CloudTrail Bucket Access Logging Disabled
This plugin enables access logging in the CloudTrail logging bucket to detect log file manipulation
Risk Level: MEDIUM
Description:
This plugin enables access logging in the CloudTrail logging bucket to detect log file manipulation. For an extra layer of auditing, CloudTrail buckets should use access logging. The additional access logs can help discover who performed the changes if the log files are destroyed or manipulated in any manner.
Recommended Action: Enable access logging on the CloudTrail bucket from the S3 console
About the Service :
AWS CloudTrail is an AWS service that allows you to manage your AWS account's governance, compliance, operational, and risk auditing. In CloudTrail, actions done by a user, role, or AWS service are recorded as events. Actions made in the AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs are all considered events.
Impact:
Because CloudTrail buckets contain important data, they should be secured against unwanted access. You can trace any requests made to access your CloudTrail buckets with S3 Server Access Logging enabled, and you can even limit who can edit or remove the access logs to prevent a user from covering their tracks.
Steps to reproduce :
- Sign in to your AWS management console.
- Navigate to the CloudTrail dashboard at: https://console.aws.amazon.com/cloudtrail/
- On the left panel, select Trails.
- Click on the trail you want to examine.
- Under the S3 section check for the S3 bucket name.
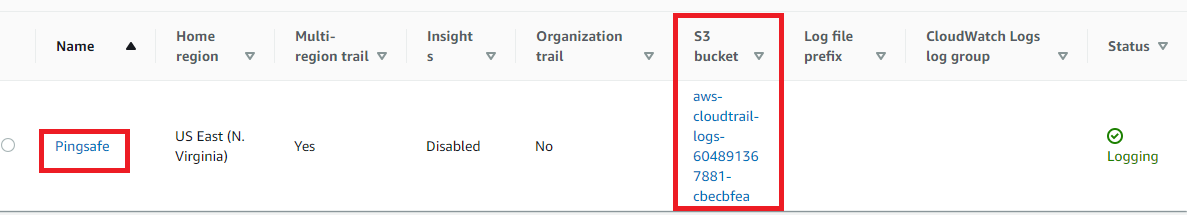
- Navigate to the S3 dashboard at: https://console.aws.amazon.com/s3/
- Select the S3 bucket used for CloudTrail logging, then click the Properties tab from the right panel.
- Under Properties, check for the value of Server Access Logging.
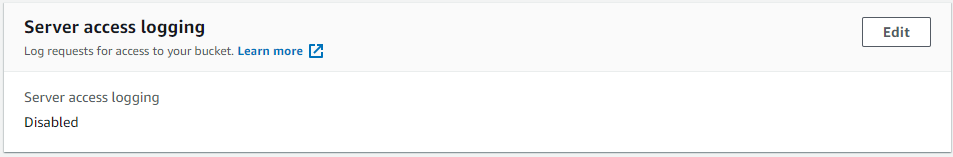
- If disabled, then the logging feature is not enabled for the selected CloudTrail bucket.
- Repeat steps no. 4-8 for other trails in the selected AWS region as well as for other regions.
Steps for remediation :
- Sign in to your AWS management console.
- Navigate to the CloudTrail dashboard at: https://console.aws.amazon.com/cloudtrail/
- On the left panel, select Trails.
- Click on the trail you want to examine.
- Under the S3 section check for the S3 bucket name.

- Navigate to the S3 dashboard at: https://console.aws.amazon.com/s3/
- Select the S3 bucket used for CloudTrail logging, then click the Properties tab from the right panel.
- Under Properties, scroll down to Server Access Logging and click Edit.
- Click on Enable radio button and select a target bucket from the dropdown list.
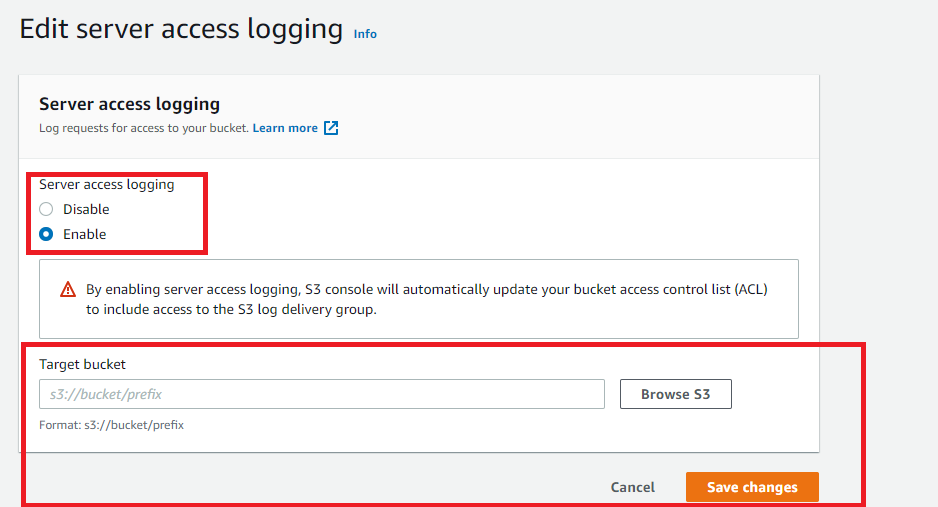
- Click on Save changes to apply the settings.
- Repeat steps no. 4-10 for other trails in the selected AWS region as well as for other regions
References: