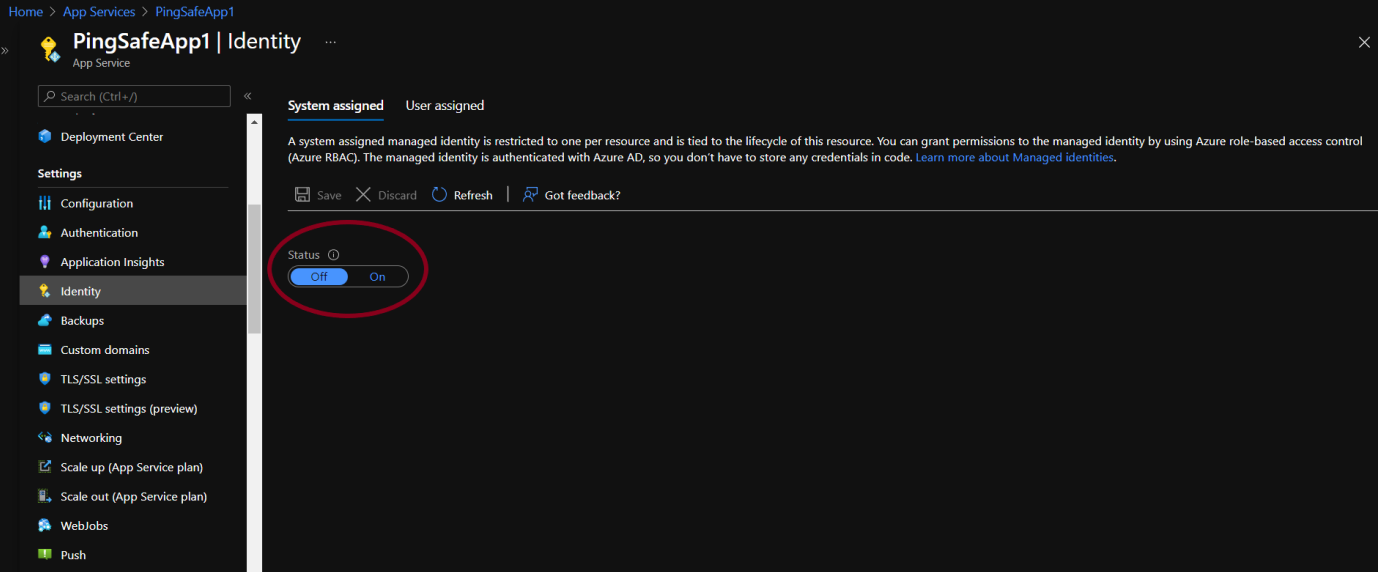
Identity Disabled
Risk Level: Medium
Description
This plugin ensures that a system or user-assigned managed identity is enabled to authenticate to App Services without storing credentials in the code. A system or user-assigned managed identity should be assigned to every application so that they can access Azure resources seamlessly. It is more secure than hard-coding credentials into the application.
About the Service
App Services: The app services at azure offers to host web applications, REST API and backend services for mobile and web applications. Hosting web apps on Azure lets users focus on managing the application and its data.
Impact
Maintaining cloud connection credentials in code is a security risk. Credentials should never appear on developer workstations and should not be checked into source control. Managed identities for Azure resources provide Azure services with a managed identity in Azure AD which can be used to authenticate to any service that supports Azure AD authentication, without having to include any credentials in code.
Steps to Reproduce
- Log in to the Azure portal.
- Click on App Services.
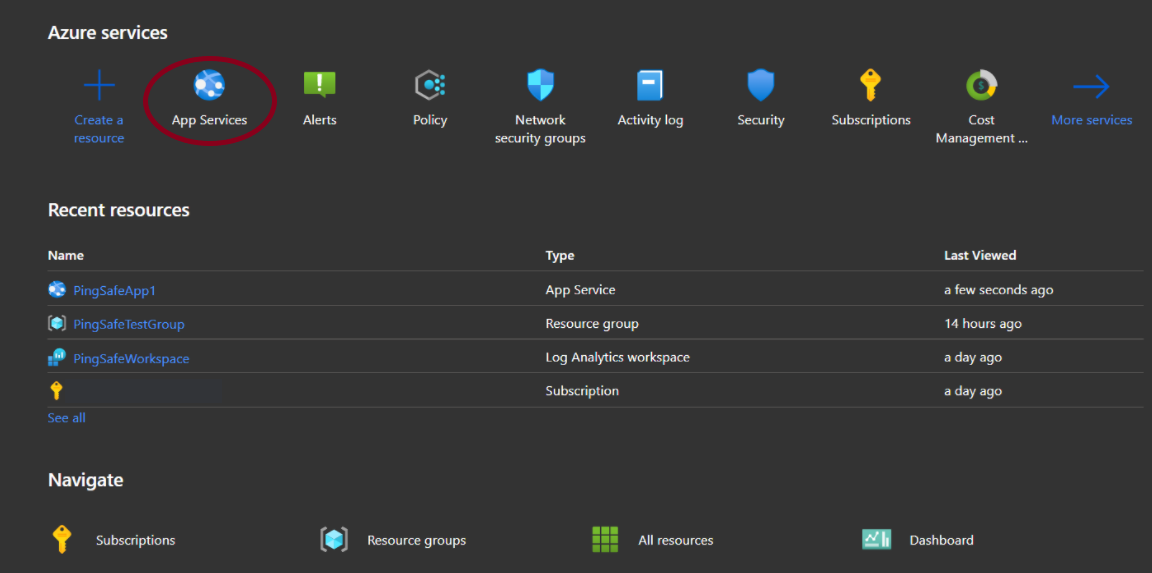
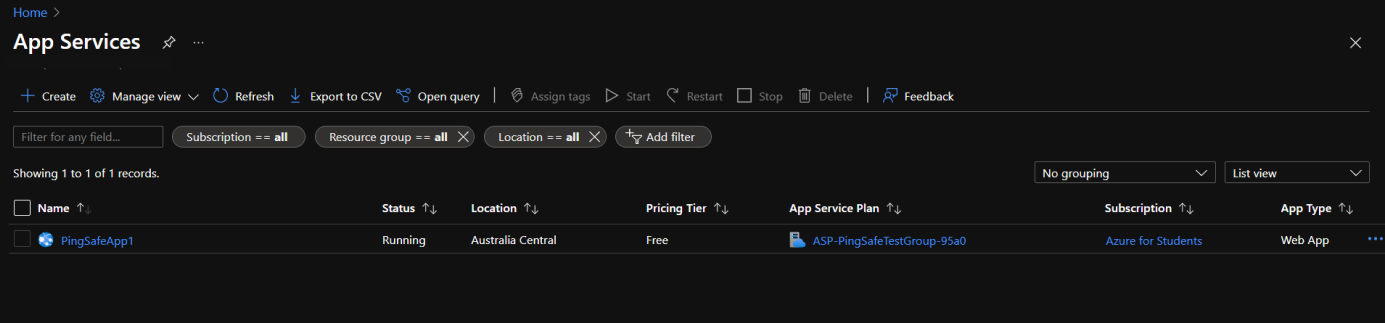
- Select an App Service plan from the listed apps.
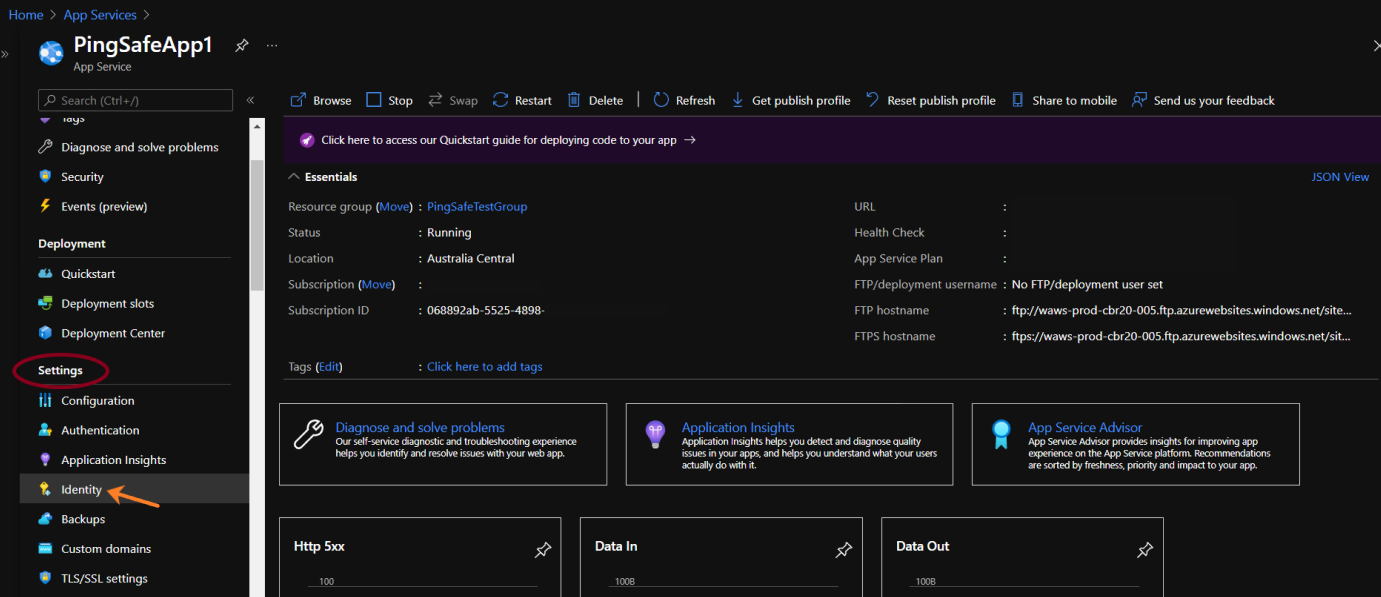
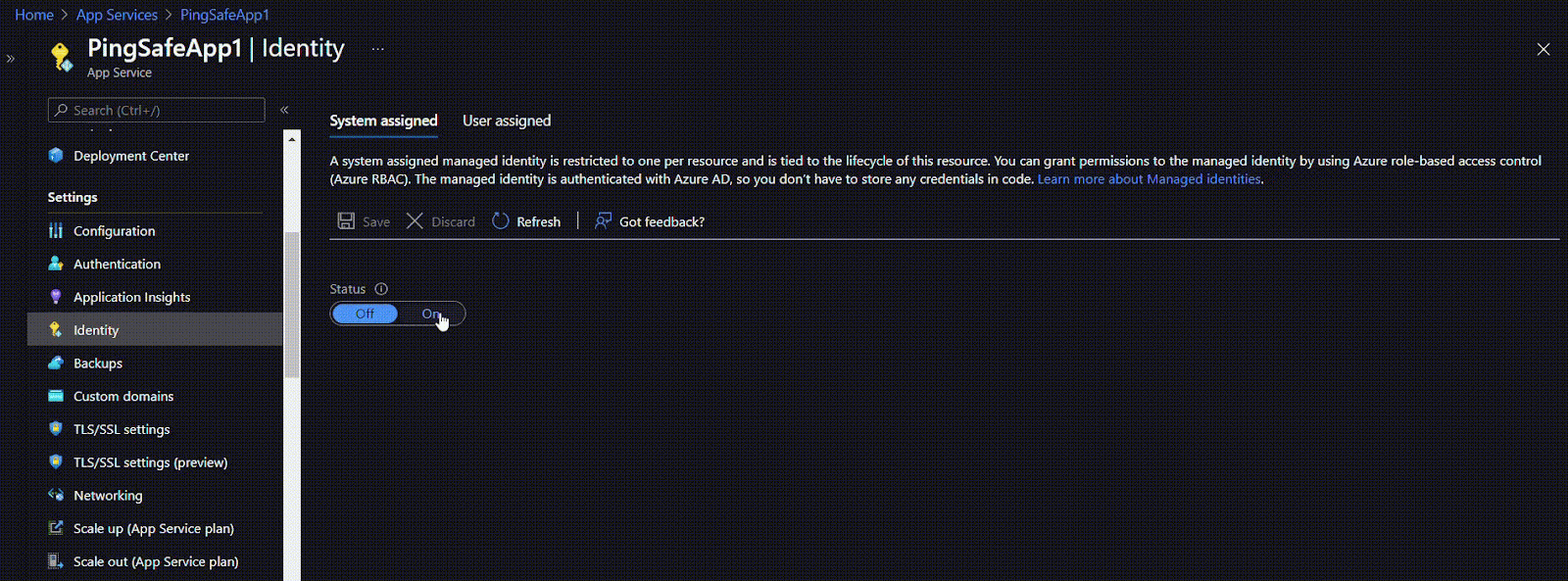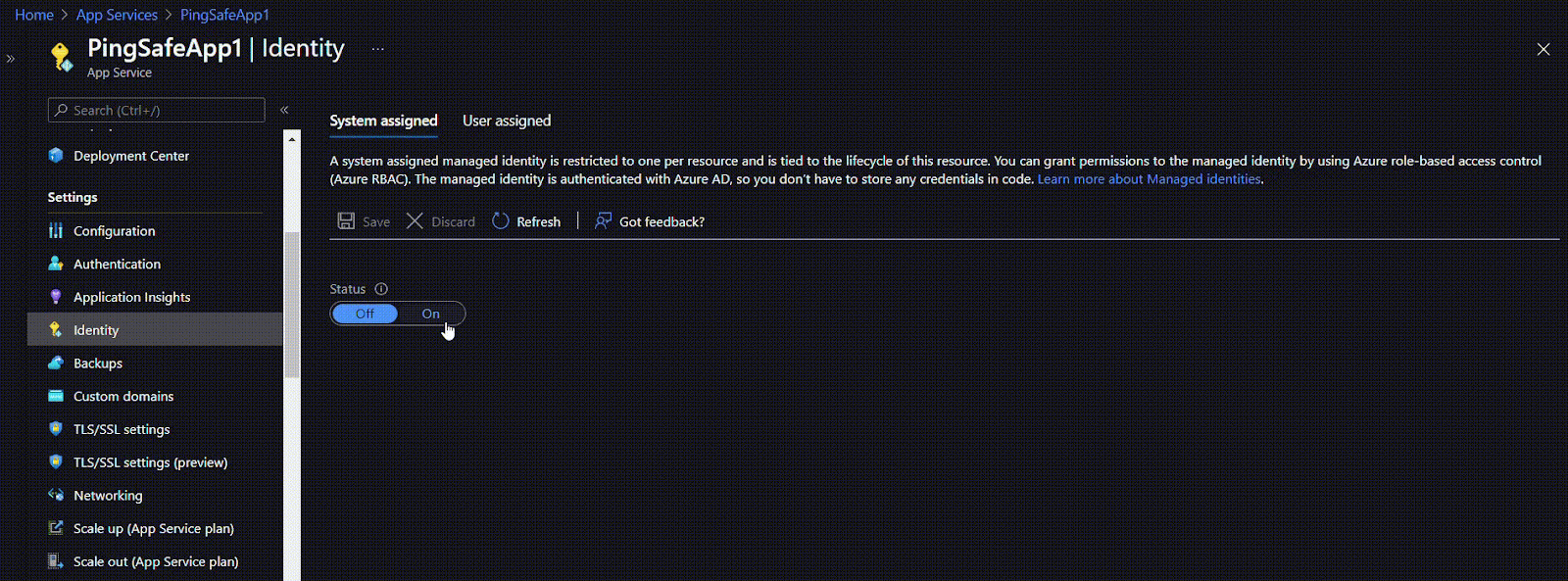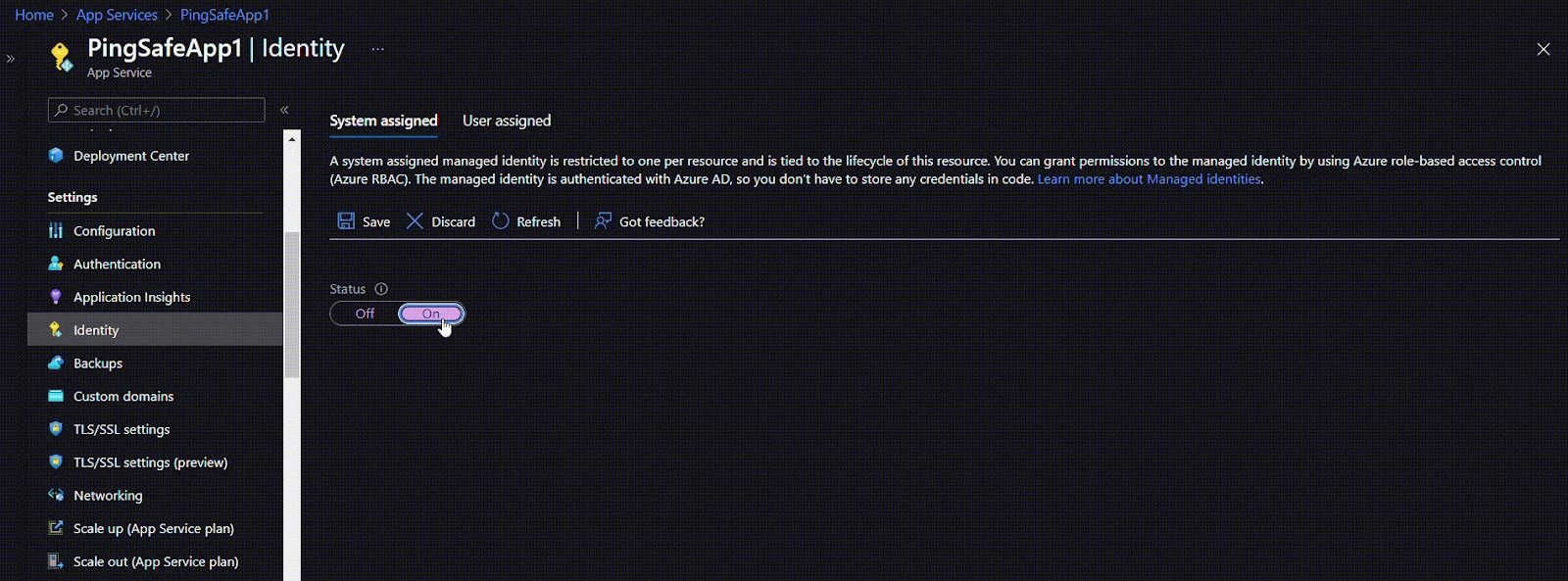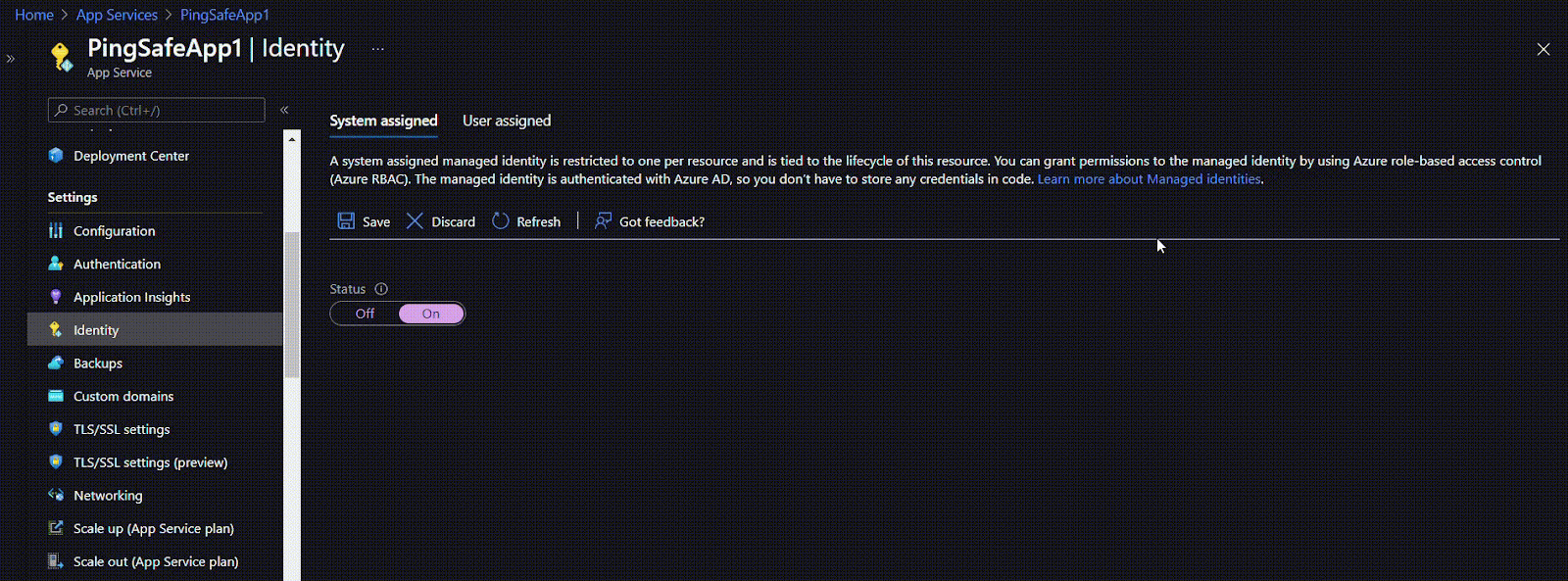
- Click on Identity under Settings from the navigation bar.
- If the Status is set to ‘Off’ follow the Steps to Remediation section.
- Repeat the process for other applications as well.
Steps for Remediation
- Login to azure portal.
- Click on App Services.

- Select an App Service plan from the listed apps.

- Click on Identity under Settings.

- If the Status is set to ‘Off’, click the ‘On’ button to enable the user managed identity for your application.
- Repeat the steps for other applications as well.
Please feel free to reach out to support@pingsafe.ai with any questions that you may have.
Thanks
PingSafe Support