AWS Glue S3 Encryption Disabled
This plugin ensures that encryption at-rest is enabled when writing AWS Glue data to Amazon S3.
Risk Level: Medium
Description
This plugin ensures that encryption at-rest is enabled when writing AWS Glue data to Amazon S3. AWS Glue should have encryption at-rest enabled for Amazon S3. While writing Amazon S3 data, encryption is done either using S3 managed keys (SSE-S3) or with AWS KMS managed keys (SSE-KMS). By default, SentinelOne CNS checks for the SSE-KMS level of encryption.
Configuration Parameters
Glue S3 Encryption Level : The parameter allows users to input the lowest encryption level of key that can be used by the organization for S3 bucket. In case, a key has been generated and it is lower than the Encryption level mentioned an issue will be generated.
The default value is set to AWS kms i.e. AWS key management service which has the lowest level of Encryption and is not recommended.
About the Service
AWS Glue: AWS Glue makes the process of data integration easier. The complete process of data extraction, enriching, cleaning and combining is done by AWS Glue. The integrated information can then be used to perform various analytics, machine learning, and application development operations. With AWS Data Catalog, users can easily search across various datasets at a single platform.
Impact
SentinelOne CNS recommends, S3 encryption is enabled for AWS Glue configurations. Without S3 encryption, while running ETL (Extract Transform Load) jobs or starting public development points, the data can get accessed by anonymous attackers.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the AWS Glue Console. You can use this link (https://console.aws.amazon.com/glue) to navigate directly if already logged in.
- Scroll down and select Security Configurations from the left pane.
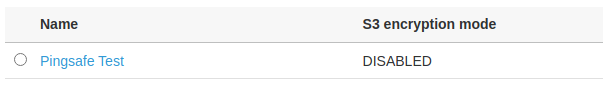
- From the list of configurations, look up for the S3 encryption mode column. If the value is set to “DISABLED”, the encryption is disabled for the configuration.
- Repeat steps 3 to 4 for all the configurations you want to investigate.
Steps for Remediation
Recreate AWS Glue Security Configuration and enable Amazon S3 encryption at-rest with KMS keys.
- Log In to your AWS Console.
- Open the AWS Glue Console. You can use this link (https://console.aws.amazon.com/glue) to navigate directly if already logged in.
- Scroll down and select Security Configurations from the left pane.

- From the list of configurations, look up for the S3 encryption mode column. If the value is set to “DISABLED”, the encryption is disabled for the configuration. Select the configuration with the radio button beside it and click on Delete.
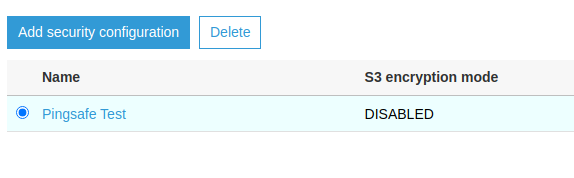
- Confirm the delete operation when asked in the Popup.
- From the Home Screen, click on Add Security Configuration. Type the same name you deleted before.
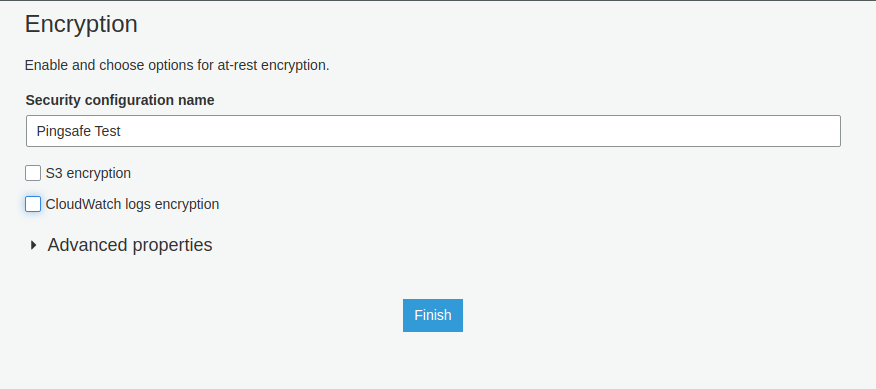
- Check the S3 encryption option. After checking it, you will find an option to select the Encryption Mode. Select SSE-KMS from the list. Also, add the KMS key from the drop down below. You can choose to type the key ARN alternatively.
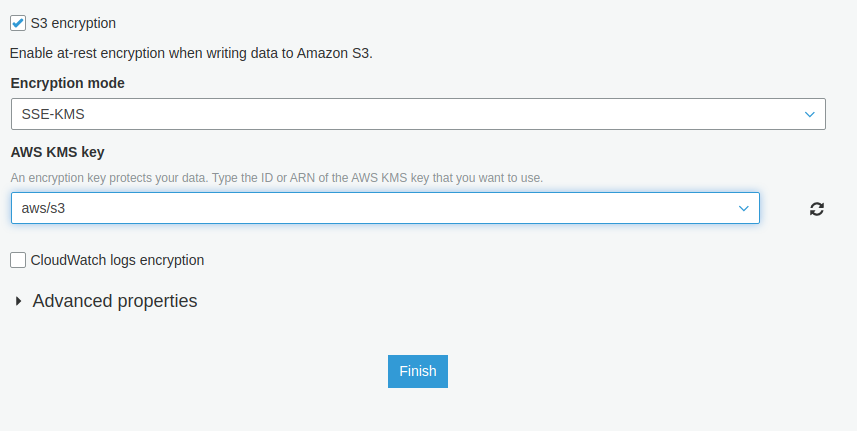
- Click on Finish after completing the configuration.
- Repeat steps 3 to 8 for all the vulnerable configurations.