AWS Glue CloudWatch Logs Not Encrypted
This plugin ensures that encryption at-rest is enabled when writing AWS Glue logs to Amazon CloudWatch.
Risk Level: Medium
Description
This plugin ensures that encryption at-rest is enabled when writing AWS Glue logs to Amazon CloudWatch. AWS Glue security configurations should have encryption at-rest enabled for AWS Glue logs. CloudWatch Logs encryption mode encrypts the AWS Glue logs with Server-side (SSE-KMS) before it is sent to CloudWatch.
About the Service
AWS Glue: AWS Glue makes the process of data integration easier. The complete process of data extraction, enriching, cleaning and combining is done by AWS Glue. The integrated information can then be used to perform various analytics, machine learning, and application development operations. With AWS Data Catalog, users can easily search across various datasets at a single platform.
Impact
AWS Glue is integrated with AWS CloudTrail which enables continuous delivery of CloudTrail events to Amazon CloudWatch Logs, and Amazon CloudWatch Events.
Since every log event has critical information on who made the request, it must be encrypted before storing.
This prevents data from being misused by any attacker.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the AWS Glue Console. You can use this link (https://console.aws.amazon.com/glue) to navigate directly if already logged in.
- Scroll down and select Security Configurations from the left pane.
- From the list of configurations, look up for the CloudWatch logs encryption mode column. If the value is set to “DISABLED”, the encryption is disabled for the configuration.
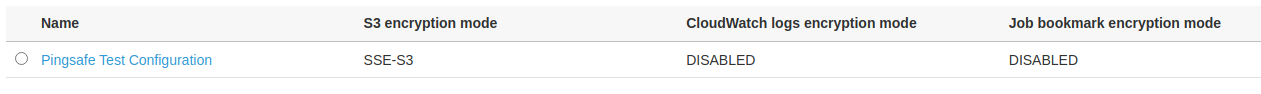
- Repeat steps 3 to 4 for all the configurations you want to investigate.
Steps for Remediation
Recreate Glue Security Configurations and enable CloudWatch logs encryption at-rest.
- Log In to your AWS Console.
- Open the AWS Glue Console. You can use this link (https://console.aws.amazon.com/glue) to navigate directly if already logged in.
- Scroll down and select Security Configurations from the left pane.

- From the list of configurations, look up for the CloudWatch logs encryption column. If the value is set to “DISABLED”, the encryption is disabled for the configuration. Select the configuration with the radio button beside it and click on Delete.
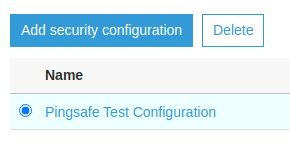
- Confirm the delete operation when asked in the Popup.
- From the Home Screen, click on Add Security Configuration. Type the same name you deleted before.
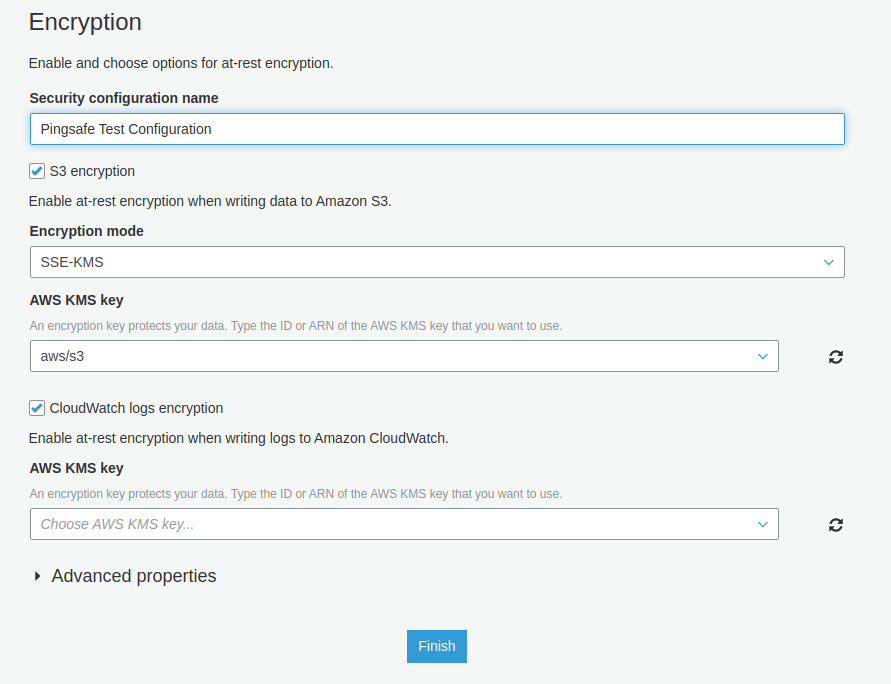
- Check the CloudWatch logs encryption option. After checking it, you will find an option to Choose AWS KMS key for encryption. Either choose one from the options or type the key ARN.
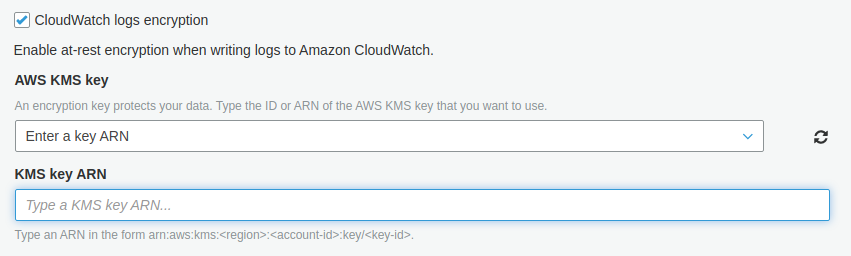
- Click on Finish after completing the configuration.
- Repeat steps 3 to 8 for all the vulnerable configurations.