Lambda With Invalid IAM Roles
This plugin verifies that IAM roles associated with Lambda functions are legitimate and available in your AWS account.
Risk Level: HIGH
Description:
This plugin verifies that IAM roles associated with Lambda functions are legitimate and available in your AWS account. For Lambda security best practices, AWS Lambda Functions should have the highest restrictive IAM permissions.
About the Service:
AWS Lambda is a serverless compute service that allows you to run code without having to provision or manage servers, create workload-aware cluster scaling logic, keep event integrations up to date, or manage runtimes. You can use Lambda to run code for almost any form of application or backend service, and you don't have to worry about managing it. Simply upload your code as a ZIP file or container image, and Lambda will automatically and precisely assign compute execution power and run your code in response to incoming requests or events, at any scale.
Impact :
In the absence of valid IAM roles associated with Lambda functions, there may be problems with the privileges of the users which can result in the compromise of the service. Hence, to avoid any such compromise or any such impacts IAM roles associated with Lambda function should be monitored.
Steps to reproduce :
- Sign in to your AWS console.
- Navigate to the Lambda dashboard at: https://console.aws.amazon.com/lambda/
- Select the Function you want to examine and visit its configuration page.
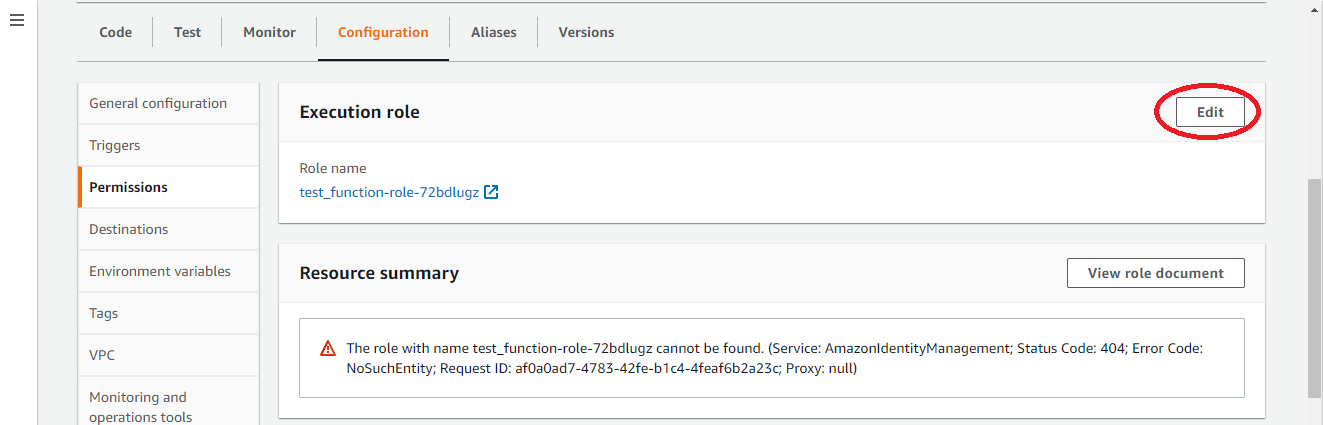
- Select the “ Configuration ” tab to view its setting panel.
- Click on the “ Edit ” button of the “ Execution Role ” panel.
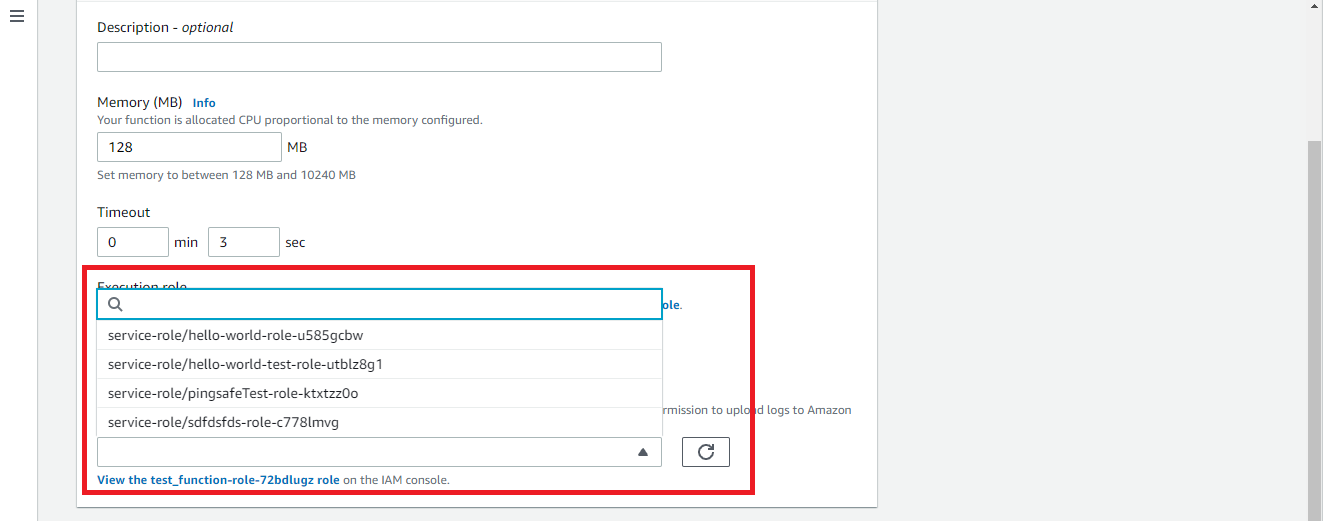
- Scroll down to the Existing role dropdown list and check if the function has an existing IAM role selected for it from the dropdown list.
- Open the selected IAM role in the new tab and check if it shows all the details regarding that IAM execution role.

Steps for remediation :
Attach a valid IAM role to the Lambda function to provide the minimal amount of access required to perform its tasks.
- Sign in to your AWS console.
- Navigate to the Lambda dashboard at: https://console.aws.amazon.com/lambda/
- Select the Function you want to examine and visit its configuration page.
- Select the “ Configuration ” tab to view its setting panel.
- Click on the “ Edit ” button of the “ Execution Role ” panel.

- Scroll down to the Existing role dropdown list and check if the function has an existing IAM role selected for it from the dropdown list.
- Open the selected IAM role in a new tab.
- If the web page shows that the execution role doesn’t exist, remove that execution role from the list and select a new and valid execution role for the chosen function.
References:
- https://docs.aws.amazon.com/lambda/latest/dg/lambda-intro-execution-role.html
- https://aws.amazon.com/lambda/faqs/