Environment Admin Privileges
This plugin guarantees that your AWS account does not have any Amazon MWAA environment with administration capabilities.
Risk Level: High
Description:
This plugin guarantees that your AWS account does not have any Amazon MWAA environment with administration capabilities. Most restrictive IAM authorization for optimal security measures should be available to Amazon MWAA environments.
SentinelOne CNS strongly recommends modifying IAM role attached with MWAA environment to provide the minimal amount of access required to perform its tasks
About the Service :
Amazon Managed Workflows for Apache Airflow (MWAA) is a managed Apache Airflow orchestration service that enables the construction and operation of end-to-end cloud data pipelines. Amazon MWAA enables you to leverage Airflow and Python in order to develop workflows without the necessary scalability, availability, and security management infrastructure. In order to ensure quick, secure access to your data, Amazon MWAA automatically grows its executive capabilities to match your demands and is linked to AWS safety services.
Impact :
The presence of admin privileges in MWAA environments makes it difficult to maintain optimal security and allows unauthorized access to the services which can prove to be dangerous for the organization.
Steps to reproduce :
- Sign In to your AWS Console.
- Navigate to the Amazon Managed Workflows for Apache Airflow (MWAA) dashboard. (https://ap-south-1.console.aws.amazon.com/mwaa/ )
- Next, navigate to the Environments of MWAA.

- Select the environment to examine and then check out the Execution role under the Permissions tab.
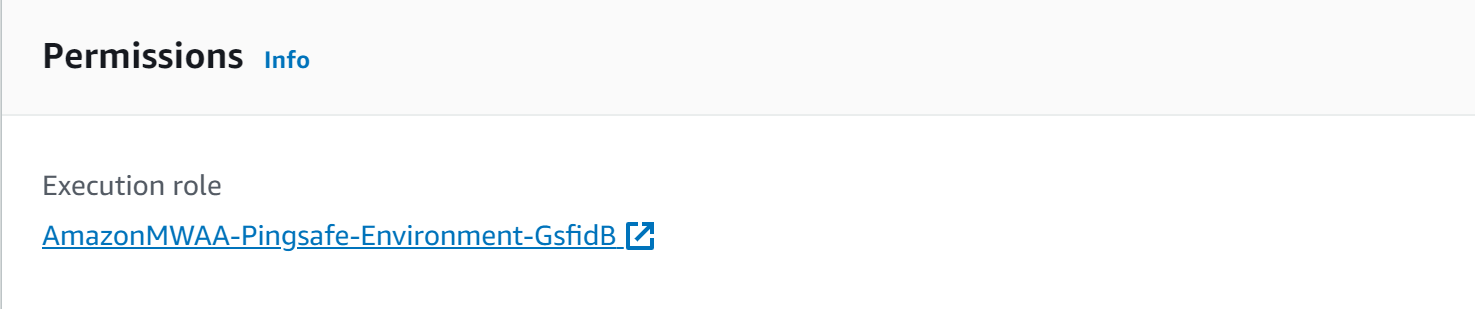
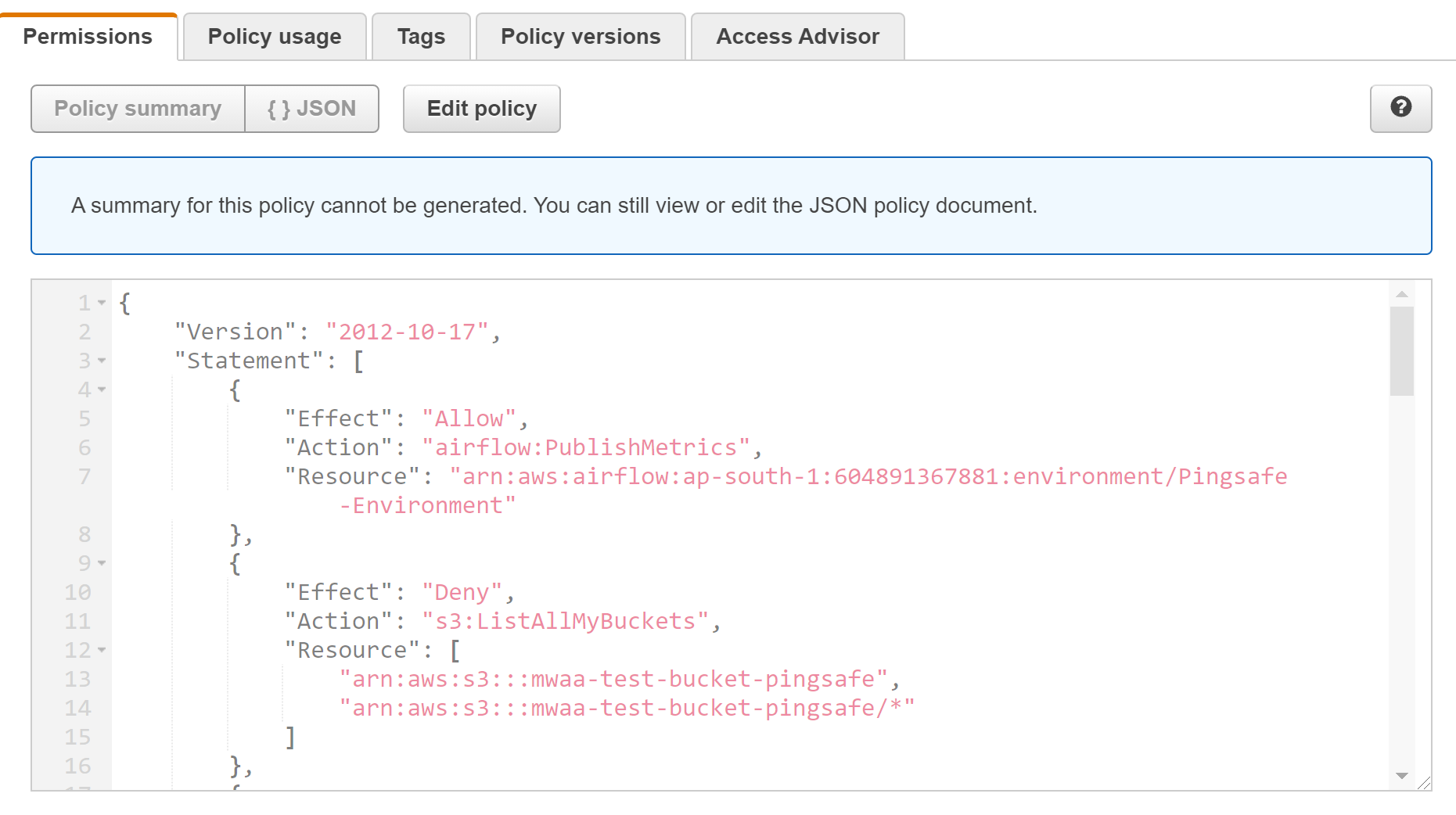
- A new tab opens up of Roles in the IAM dashboard. Next, under Permissions select the policy and examine.
- We can clearly observe that under the Policy, ”Effect”: “Allow”, “Action”:”*” and “Resource”: “*”. This suggests that the environment has administrative privileges.

- Repeat the steps for other environments.
Steps for remediation :
- Sign In to your AWS Console.
- Navigate to the Amazon Managed Workflows for Apache Airflow (MWAA) dashboard.
https://ap-south-1.console.aws.amazon.com/mwaa/
- Next, navigate to the Environments of MWAA.

- Select the environment to examine and then check out the Execution role under the Permissions tab.

- A new tab opens up of Roles in the IAM dashboard. Next, under Permissions select the policy and examine.
- We can clearly observe that under the Policy, ”Effect”: “Allow”, “Action”:”*” and “Resource”: “*”. This suggests that the environment has administrative privileges.

- We have to delete the code which snippet - ”Effect”: “Allow”, “Action”:”*” and “Resource”: “*” to make remove administrative privileges so we have to edit policy and erase that snippet.
- After that click Review Policy and Save Changes to keep the changes intact.
- Repeat the steps for other environments.
References: