CloudTrail Bucket Delete Policy Disabled
This plugin guarantees that the CloudTrail logging bucket has a policy in place that prevents logs from being deleted without an MFA token
Risk Level: MEDIUM
Description:
This plugin guarantees that the CloudTrail logging bucket has a policy in place that prevents logs from being deleted without an MFA token. CloudTrail logging buckets should require an MFA token to delete items for added protection.
Recommended Action: Enable MFA delete on the CloudTrail bucket.
About the Service :
AWS CloudTrail is an AWS service that allows you to manage your AWS account's governance, compliance, operational, and risk auditing. In CloudTrail, actions done by a user, role, or AWS service are recorded as events. Actions made in the AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs are all considered events.
Impact:
Not using an MFA-protected bucket for AWS CloudTrail will result in the accidental or intentional deletion of your versioned log files in case your access credentials are compromised.
Steps to reproduce :
- Sign in to your AWS management console.
- Navigate to the CloudTrail dashboard at: https://console.aws.amazon.com/cloudtrail/
- On the left panel, select Trails.
- Click on the trail you want to examine.
- Under the S3 section check for the S3 bucket name.
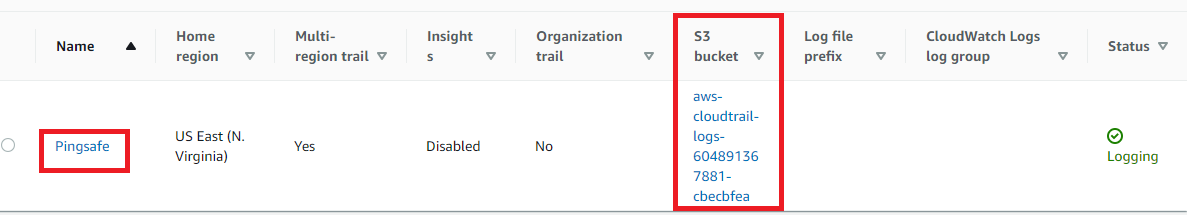
- Navigate to the S3 dashboard at: https://console.aws.amazon.com/s3/
- Select the S3 bucket used for CloudTrail logging, then click the Properties tab from the right panel.
- Under Properties, scroll down to Bucket Versioning and check if it is enabled or disabled then the S3 bucket selected is not MFA-protected.
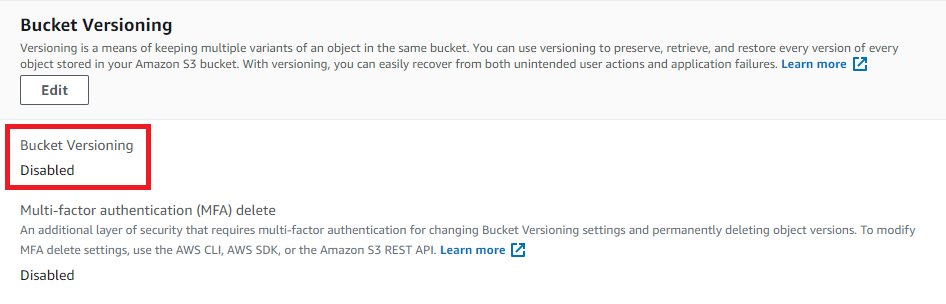
- Repeat steps no. 4-8 for other trails in the selected AWS region as well as for other regions.
Steps for remediation ( Using AWS CLI ):
- Run put-bucket-versioning command to enable versioning and MFA Delete for the selected bucket at same time by replacing the --mfa parameter with the root account’s arn and the bucket name with that of the vulnerable trail.
– aws s3api put-bucket-versioning
–bucket <Bucket_Name>
-versioning-configuration ‘{“MFADelete”:”Enabled”,”Status”:”Enabled”}’
–mfa ‘arn:aws:iam::<aws_account_id>:mfa/root-account-mfa-device <passcode>’ - Run get-bucket-versioning command and determine if versioning and MFA delete are enabled or not.
aws s3api get-bucket-versioning
--bucket cloudtrail-global-logging - If yes, they will be clearly visible in the command output that appears.
- For more details regarding S3 MFA delete, refer to this article :https://docs.pingsafe.ai/knowledge/s3-bucket-mfa-delete-disabled
References: