Extra User Admins
This plugin makes sure that there are a minimal amount of IAM admins in the account.
Risk Level: Medium
Description:
This plugin makes sure that there are a minimal amount of IAM admins in the account. It checks if the number of admins is in the specified range.
SentinelOne CNS strongly recommends keeping minimum users with admin permissions but ensuring other IAM users have more limited permissions.
Configuration Parameters
IAM Admin Count Minimum: The parameter holds the minimum count of IAM user admins to require in the account. When the number of admins is inferior to the desired minimum value, CNS raises an issue. By default, the minimum value of the IAM Admin Count is 1 user.
IAM Admin Count Maximum: The parameter holds the maximum count of IAM user admins to require in the account. When the number of admins exceeds the desired maximum value, CNS raises an issue. By default, the maximum value of the IAM Admin Count is 2 users.
About the Service :
AWS ID and Access Management (IAM) allows you to securely manage access to AWS services and resources. With IAM, AWS users and groups can be established and managed and permissions used to enable access by AWS resources and prohibit them.
We can discover and adjust the rules so that only the services are accessible. We can thus adhere better to the less privileged principle.
Impact :
If more users have administrative authorization or authorization to create, modify or remove any resource, access any data within the AWS environment, and use any service or component their actions can lead to severe security problems, data leaks, data loss, or unexpected charges on your AWS bill.
Compliances covered :
Steps to reproduce :
- Login to AWS Management Console.
- Navigate to the IAM dashboard.
https://console.aws.amazon.com/iam
- Click on Users in the left navigation panel under the Identity and Access Management (IAM) heading.
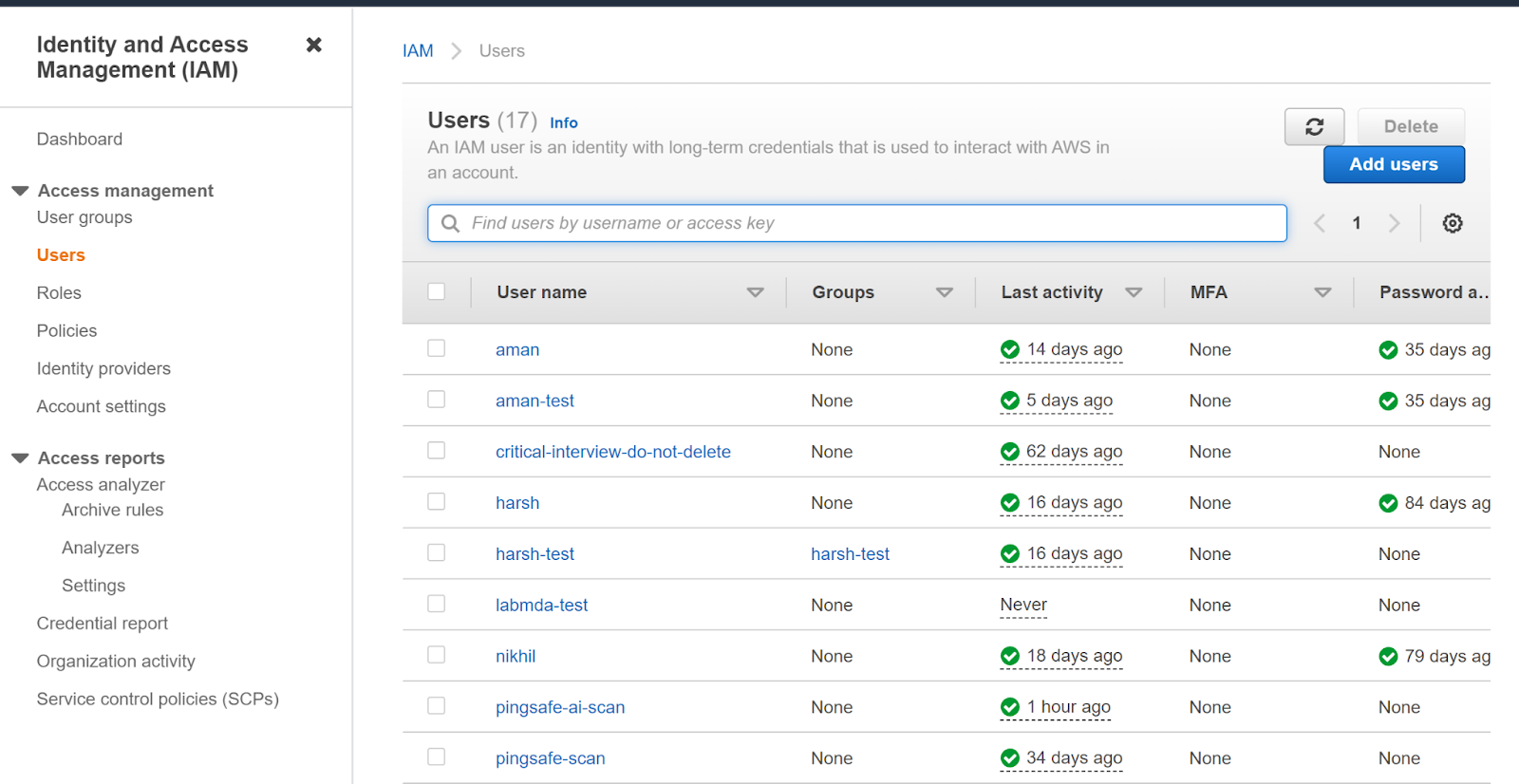
- Click on the user you want to examine. Then under Permissions, check if there is an Administrator access policy in the Permission Policy.
- If the Administrator access policy is present in the Permission Policy, this suggests that the user has admin privileges.
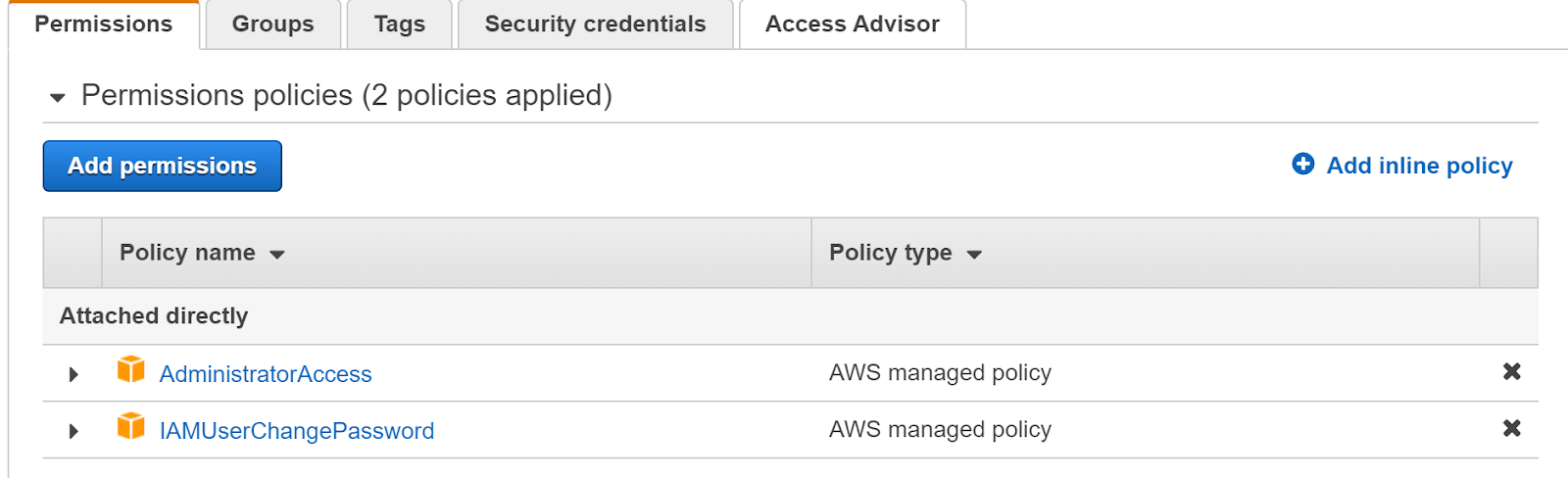
- Repeat the same procedure for other users as well.
Steps for remediation :
- Login to AWS Management Console.
- Navigate to the IAM dashboard.
https://console.aws.amazon.com/iam
- Click on Users in the left navigation panel under the Identity and Access Management (IAM) heading.

- Click on the user you want to examine. Then under Permissions, check if there is an Administrator access policy in the Permission Policy.
- If the Administrator access policy is present in the Permission Policy, this suggests that the user has admin privileges.

- Remove the administrative privileges by clicking on the cross on the left of the policy name.
- Repeat the same procedure for other users as well.
References: