CloudFront Origin Uses Insecure Match-Viewer
This plugin detects the use of the match-viewer option with CloudFront origins.
Risk Level: Low
Description:
This plugin detects the use of the match-viewer option with CloudFront origins. SentinelOne CNS strongly recommends not use the match-viewer option for securing CloudFront origins.
About the Service :
Amazon CloudFront is a web service that accelerates your online content delivery to your users, such as.html,.css,.js, or picture files. CloudFront provides your content over a global data center network known as edge locations. When a user requires the material you provide with CloudFront, the request routes to the lowest delay location, ensuring optimum performance for the content.
Impact :
In case the CloudFront origin uses an insecure match-viewer, it becomes vulnerable to exploits.
Steps to reproduce :
- Log In the AWS Console.
- Move to Cloudfront dashboard.
- Click on the Distributions panel on the left panel to access the distributions.
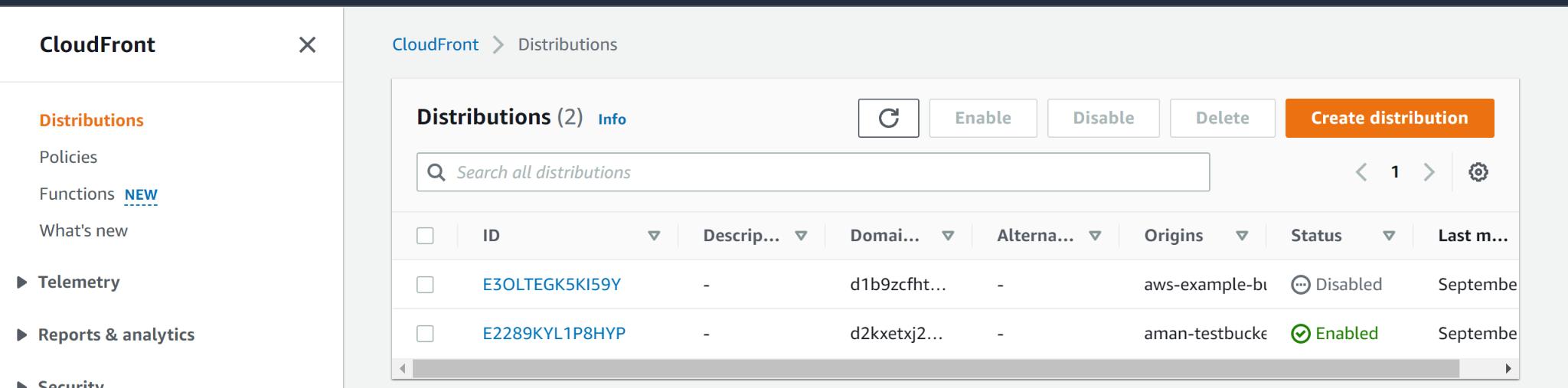
- Choose the distribution origin that you want to verify from the Origins tab.
- Verify the protocols enabled within the Origin Protocols Policy category, on the Origin Settings page.
- If the Match Viewer checkbox is checked then it can be concluded that the CloudFront Origin uses Insecure Match-Viewer.
Steps for remediation :
- Log In the AWS Console.
- Move to Cloudfront dashboard.
- Click on the Distributions panel on the left panel to access the distributions.

- Choose the distribution origin that you want to verify from the Origins tab.
- Verify the protocols enabled within the Origin Protocols Policy category, on the Origin Settings page.
- If the Match Viewer checkbox is checked then it can be concluded that the CloudFront Origin uses Insecure Match-Viewer.
- Uncheck the Match Viewer checkbox.
References: