Insecure Role Policies
This plugin guarantee that IAM role policies with particular rights are appropriately scoped.
Risk Level: Medium
Description:
This plugin guarantee that IAM role policies with particular rights are appropriately scoped. IAM roles policies should be targeted at least private access and the usage of wildcards should be prevented.
SentinelOne CNS strongly recommends ensuring all IAM roles are scoped to specific services and API calls.
Configuration Parameters
Ignore Identity Federation Roles: In case the Identity Federation Roles has statements including “Action” with "sts:AssumeRoleWithWebIdentity" or "sts:AssumeRoleWithSAML" and the Ignore Identity Federation Roles parameter value set as true then in that case CNS does not create any issue regarding it. Also, except for the AWS managed Administrator policy, CNS won’t scan any of the AWS managed policies if the Ignore AWS-Managed IAM Policies parameter is set to true.
About the Service :
AWS ID and Access Management (IAM) allows you to securely manage access to AWS services and resources. With IAM, AWS users and groups can be established and managed and permissions used to enable access by AWS resources and prohibit them.
We can discover and adjust the rules so that only the services are accessible. We can thus adhere better to the less privileged principle.
Impact :
The absence of the right policies will result in unauthorized access and this can prove to be lethal for any organization. Malicious users can easily gain access to resources and even tamper with them.
Steps to reproduce :
- Login to AWS Management Console.
- Navigate to the IAM dashboard.
https://console.aws.amazon.com/iam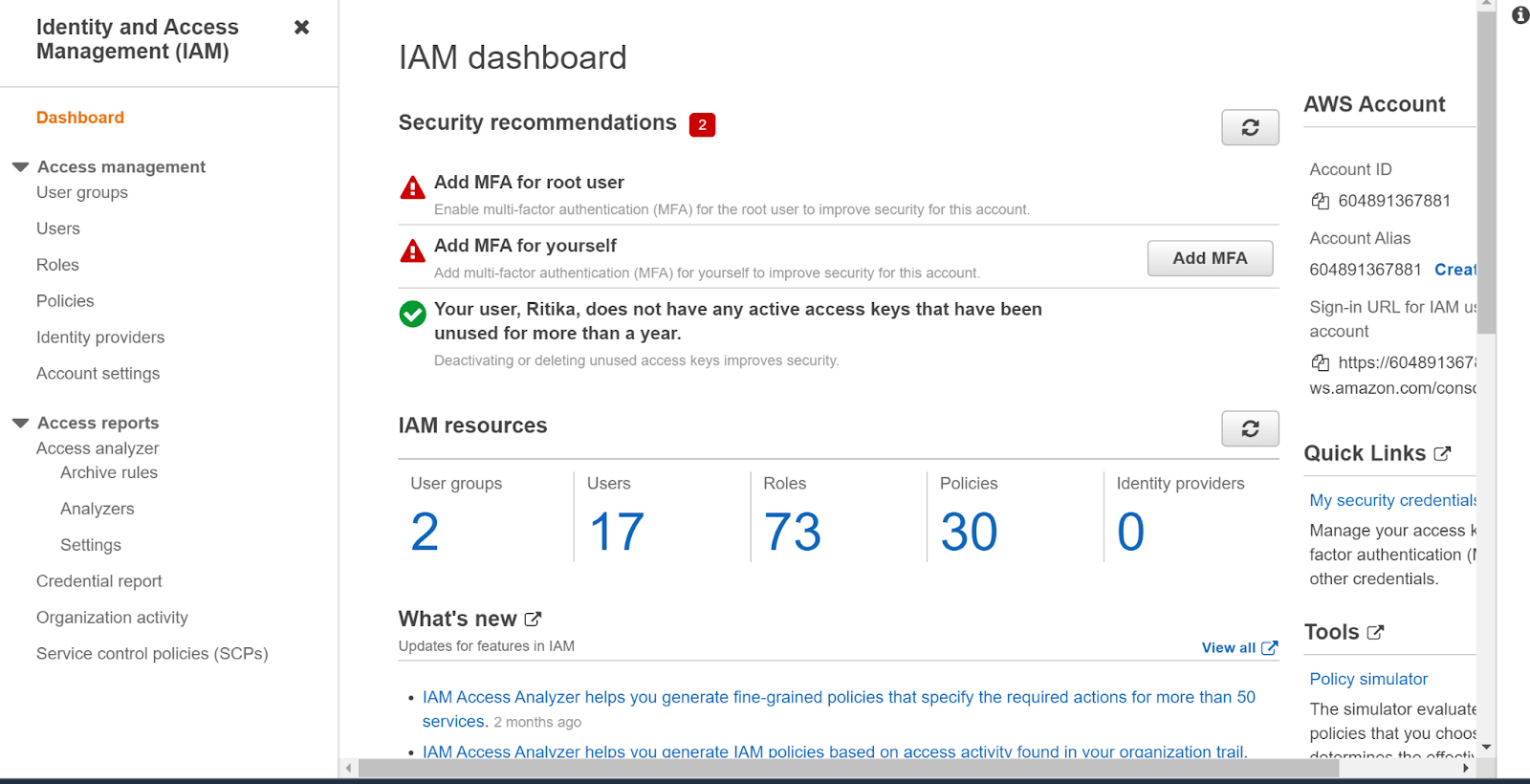
- Click on Roles in the left navigation panel under the Identity and Access Management (IAM) heading
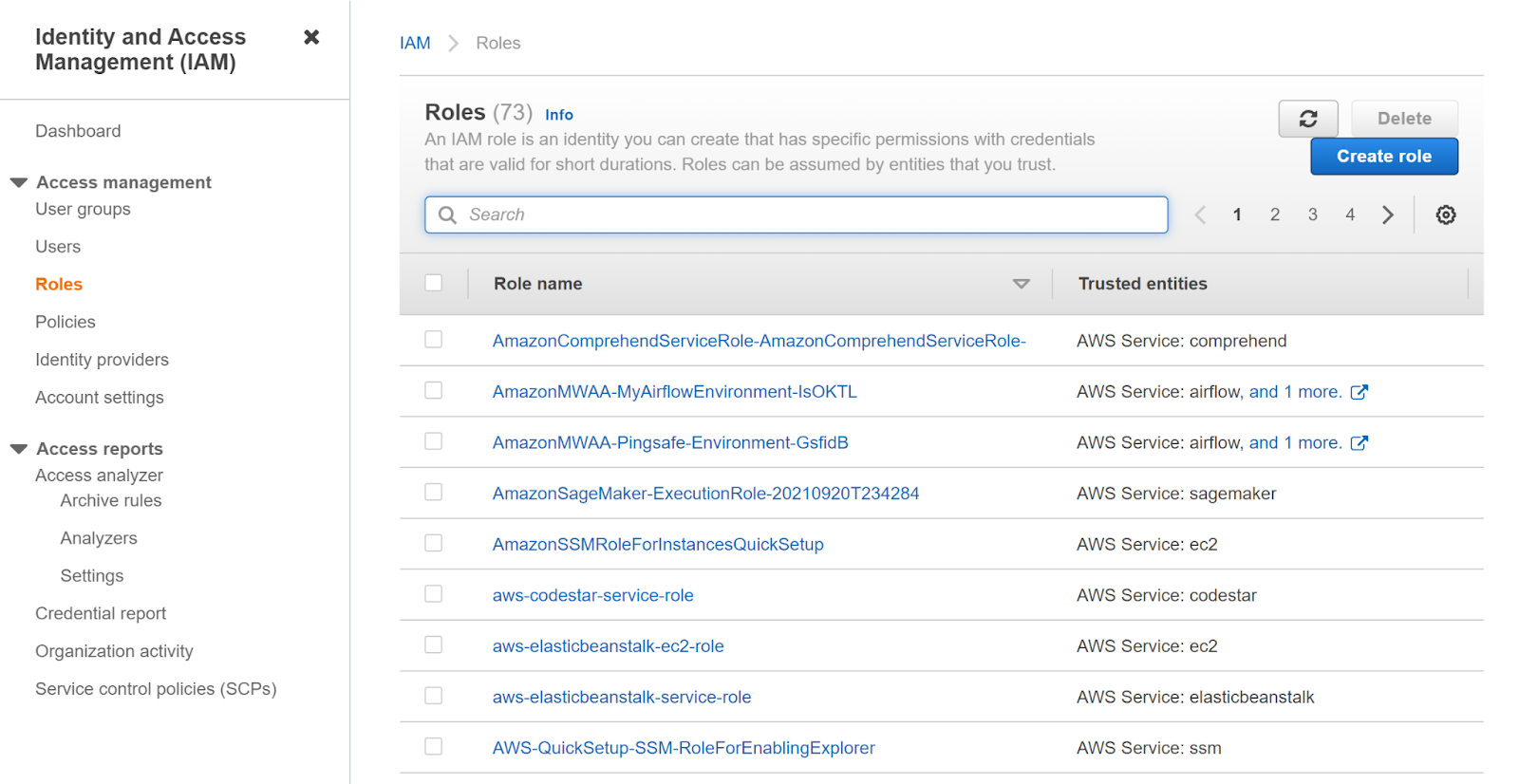
- Click on the role you want to examine.
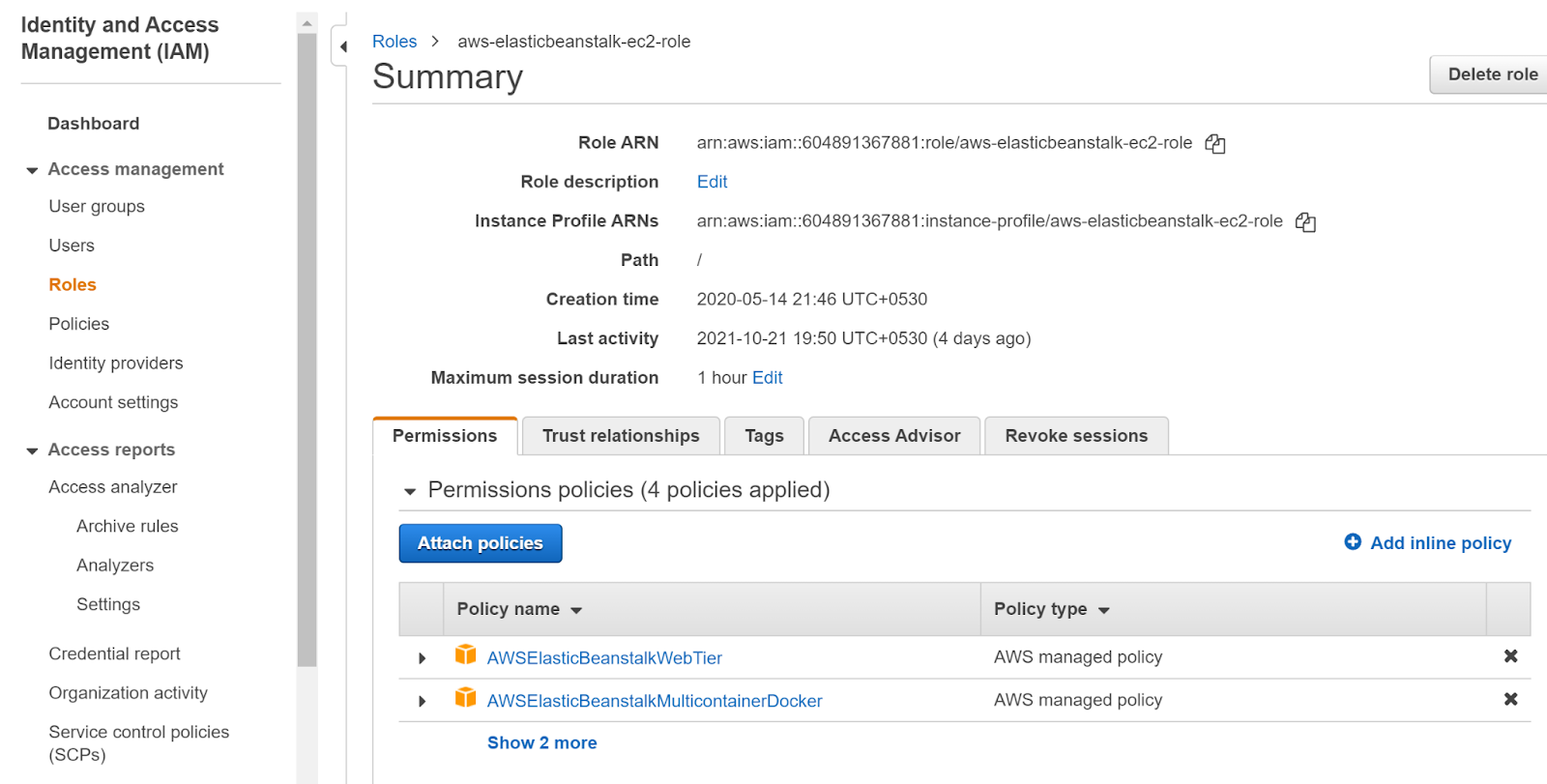
- Under the Permissions tab click on any of the policies to examine that policy.
- Identify the current value of the Action element and Resource element. When the element value is set to "*" the AWS resource(s) as stated in the policy statement can carry out all current actions and the IAM policy is consequently excessively permissive.
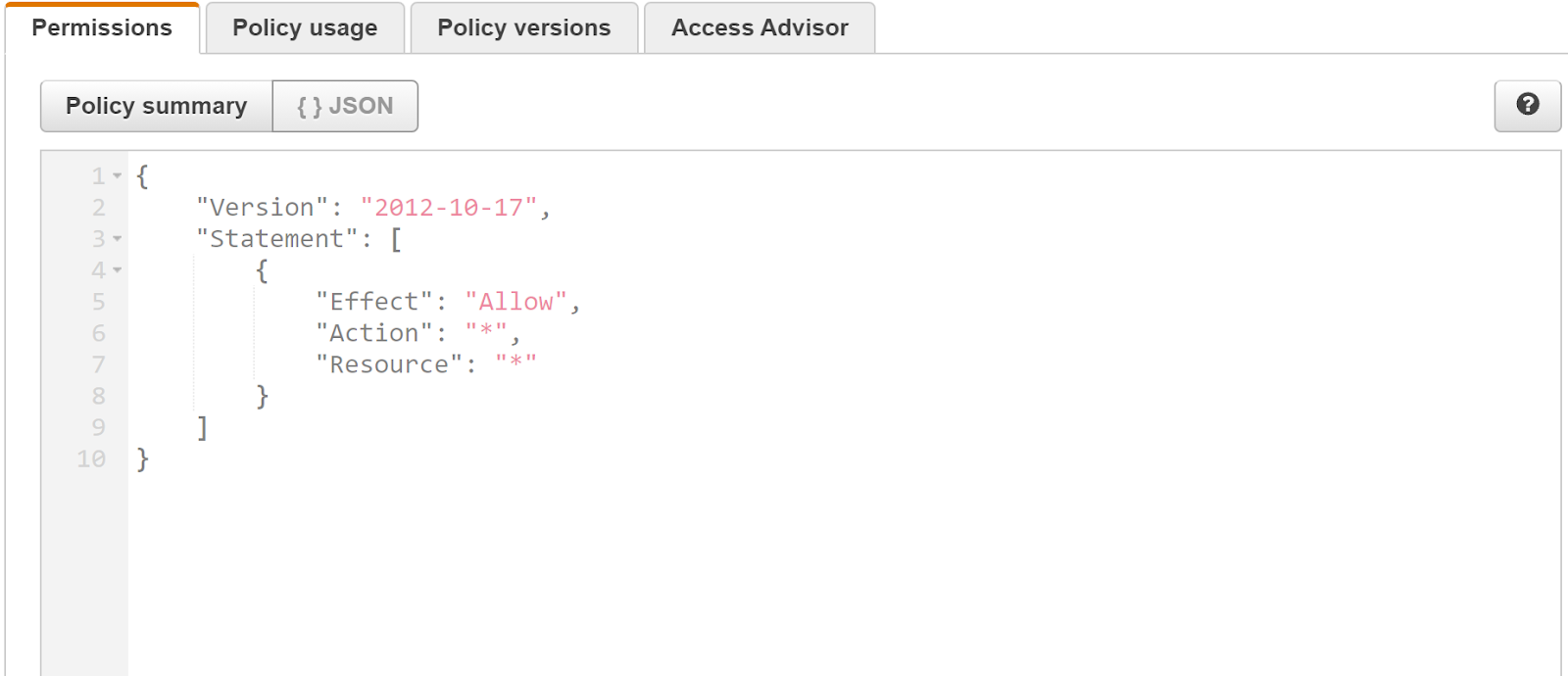
- Repeat the steps to check the same for other roles.
Steps for remediation :
- Login to AWS Management Console.
- Navigate to the IAM dashboard.
https://console.aws.amazon.com/iam
- Click on Roles in the left navigation panel under the Identity and Access Management (IAM) heading

- Click on the role you want to examine.

- Under the Permissions tab click on any of the policies to examine that policy.
- Identify the current value of the Action element and Resource element . When the element value is set to "*" the AWS resource as stated in the policy statement can carry out all current actions and the IAM policy is consequently excessively permissive. The same stands if Wildcards are present.

- Update the Action element and Resource element with specific actions based on your requirement.
- Next, click on Validate policy and then Save Changes.
- Repeat the steps to check the same for other roles.
References: