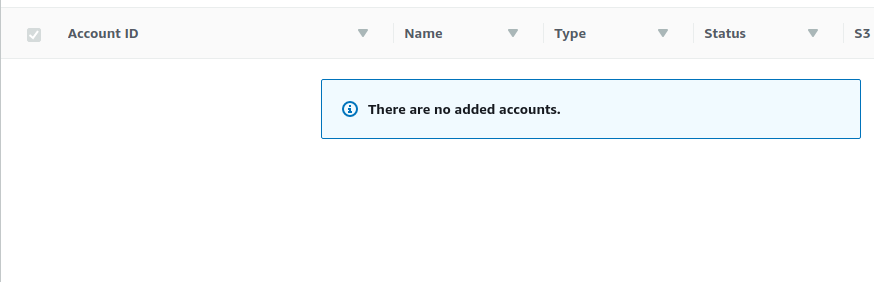
- Repeat steps 3 to 4 for all the AWS accounts you want to investigate.
Steps for Remediation
Add the member accounts from the master account by sending invitations using Amazon GuardDuty and enable them.
- Log In to the AWS Console of the Master Account.
- Open the Amazon GuardDuty Console. You can use this link (https://console.aws.amazon.com/guardduty) to navigate directly if already logged in.
- The Findings page is displayed. Click on Account from the left panel.

- Click on Add Accounts to send invitations to member accounts.
- Enter the Account ID and the email address of the member accounts. Alternatively, you can also upload a .csv file.
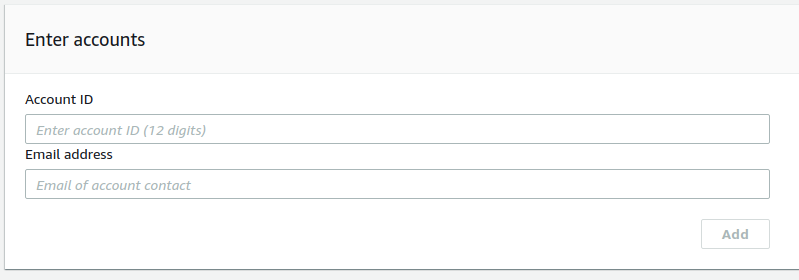
- Review the list of accounts, and click on next to send the invitations.
- Repeat steps 3 to 6 to invite all the AWS accounts from the master account.