Groups Without Users
This plugin guarantees that all groups have at least one member.
Risk Level: Medium
Description:
This plugin guarantees that all groups have at least one member. While there are no immediate security issues with vacant groups, it expands the management landscape that might possibly create future risks.
PingSafe strongly recommends removing unused groups without users.
About the Service :
AWS ID and Access Management (IAM) allows you to securely manage access to AWS services and resources. With IAM, AWS users and groups can be established and managed and permissions used to enable access by AWS resources and prohibit them.
We can discover and adjust the rules so that only the services are accessible. We can thus adhere better to the less privileged principle.
Impact :
If the groups without Users will not be removed or will be forgotten then it raises the risk of allowing unauthorized users to access AWS resources.
Steps to reproduce :
- Sign-in to AWS management console.
- Navigate to the “IAM” dashboard.
https://console.aws.amazon.com/iamv2/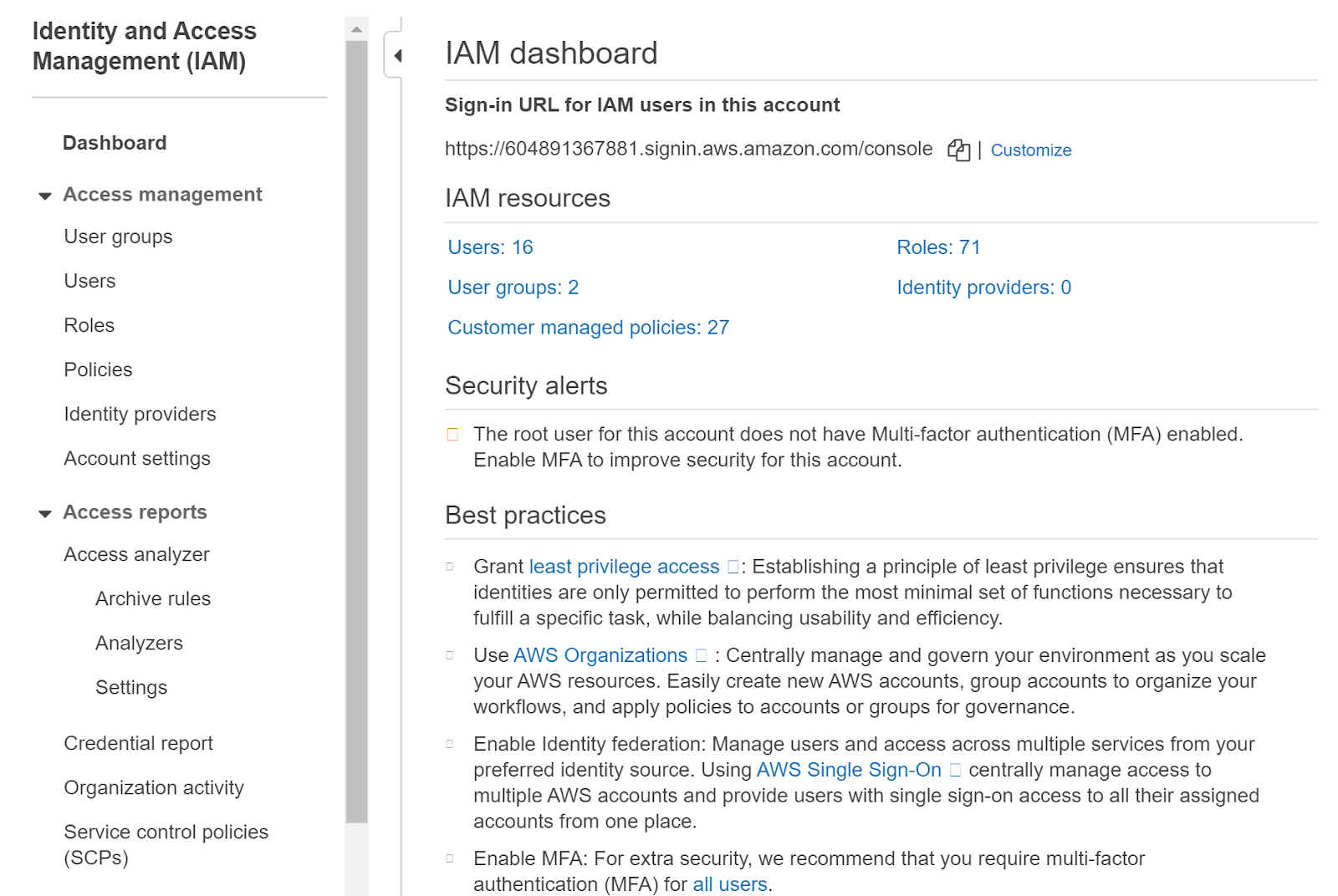
- Select “User Groups” in the left panel and click on the group you want to examine.
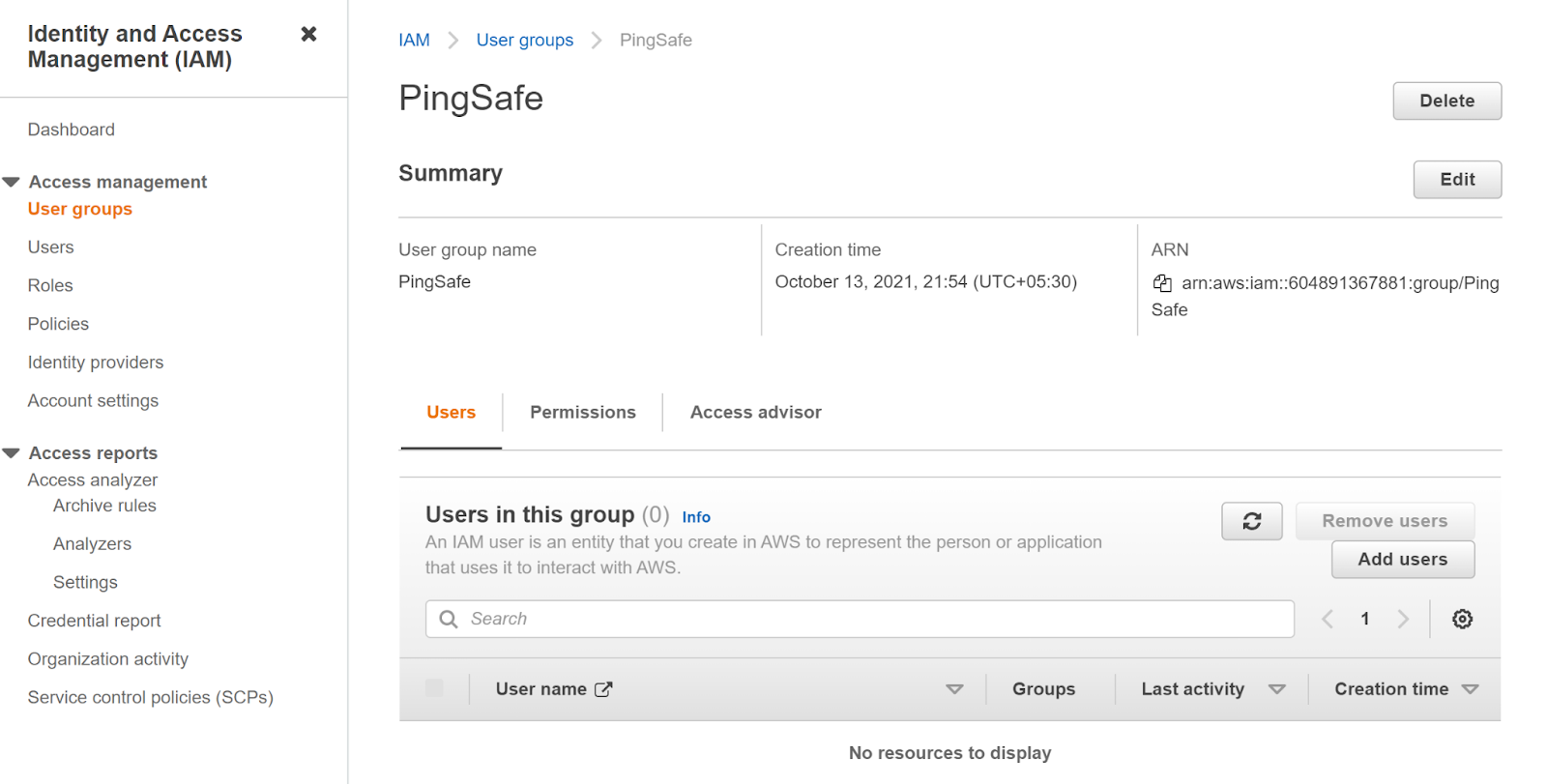
- In the “Users” look for the users of the group. We can observe that this group does not have any users.
- Repeat the same steps to look for the users of other groups.
Steps for remediation :
- Sign-in to AWS management console.
- Navigate to the “IAM” dashboard.
https://console.aws.amazon.com/iamv2/
- Select “User Groups” in the left panel and click on the group you want to examine.

- In the “Users” look for the users of the group. We can observe that this group does not have any users.
- Click on the “Delete” button to delete the group without users.
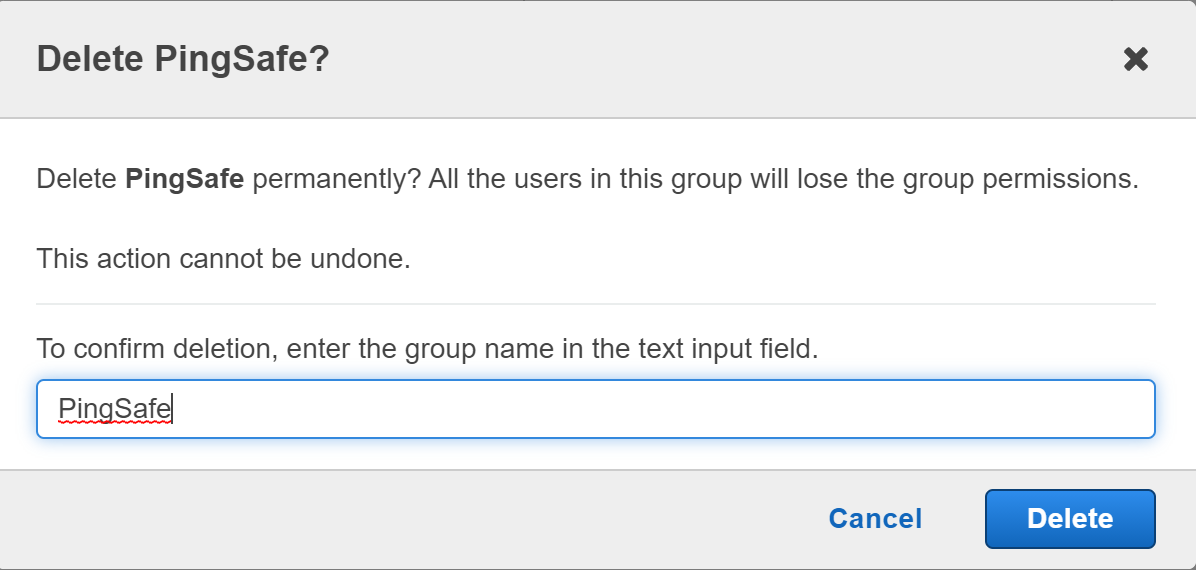
- Repeat the steps for more such groups.
References: