Azure Container Registries With Admin User
Risk Level: High
Description
This plugin ensures that the admin user is not enabled on container registries. Azure Container Registries have an admin user that is designed for testing. This should be disabled by default to avoid sharing confidential admin credentials
About the Service
Container Registries: Container registries is Microsoft owned hosting platform for Docker images. It is a repository used to build, store and manage container images securely and efficiently. The container images help users to scale out the applications quickly and ship applications from one system to another.
Impact
If the admin user is enabled other employees will be able to docker login to container registries using the generated passwords. But, the sharing of passwords can give unauthenticated access to bad actors once they get hold of the auto-generated passwords.
Steps to Reproduce
- Login to azure portal.
- In services, select Container Registries.
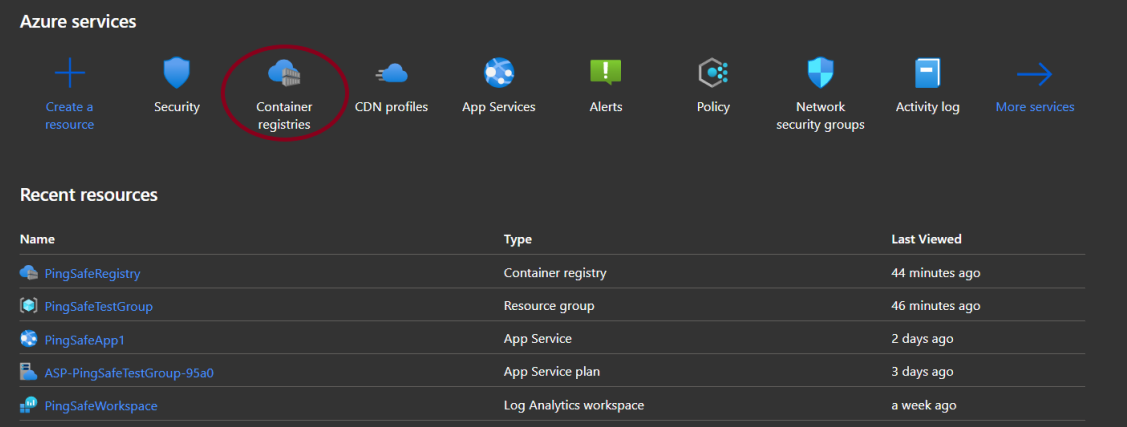
- The Container registries service will open, select the desired registry for which you want to check the error.
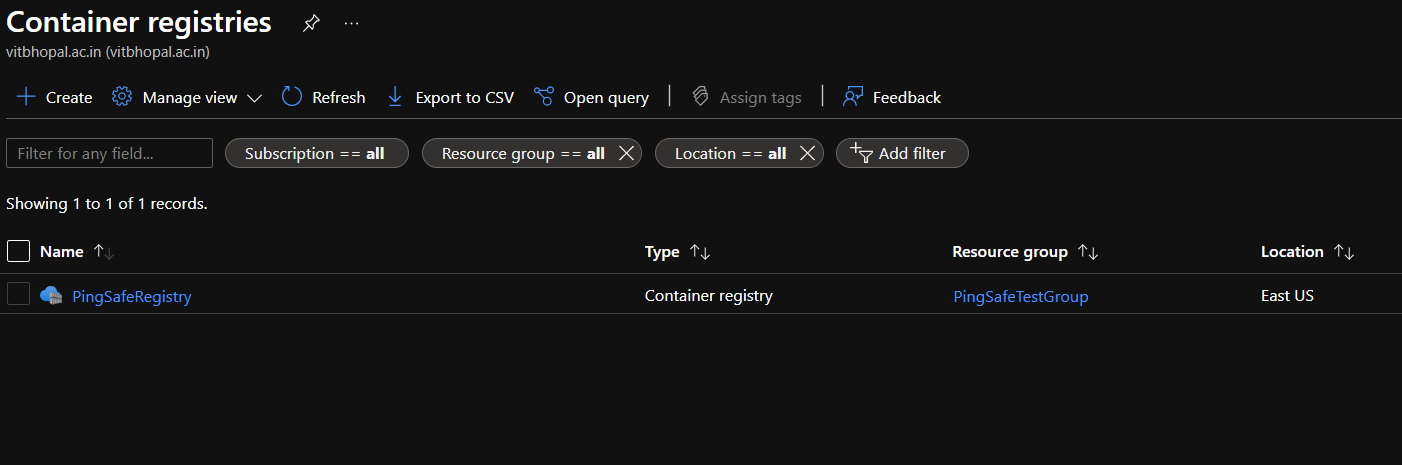
- In the Navigation section, Under Settings click on Access keys.
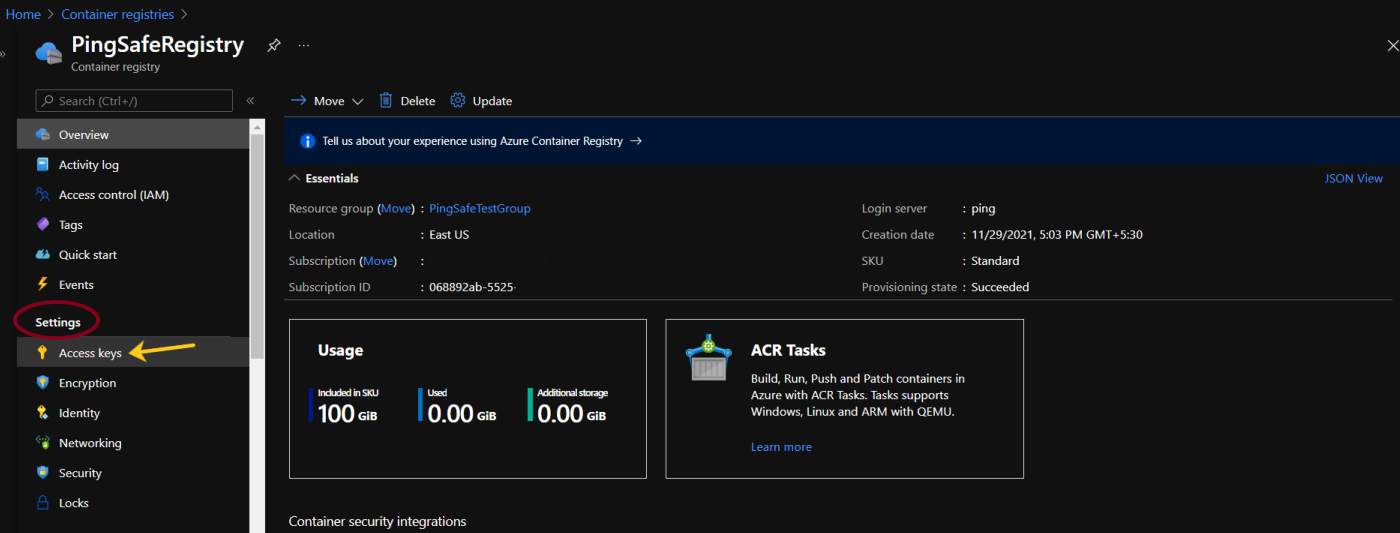
- If the Admin User button is set to Enabled, follow the Steps for Remediation.
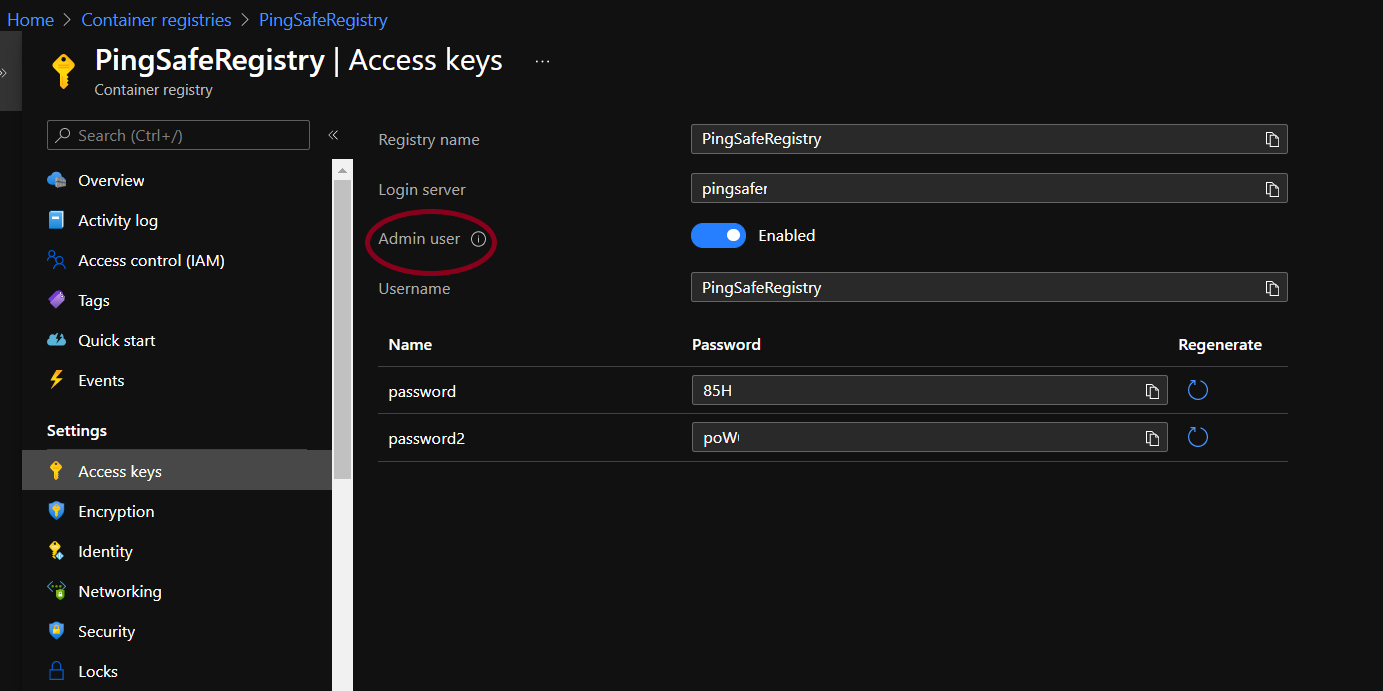
- Repeat the process for the rest of the registries.
Steps for Remediation
- Login to azure portal.
- In services, select Container Registries.

- The Container registries service will open, select the desired registry for which you want to eliminate the error.
- In the Navigation section, Under Settings click on Access keys.

- Click on the switch button in front of the Admin User option to disable admin user.
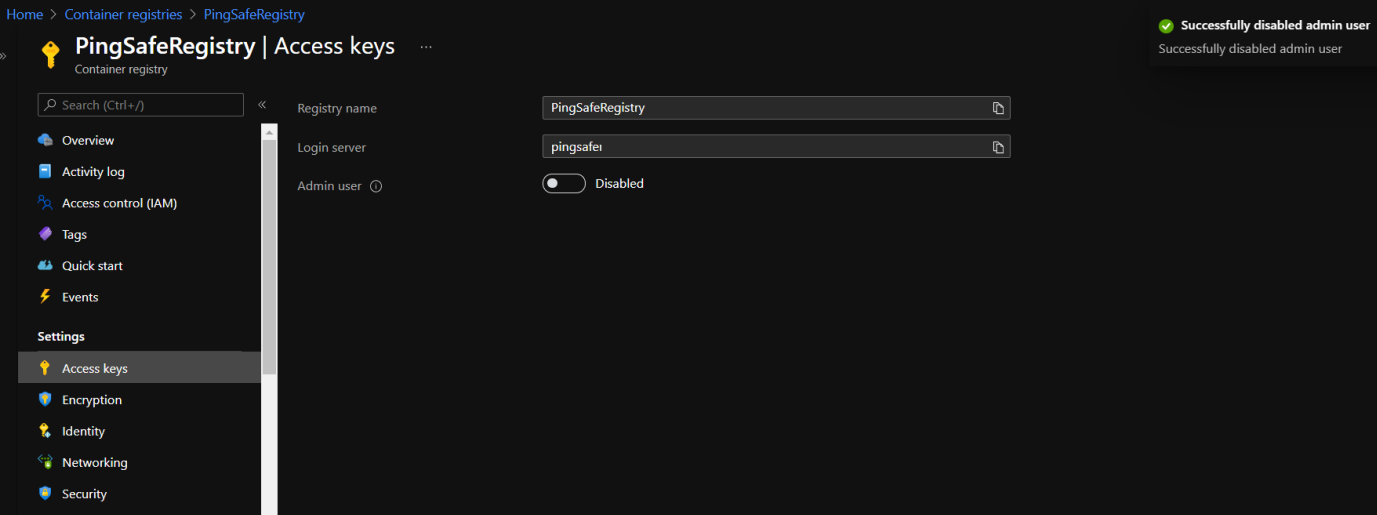
- Repeat this process for the rest of the registries.
Please feel free to reach out to support@pingsafe.com with any questions that you may have.
Thanks
PingSafe Support