Lambda Function Public Access
This plugin ensures AWS Lambda functions cannot be accessed globally.
Risk Level: High
Description
This plugin ensures AWS Lambda functions cannot be accessed globally. Lambda resource-based policies state actions that can be performed by specific users. It is recommended never to expose Lambda functions via such policies unless absolutely necessary.
Configuration Parameters
Lambda Policy Allowed Condition Keys: This parameter denotes all the AWS IAM condition keys that are allowed. An alert is generated if any keys apart from the allowed keys are granted public access.
By default, the keys allowed are ‘aws:PrincipalArn’, 'aws:PrincipalAccount', 'aws:PrincipalOrgID', 'aws:SourceAccount', 'aws:SourceArn', 'aws:SourceOwner', 'kms:CallerAccount', and 'kms:ViaService'. Therefore it will return a vulnerability if any of the key apart from the ones mentioned are publicly accessible.
About the Service
AWS Lambda: AWS Lambda is a serverless compute service that allows you to run code without having to provision or manage servers, create workload-aware cluster scaling logic, keep event integrations up to date, or manage runtimes. You can use Lambda to run code for almost any form of application or backend service, and you don't have to worry about managing it. Simply upload your code as a ZIP file or container image, and Lambda will automatically and precisely assign compute execution power and run your code in response to incoming requests or events, at any scale.
Impact
With resource-based policies, you can grant an account permission to invoke or manage an AWS Lambda function. But, by providing public access, any anonymous user can access the lambda function. This vulnerability can be exploited by an attacker which can result in data exposure and unexpected charges for your AWS account.
Steps to Reproduce
Using AWS CLI-
1. Configure the AWS CLI with your account credentials.
2. List all the functions in the region by running the list-function command as:
aws lambda list-functions --region <region>
3. A list of functions will be displayed. Note down the name of the function you wish to investigate.
4. Run the get-policy command for the function.
aws lambda get-policy --function-name <function_name> --region <region>
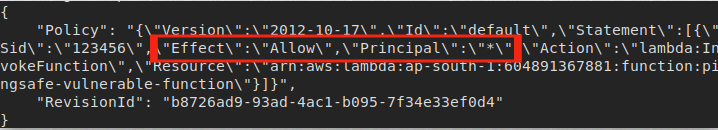
5. If any resource policy is attached to the function, it will return an array of policy statements as the output.
6. Examine the statements. If any of the statement's Principal value is set to '*' or 'arn:aws:iam::*' and has Effect element set to "Allow", the action specified can be carried out by any AWS account. Also verify if there are any conditional statements securing the public exposure of the action.
7. Repeat the steps from 2 to 6 for all the AWS Lambda functions you wish to examine.
Steps for Remediation
Remove the vulnerable Lambda policy statement to prevent public access.
Using AWS CLI-
1. Configure the AWS CLI with your account credentials.
2. Run the remove-permission command which will remove the vulnerable statement.
aws lambda remove-permission --function-name <function_name> --statement-id <statement_id> --region <region>
3. Repeat the steps from 2 to 3 for all the vulnerable AWS Lambda functions resource-based policy statements.