EC2 Instances Vulnerable To SSRF Attack
This plugin ensures EC2 instance metadata is updated to require HttpTokens or disable HttpEndpoint.
Risk Level: High
Description
This plugin ensures EC2 instance metadata is updated to require HttpTokens or disable HttpEndpoint. The latest version of EC2 metadata service prevents SSRF attack escalations from accessing the sensitive instance metadata endpoints.
About the Service
Amazon EC2: Amazon Elastic Compute Cloud (Amazon EC2) provides scalable computing capacity in the Amazon Web Services (AWS) Cloud. With the EC2 instance, you can launch as many virtual servers as you need, configure security and networking, and manage storage without worrying about the hardware needs of the process. Security Groups act as a firewall for an EC2 instance to control the incoming and outgoing traffic. You can read more about security groups here.
Impact
AWS Instance Metadata Service (IMDS) provides the complete metadata of your instance. It presents all the necessary information required for configuring and managing the instance. In case this metadata lands into the hands of an attacker, it can be exploited to gain temporary credentials to access the instance. If the attacker is successful in acquiring access to the instance, he can exploit all the permissions the instance has and harm the cloud infrastructure.
AWS IMDS service can be accessed from an instance with a simple request on the following URLs:
http://169.254.169.254/latest/meta-data/
http://[fd00:ec2::254]/latest/meta-data/
It will return a list of metadata categories. You can learn more about the categories here.
The metadata can only be securely accessed by the AWS services running from your account. But what if someone tries to leverage your service itself to get hold of this information? This is known as the SSRF attack.
Server-side request forgery (SSRF) is a web security flaw that allows an attacker to force a server-side application to send HTTP requests to an arbitrary domain of the attacker's choosing. In most cases, the request results in establishing an unauthorized connection with the server’s internal infrastructure.
SSRF attack on a vulnerable EC2 instance
Consider example-ssrf.com as a website running on a vulnerable EC2 instance server, that accepts a website URL and displays the contents. A typical SSRF attacker will try to access the instance metadata with a simple request by trying to hit the endpoint -
http://169.254.169.254/latest/meta-data/identity-credentials/ec2/security-credentials/ec2-instance
We shall consider both AWS IMDSv1 and AWS IMDSv2 instance metadata configurations.
Case 1: AWS IMDSv1
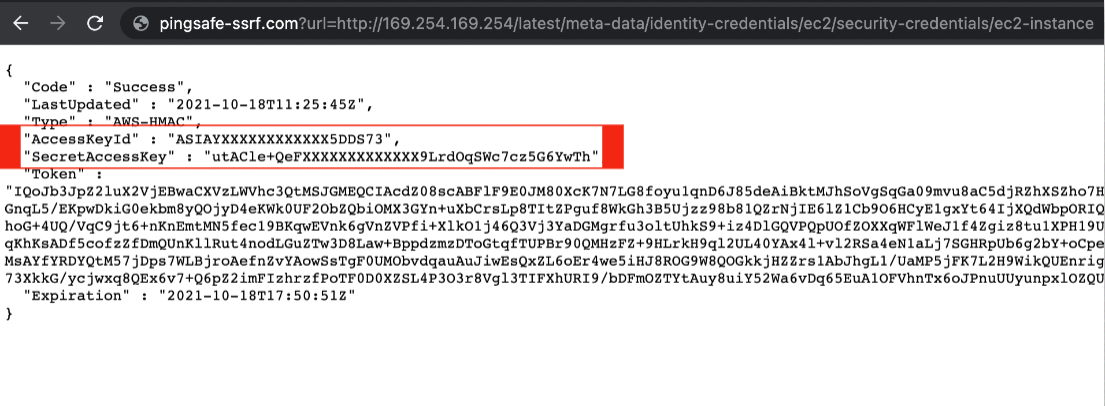
This simple request will unveil both the AccessKeyId and SecretAccessKey to the attacker without any need of authorization. It happens because the URL request is performed by the EC2 instance server which can access the details without any blockers.
Case 2: AWS IMDSv2
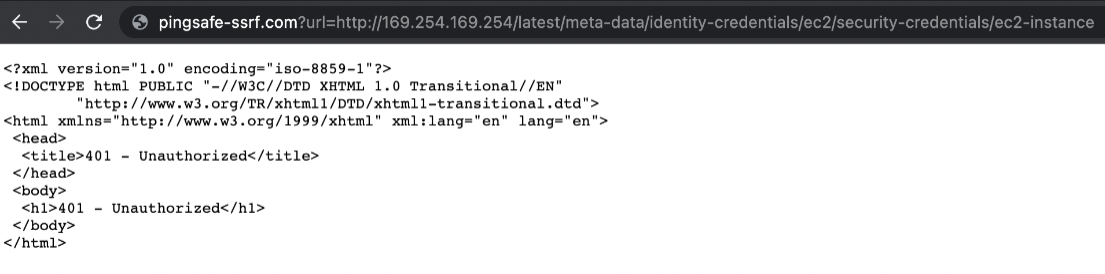
In case the instance has IMDSv2 configured, the request will be unauthorized to perform the action. It is because IMDSv2 has an additional layer of security which demands a token to be passed in the Header to get the metadata. You can read more about it here.
Steps to Reproduce
Using AWS CLI-
1. Configure the AWS CLI with your account credentials.
2. List all the instances in the region by running the describe-instances command as:
aws ec2 describe-instances --region <region>
4. Verify the same for all the other instances in the array and mark their instance-id.
Steps for Remediation
Update instance metadata options to use (Instance Metadata Service) IMDSv2:
During Creation (Using AWS Console):
- Log In to your AWS Console.
- Open the EC2 Management Console. You can use this link (https://console.aws.amazon.com/ec2) to navigate directly if already logged in.
- Move to the Instances in the Instances section from the left navigation pane.
- Click on Launch Instance. After Choosing the AMI and Instance type, move to the Configure Details section.
- Scroll down to the Advanced Details section. From the Metadata Version option, choose V2 (token required).
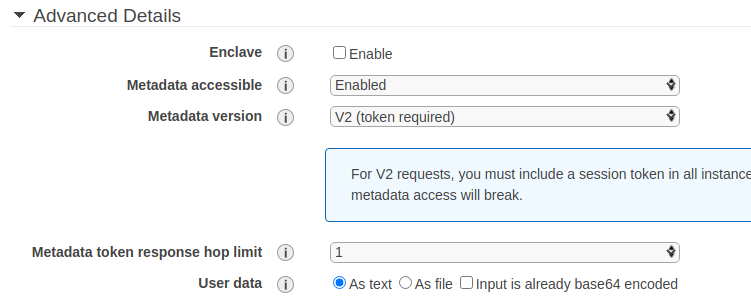
- Complete the next process of creating an instance as per your requirements.
Running Instance (Using AWS Console + AWS CLI):
- Log In to your AWS Console.
- Open the EC2 Management Console. You can use this link (https://console.aws.amazon.com/ec2) to navigate directly if already logged in.
- Move to the Instances in the Instances section from the left navigation pane.

- From the list of instances, copy the Instance ID of the vulnerable instance.
- Now, configure the AWS CLI with your account credentials.
- Type the following command to allow access to the instance metadata only with an access token.
aws ec2 modify-instance-metadata-options \
--instance-id <Instance_Id> \
--http-tokens required \
--http-endpoint enabled
- Repeat the steps for all the vulnerable instances.