ElasticSearch Logging Disabled
This plugin ensures ElasticSearch domains are configured to log data to CloudWatch
Risk Level: Medium
Description
This plugin ensures ElasticSearch domains are configured to log data to CloudWatch. ElasticSearch domains should be configured with logging enabled with logs sent to CloudWatch for analysis and long-term storage. The logs generated helps in identifying potential security threats by monitoring unusual requests. As good security practice, PingSafe recommends enabling logging for OpenSearch domains.
About the Service
Amazon OpenSearch: With Amazon OpenSearch, one can analyze, query and visualize petabytes of text and unstructured data. It makes the complex process of performing interactive log analytics, real-time application monitoring, website search, an easy process. Apart from this, Amazon OpenSearch also provides the possibility to capture observability logs and metrics.
Impact
Logs are important for keeping a track of requests made to the OpenSearch domains. It is recommended to regularly keep a close eye on the logs for any unusual activity. In the event of data compromise, generated logs will be useful to identify unusual or unauthorized access. It can eventually lead to the attacker's details. Without logs, the security team will not have any information to begin the investigation.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the Amazon OpenSearch Console. You can use this link (https://console.aws.amazon.com/esv3/) to navigate directly if already logged in.
- From the left navigation pane, click on Domains from the left panel.
- A list of domains will be displayed. Select the domain you want to examine by clicking on it’s name.
- Move to the Logs tab.

- In the CloudWatch Logs section, check if all the logs are enabled. If not, the vulnerability exists.
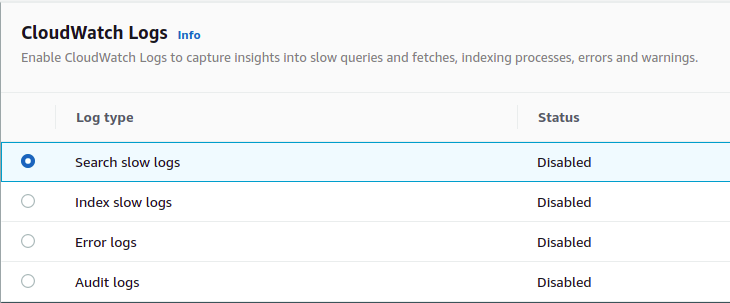
- Repeat steps 3 to 6 for all the domains you wish to examine.
Steps for Remediation
Ensure encryption-at-rest is enabled for all ElasticSearch domains.
- Log In to your AWS Console.
- Open the Amazon OpenSearch Console. You can use this link (https://console.aws.amazon.com/esv3/) to navigate directly if already logged in.
- From the left navigation pane, click on Domains from the left panel.

- A list of domains will be displayed. Select the vulnerable domain by clicking on it’s name.
- Move to the Logs tab.

- In the CloudWatch Logs section, click on Enable for all the logs which are currently disabled.
- Select a CloudWatch Log group and access policy for the domain logs.
- Repeat steps 3 to 7 for all the insecure domains.