Directly Attached User IAM Policies
This plugin guarantees that IAM policies are not directly associated with IAM users.
Risk Level: Low
Description:
This plugin guarantees that IAM policies are not directly associated with IAM users. IAM permissions are only to be allocated to roles and groups to decrease administrative complexity. Then those groups can be joined by the users. The policy should not immediately be applied to a user.
SentinelOne CNS strongly recommends creating groups with the required policies, moving the IAM users to the applicable groups, and then removing the inline and directly attached policies from the IAM user.
About the Service :
AWS ID and Access Management (IAM) allows you to securely manage access to AWS services and resources. With IAM, AWS users and groups can be established and managed and permissions used to enable access by AWS resources and prohibit them.
We can discover and adjust the rules so that only the services are accessible. We can thus adhere better to the less privileged principle.
Impact :
The presence of directly attached User IAM policies increases the management policies hence the policies should be attached to the groups and then the user can be added to the group.
Steps to reproduce :
- Login to AWS Management Console.
https://console.aws.amazon.com/ - Navigate to the IAM dashboard.
https://console.aws.amazon.com/iam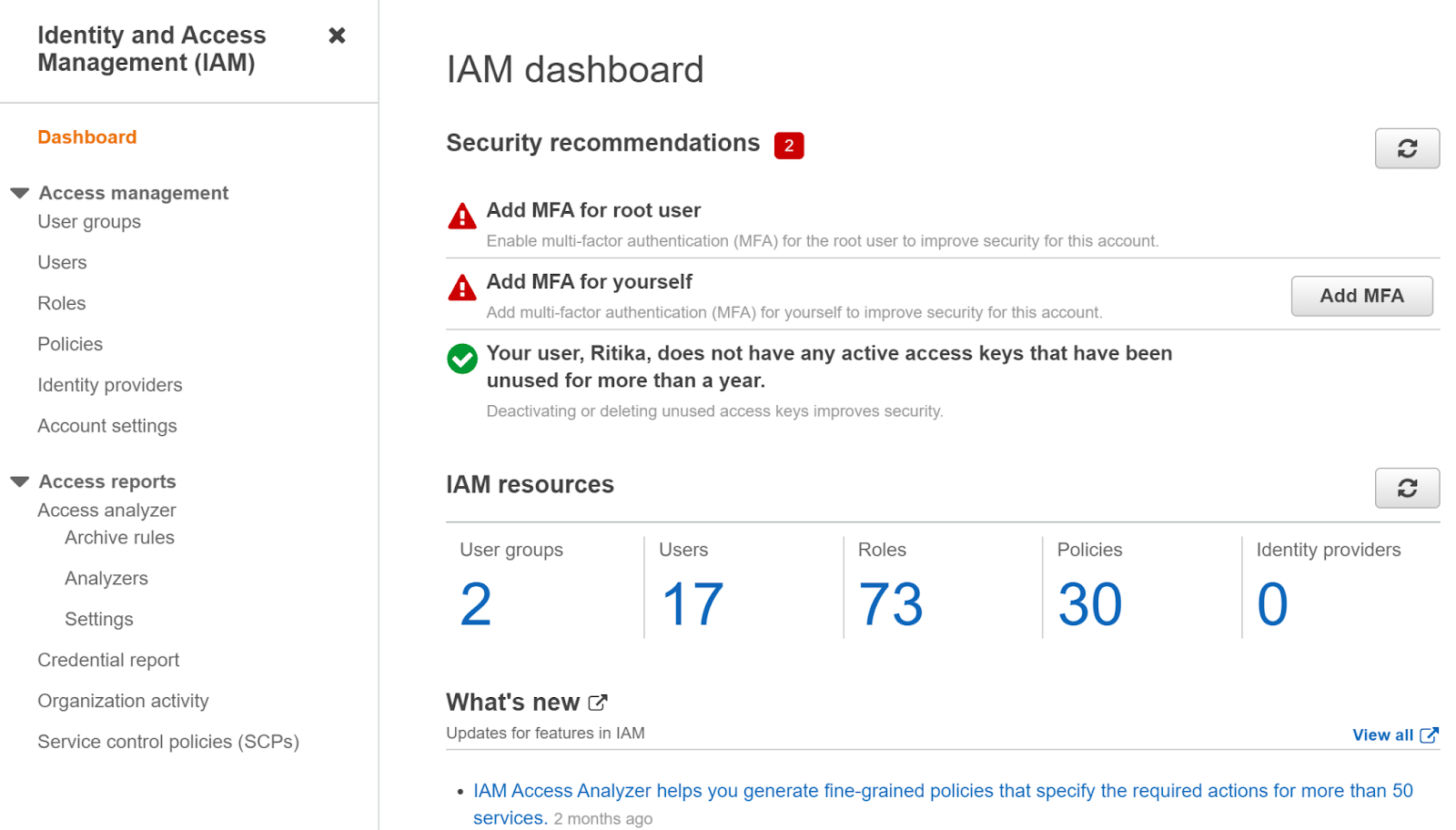
- Select Users from the Access Management in the left navigation panel.
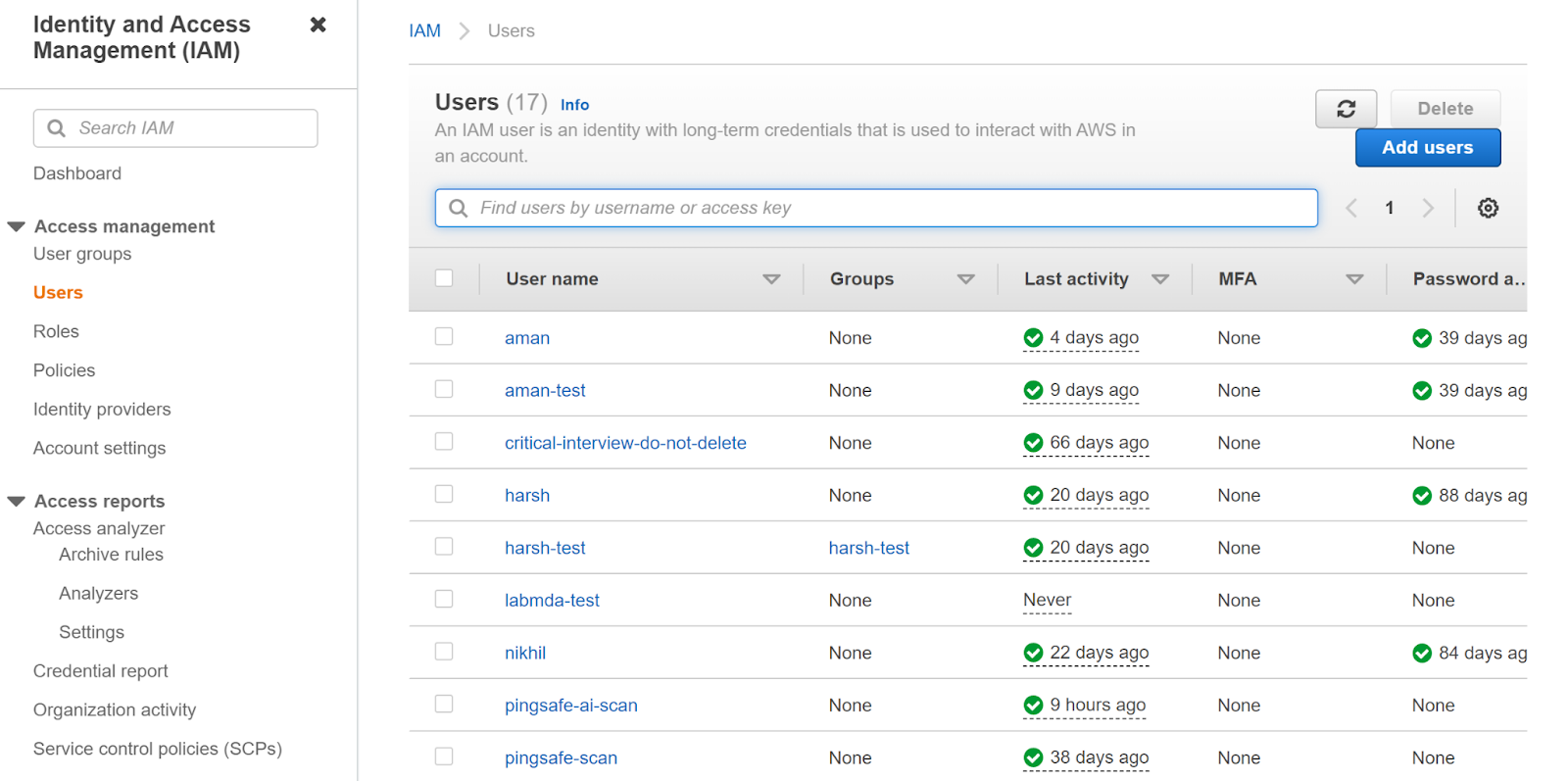
- Select the user that you want to examine and then navigate to the Permissions tab, then look at the policies.
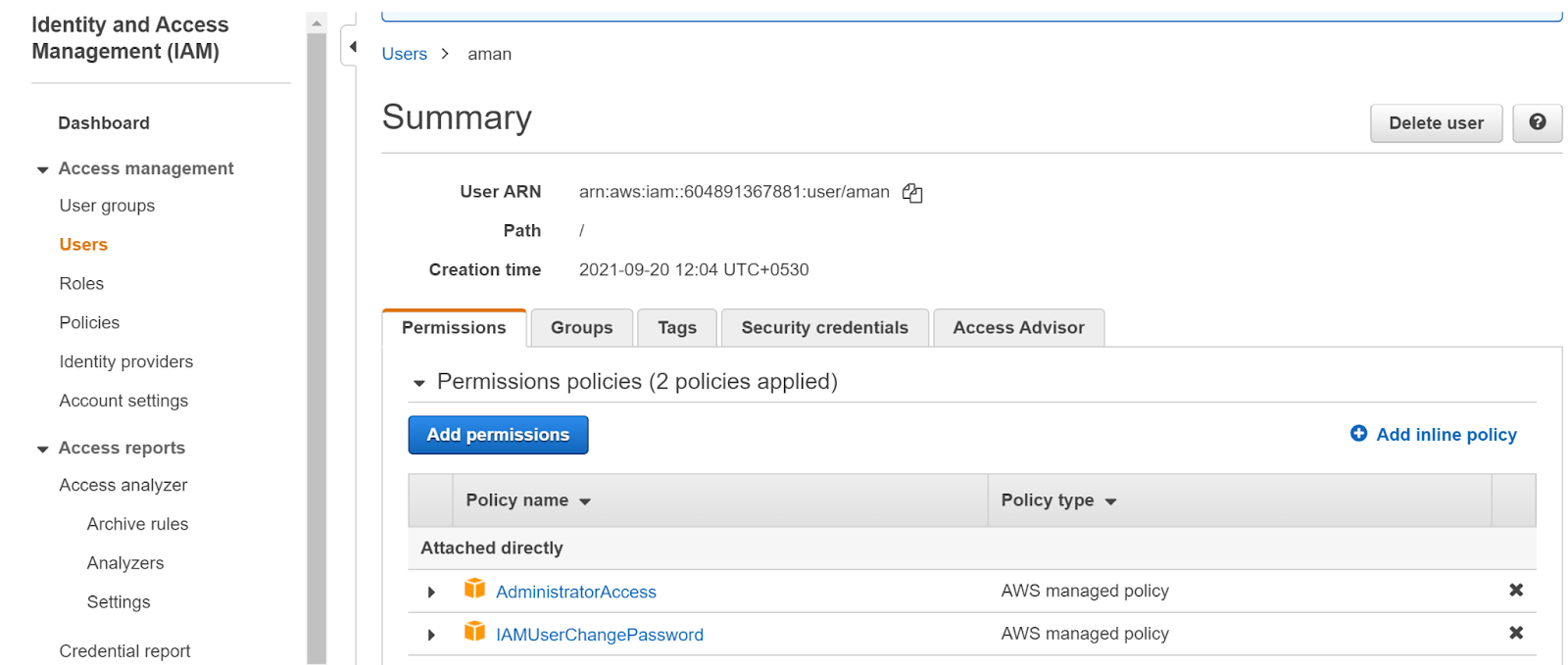
- We can clearly see that there are two policies that are attached directly to the user. This suggests that the user has policies that are directly attached.
- Repeat the steps for other users as well.
Steps for remediation :
- Login to AWS Management Console.
https://console.aws.amazon.com/ - Navigate to the IAM dashboard.
https://console.aws.amazon.com/iam
- Select Users from the Access Management in the left navigation panel.

- Select the user that you want to examine and then navigate to the Permissions tab, then look at the policies.

- We can clearly see that there are two policies that are attached directly to the user. This suggests that the user has policies that are directly attached.
- In order to overcome this problem, we will create a group and attach these policies to the group and then add the users to the group.
- To create a group, click on User groups under Access management in the left navigation panel.
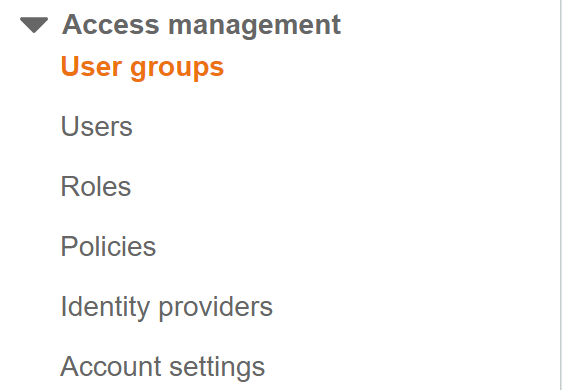
- A list of groups will appear on the page along with the option to create new groups. Click on Create Group button.
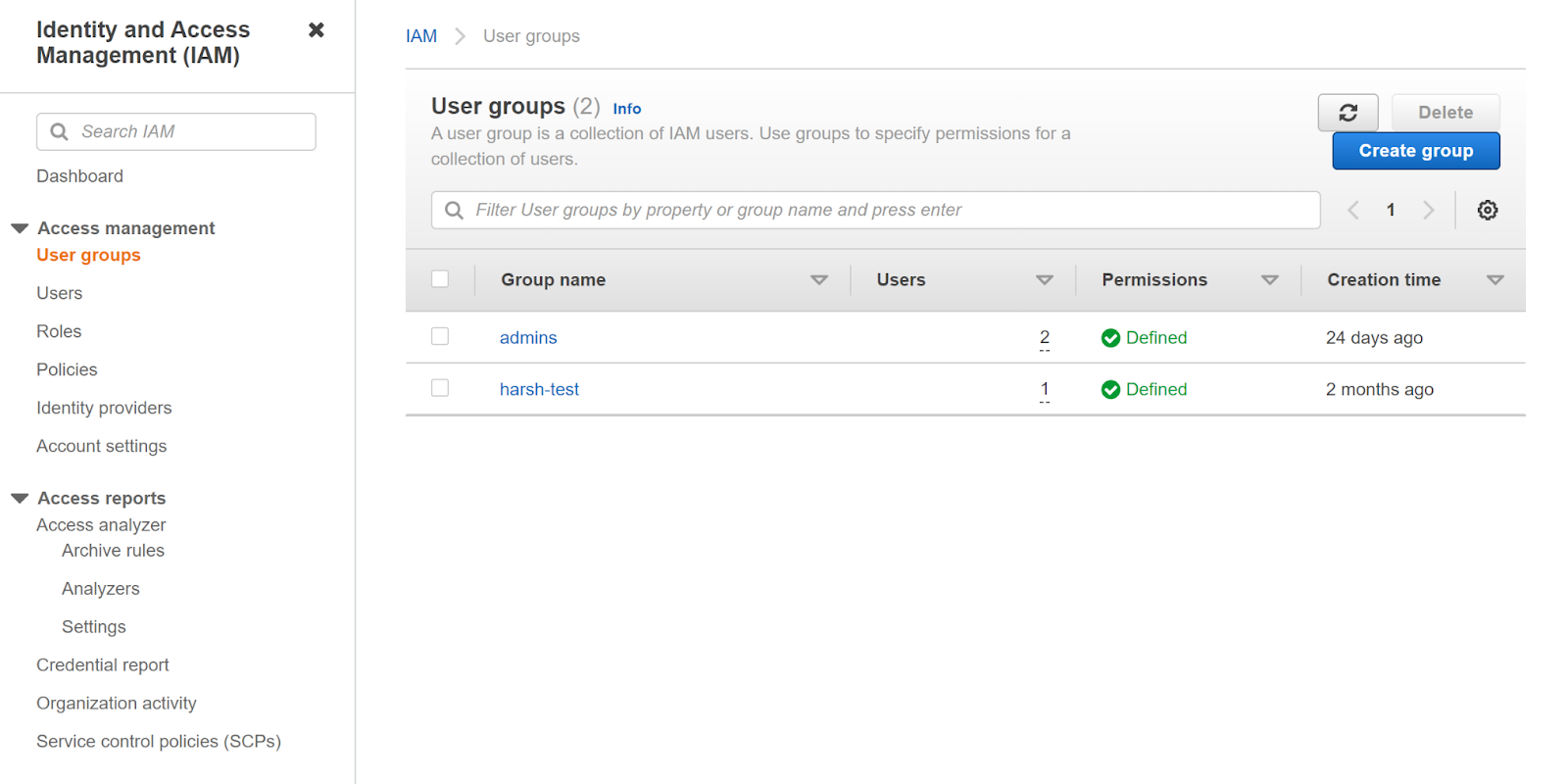
- Create user group tab will appear. Next, we will enter the group name.

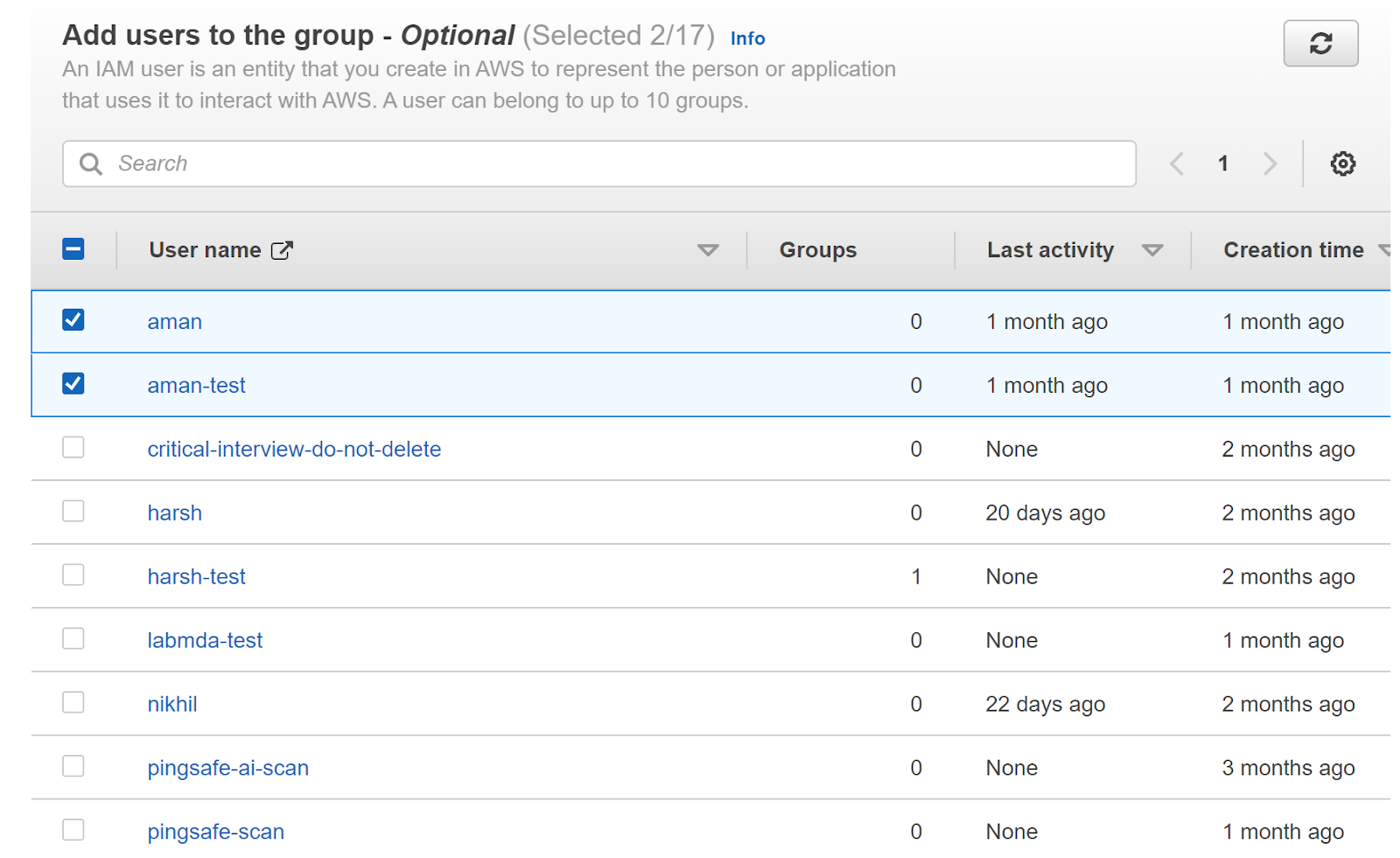
- Next, we will add the user to the group by clicking on the user’s name in the Add users to the group section.
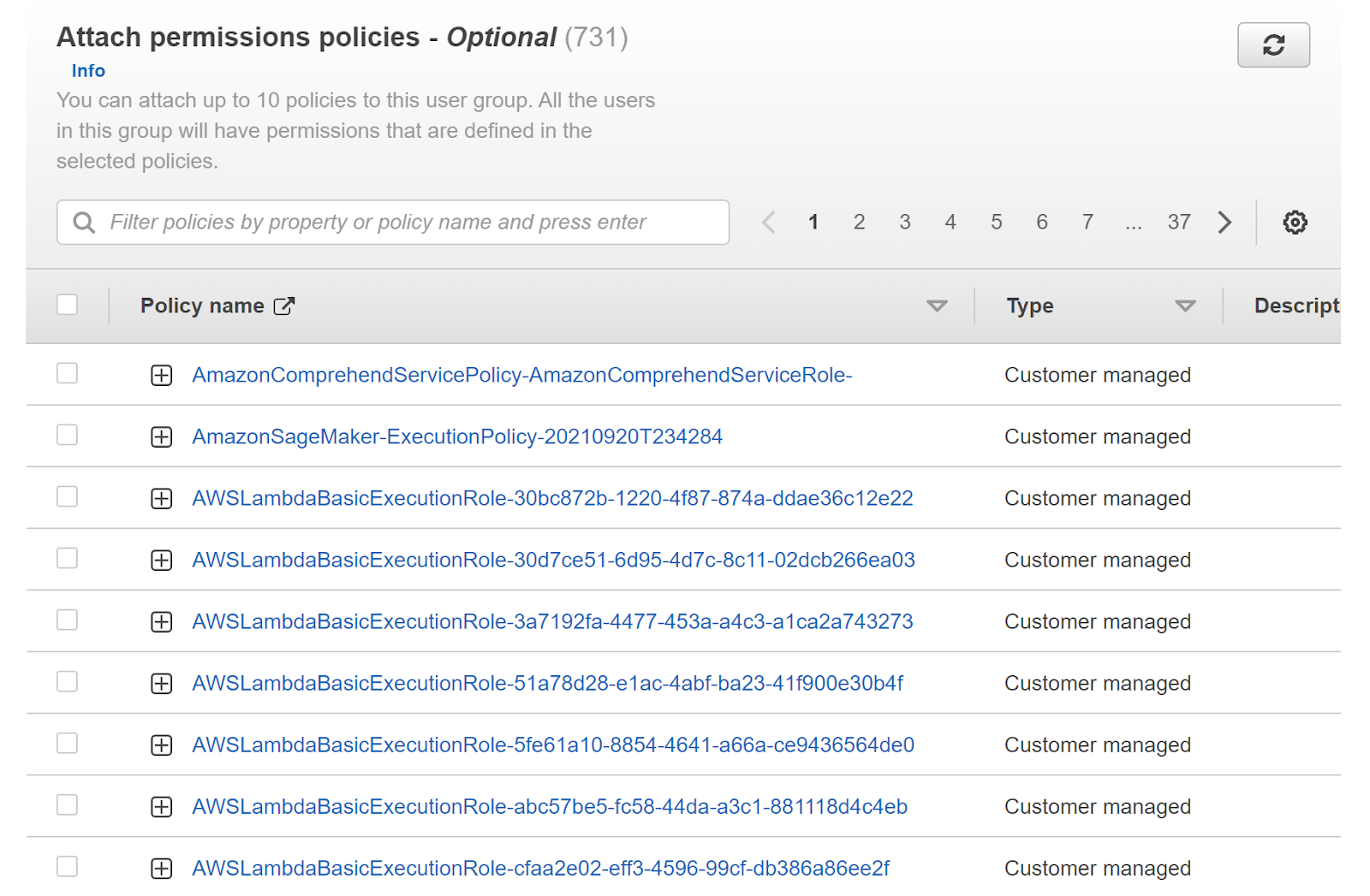
- Further, we will add the policies to the group by selecting the policies in the Attach permissions policy.
- In order to finish the procedure, we will click on the Create Group button at the bottom of the page.
- Repeat the steps for other users as well.
References: