Policy Assignment Alerts Enabled
Risk Level- Medium
Description
The plugin checks that the Activity Log alerts for create or update and delete Policy Assignment events are enabled. Monitoring for create or update and delete Policy Assignment events gives insight into policy changes and may reduce the time it takes to detect suspicious activity.
About the Service
Alerts: Alerts in Azure in the most simple of terms can be termed as a notification centre for all the things in Azure. Users can create, view and manage all the alert rules from a single place including metric rules, log alerts and activity log alerts. Customized alerts can be created by selecting the alert target (can be resource, subscription or anything on their azure account), the rule condition managing action groups(specifications about actions to be taken whenever an alert is triggered). To sum up the entire basic process and working of the service, the user specifies the target, condition (logic or any condition when the alert should trigger) and action group. Azure monitors the provided target and when the specified conditions are met an alert is triggered and sent to the action group.
Impact
If the policy assignment alert rule is not created and enabled then the user will not be notified regarding the creation, changes or deletion of any policy assignment leading to mismanagement in the organization and missing important notifications regarding deletion or exemption of any compliance and policies which may lead to legal issues (eg. on October 2021 SBI was fined 1 crore Indian Rupees for not being RBI compliant) from authorities and vulnerabilities in the system.
Steps to Reproduce
- Login to the Azure account.
- From Azure services, select Alerts.
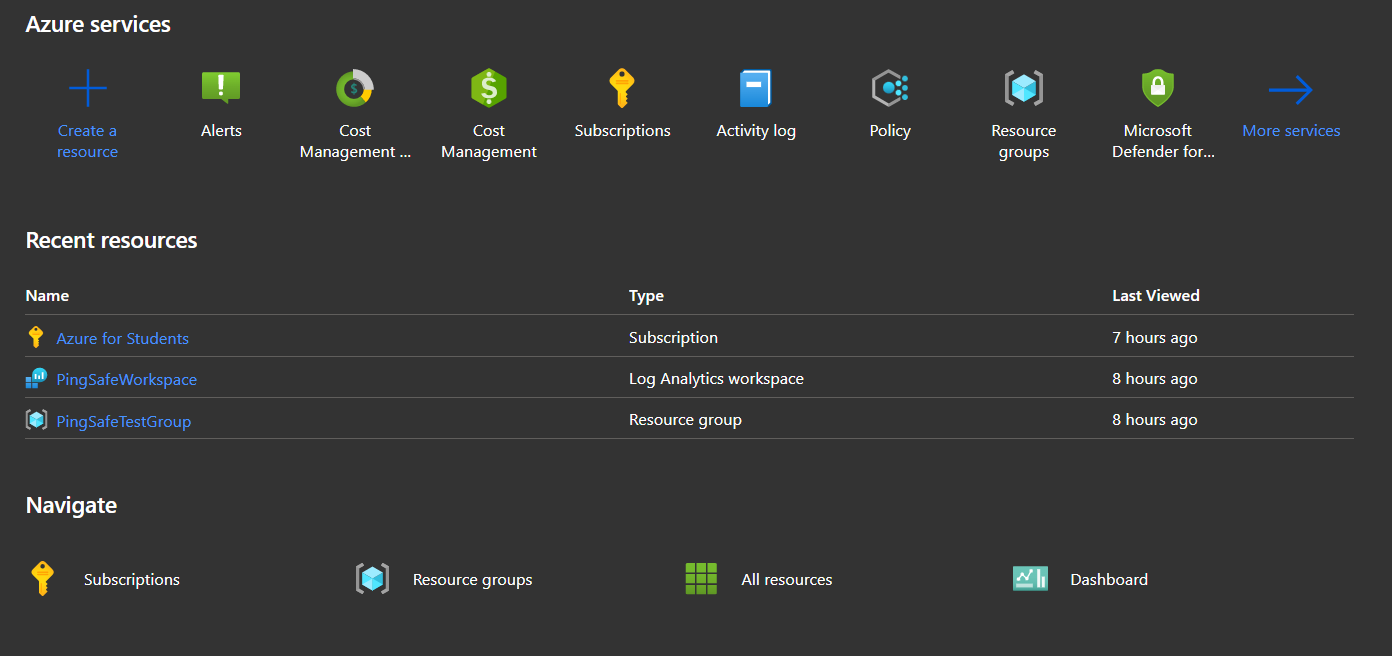
- The Alerts page will open, select the Alert rules option.
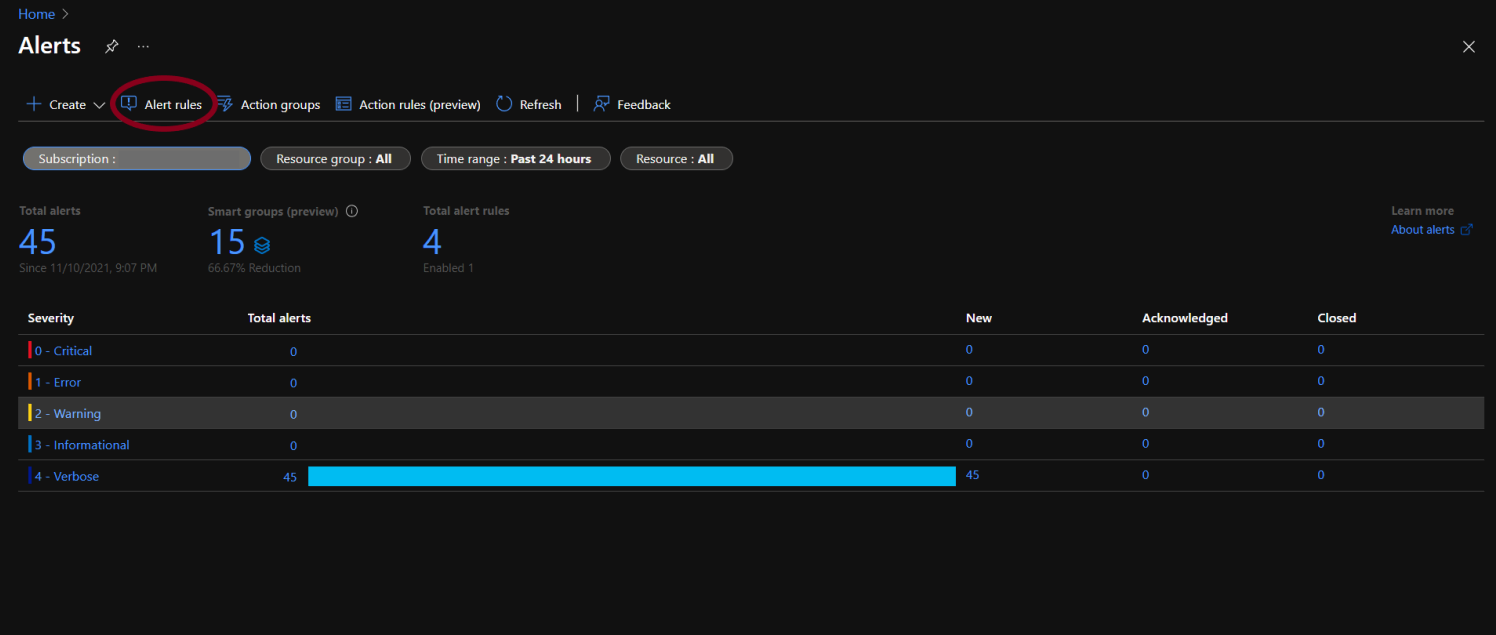
- The alerts rule page will appear. By default, only the enabled alert rules are shown on the screen.
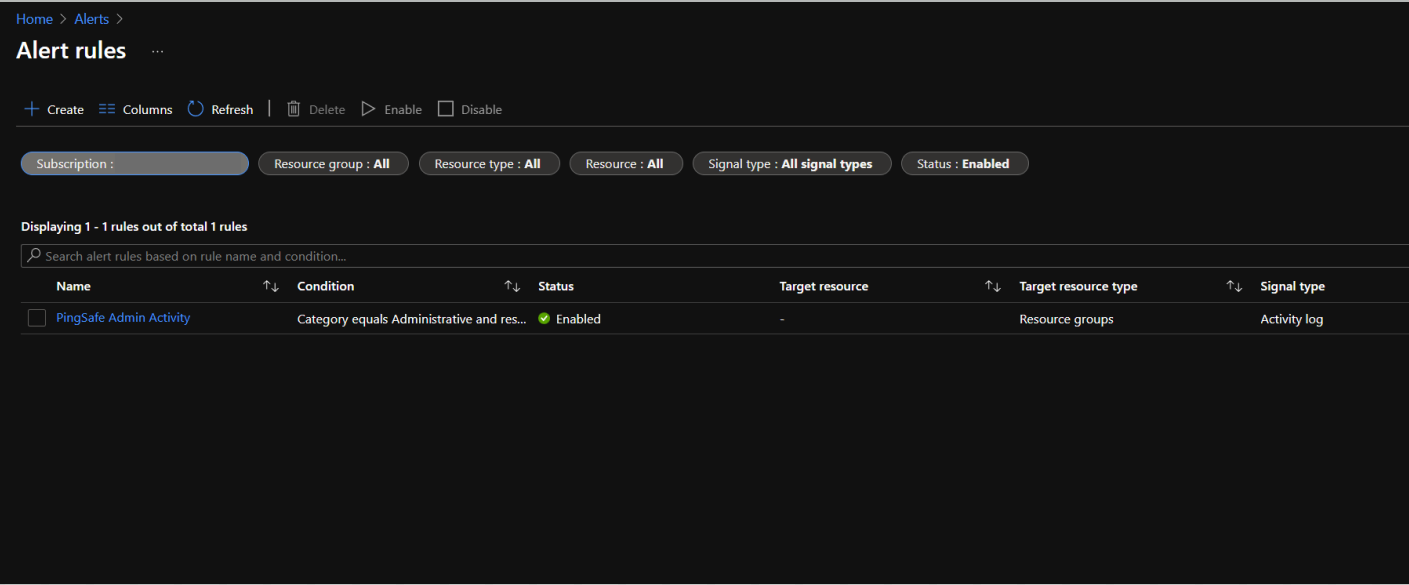
- To check the list of disabled alert rules as well, go to the Status option and click on Select all.
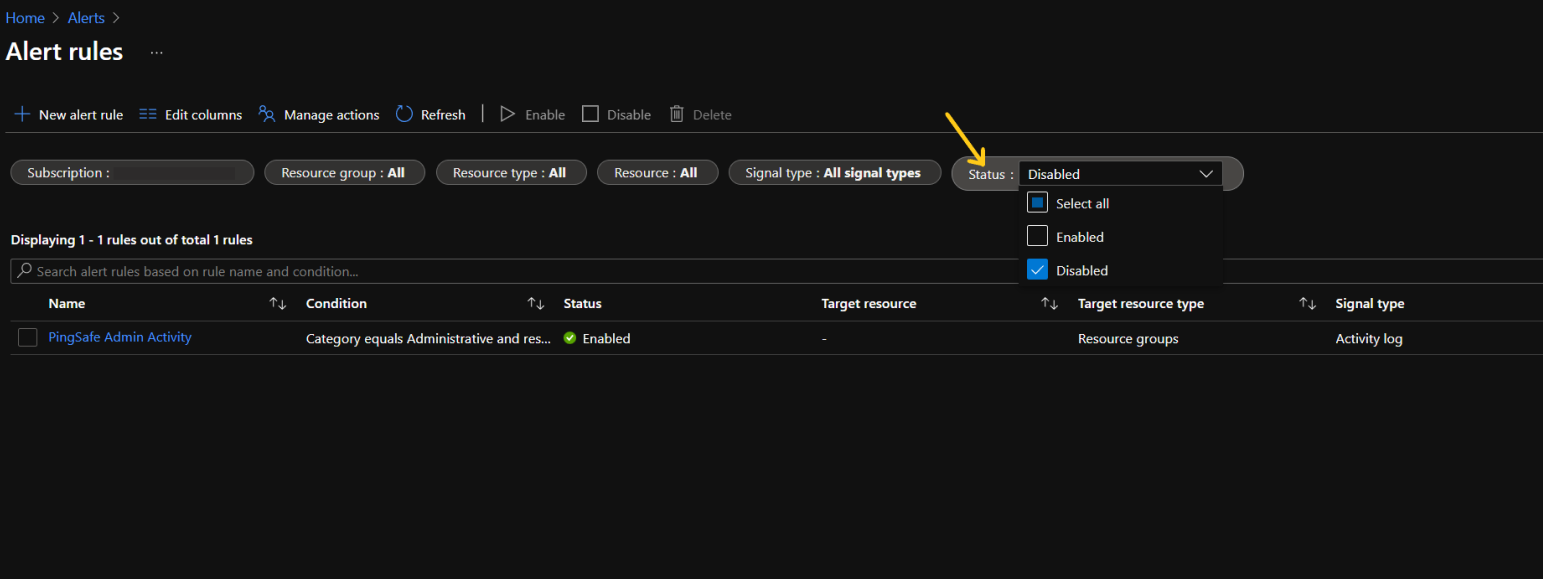
- Now we will check for 2 things:
- Whether the Policy Assignment rule is created.
- If the Policy Assignment alert is created then is it enabled.
- Search alert rules based on rule name:
- If the user remembers the security policy alert rule name, simply type it in the search bar given above the list of subscriptions.
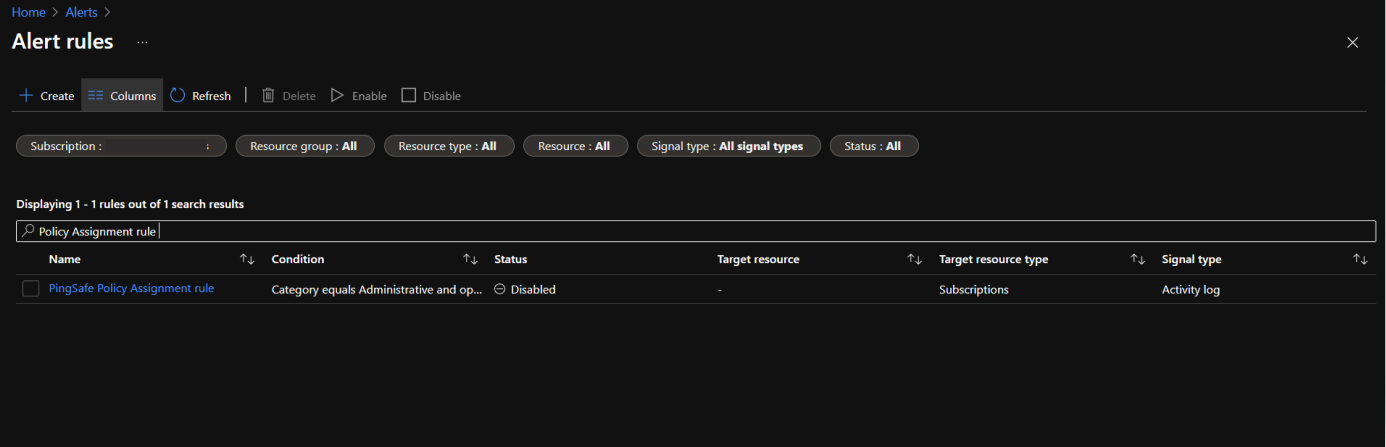
- Now check the status of the alert rule and check the Status. If the Status is set as Disabled, we need to enable it. To do so follow from steps under the Steps for Remediation section given next to the current section(Steps to reproduce).
- If the user remembers the security policy alert rule name, simply type it in the search bar given above the list of subscriptions.
- Search alert rules based on condition:
- In case the rule name is not known, in the search bar type ‘Microsoft.Authorization/policyAssignments/’.
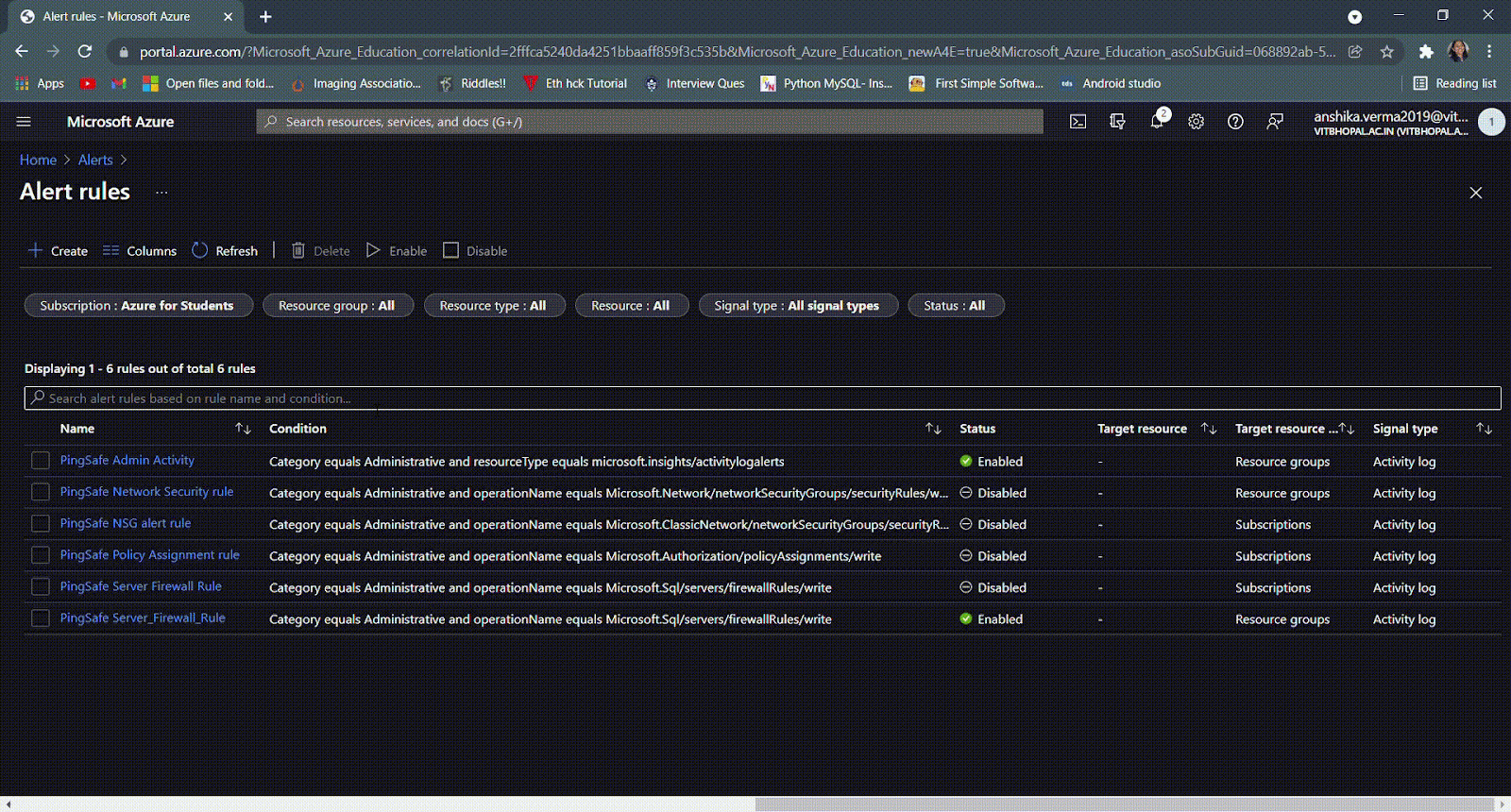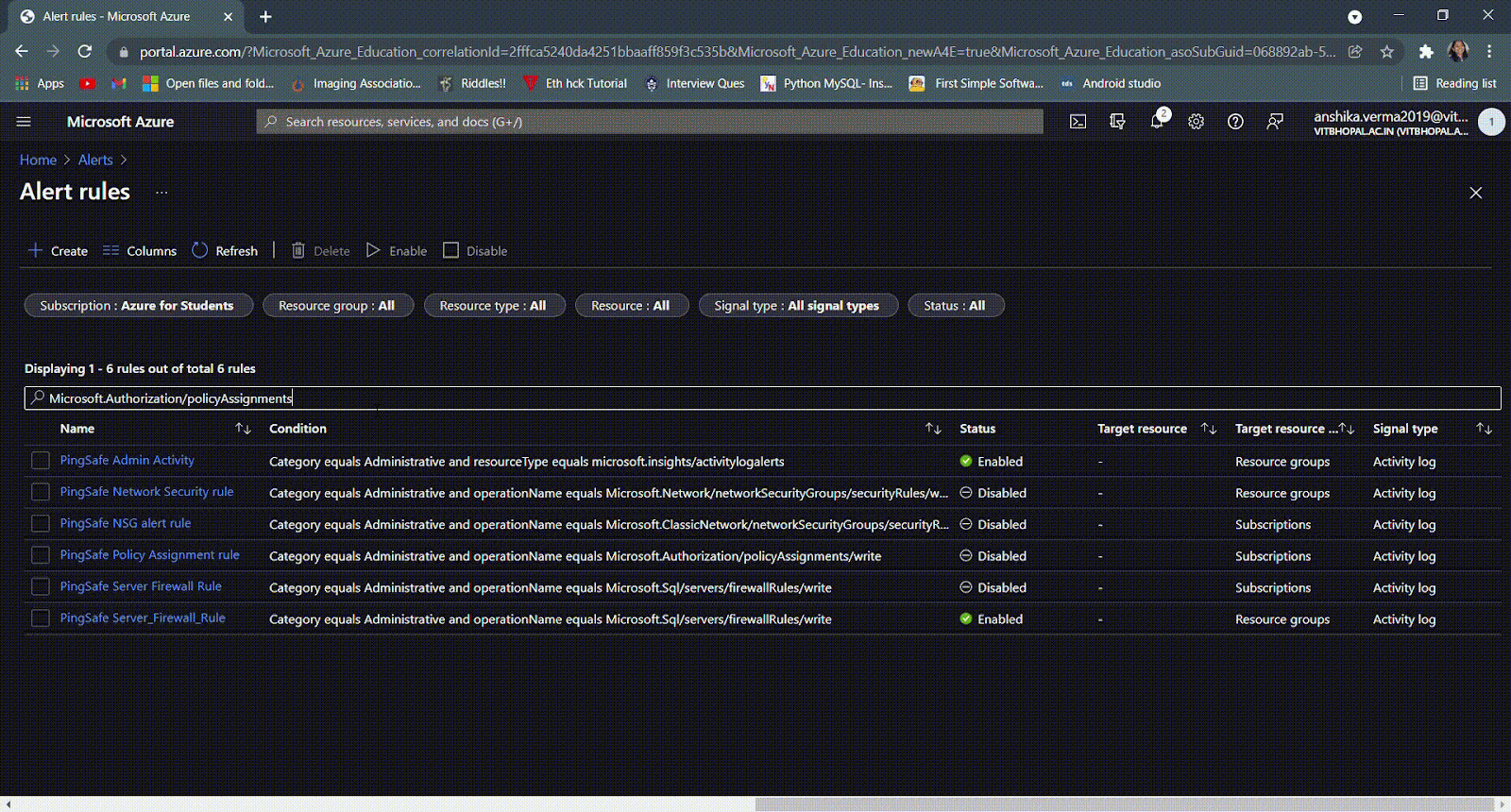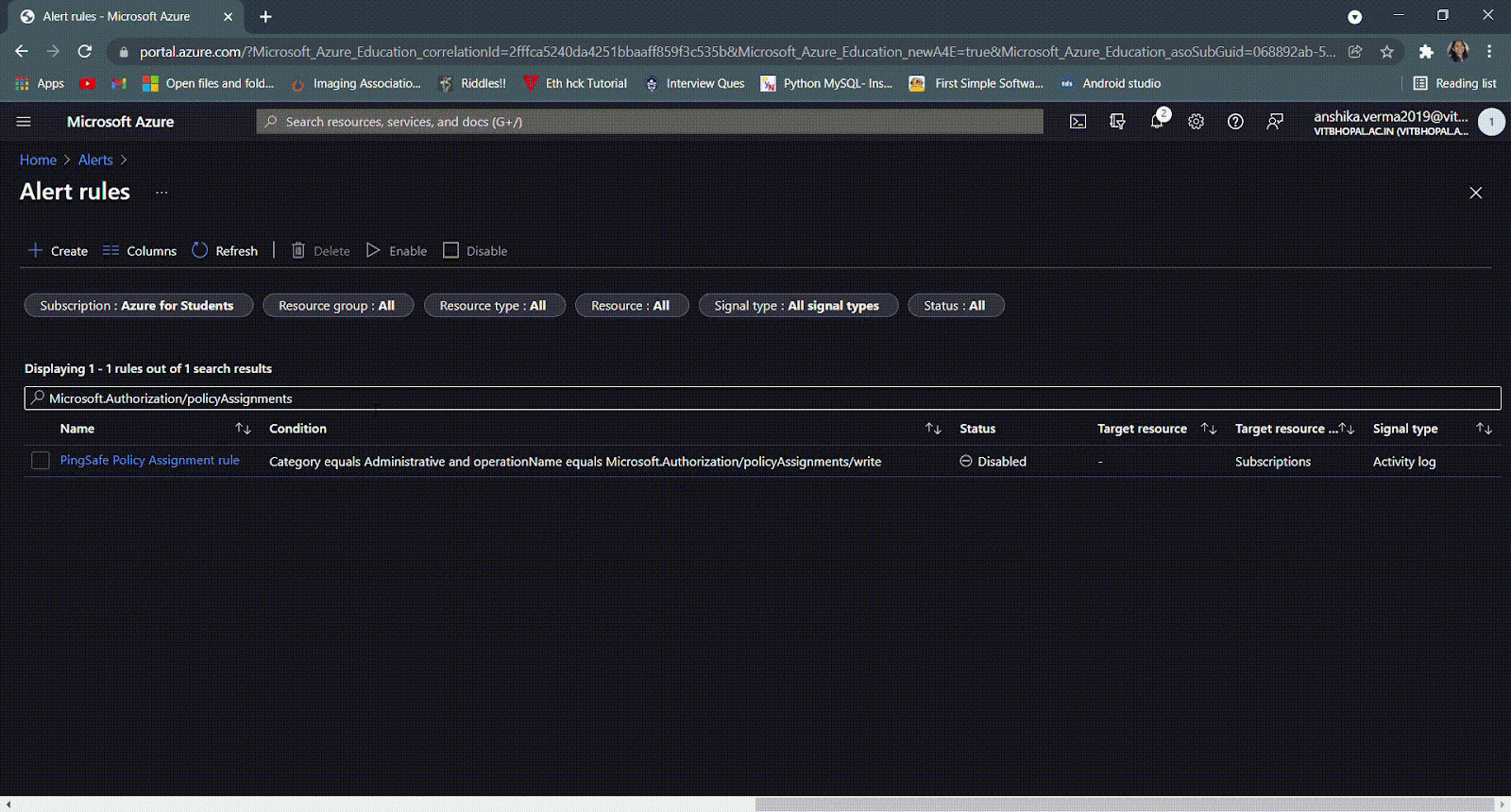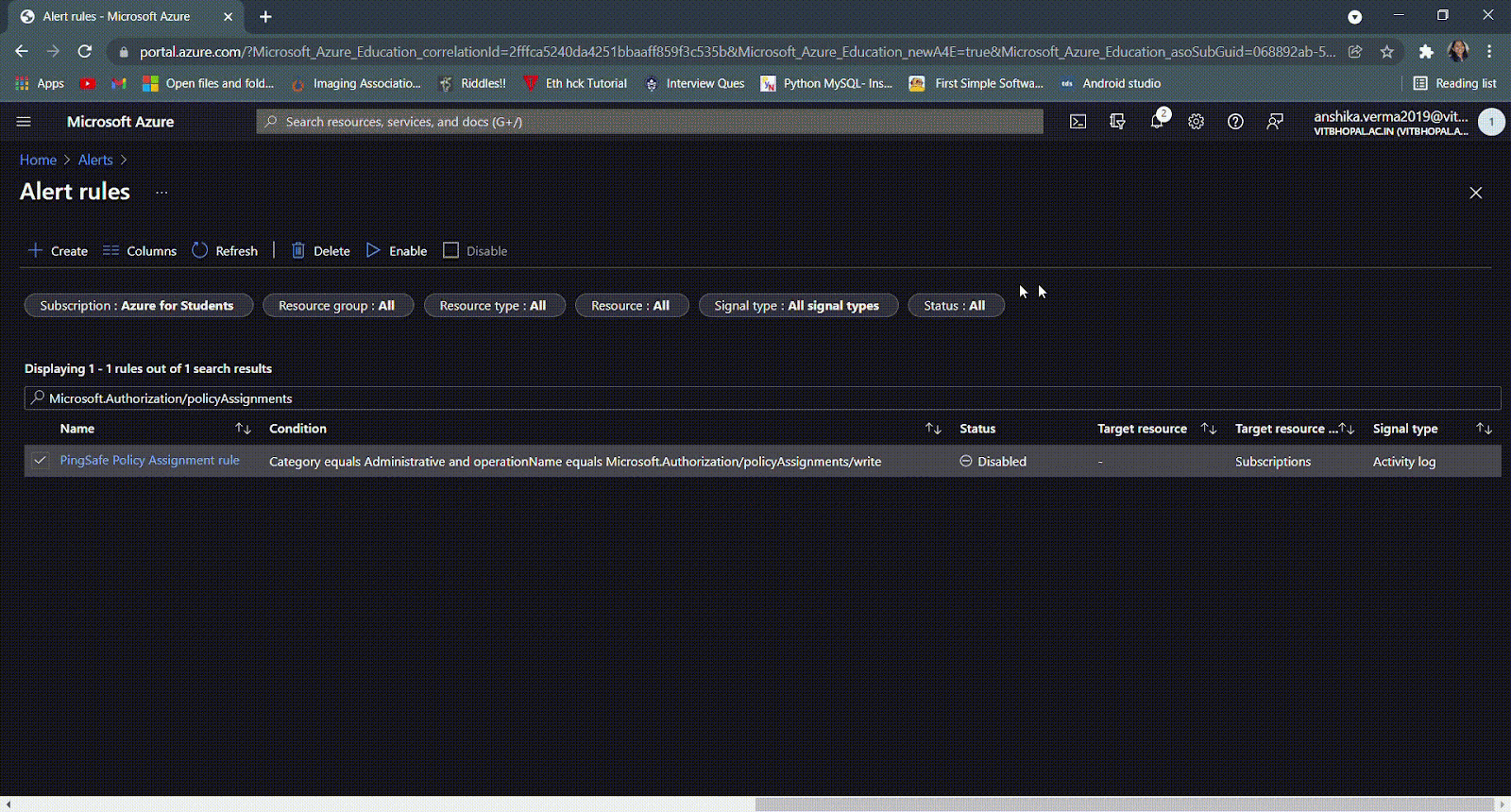
- If the status is set as Disabled then go to the Steps for Remediation section and follow the steps.
- Else, if the screen appears blank, we will have to create a Policy Assignment alert rule first. To check the steps of creating a Policy Assignment rule, click here.
- In case the rule name is not known, in the search bar type ‘Microsoft.Authorization/policyAssignments/’.
Steps for remediation
Create Alert Rule:
- Login to the Azure account.
- From Azure services, select Alerts.
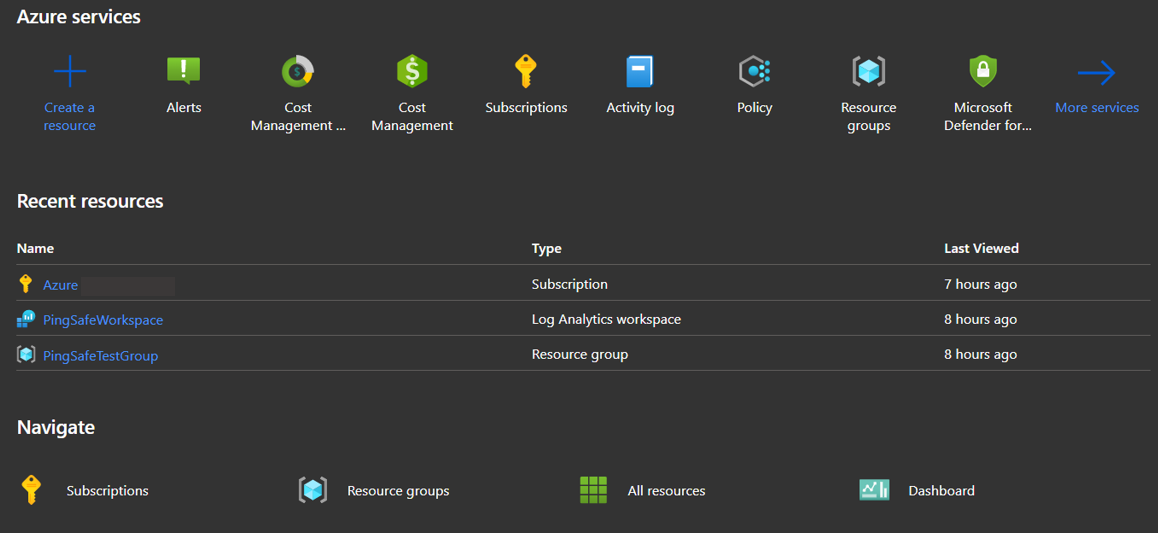
- The Alerts page will open. Click on Alert rules.
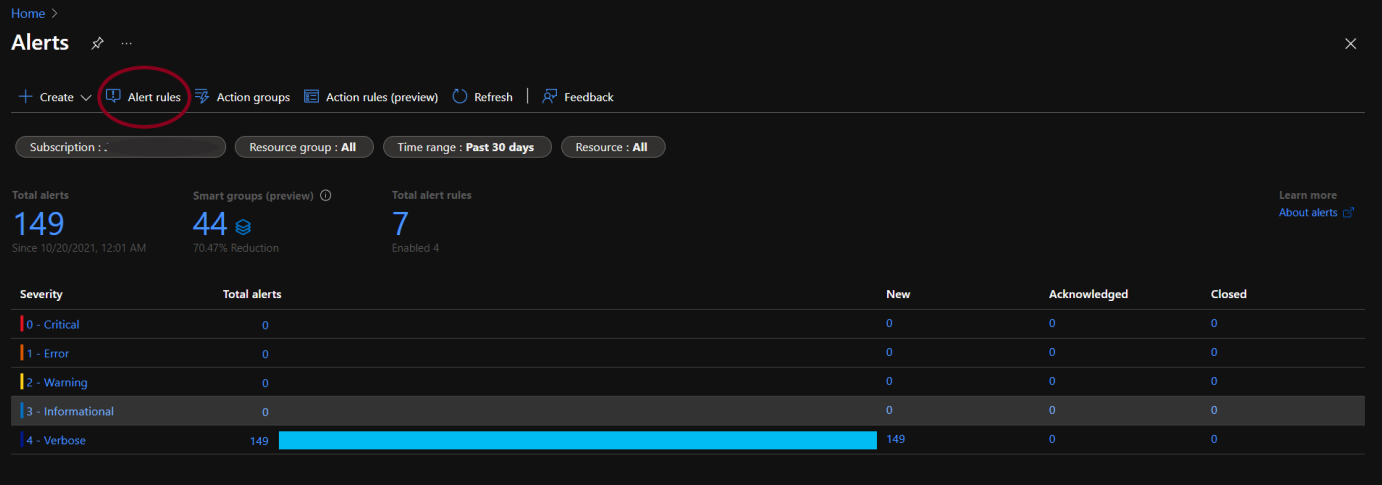
- Click on +Create.
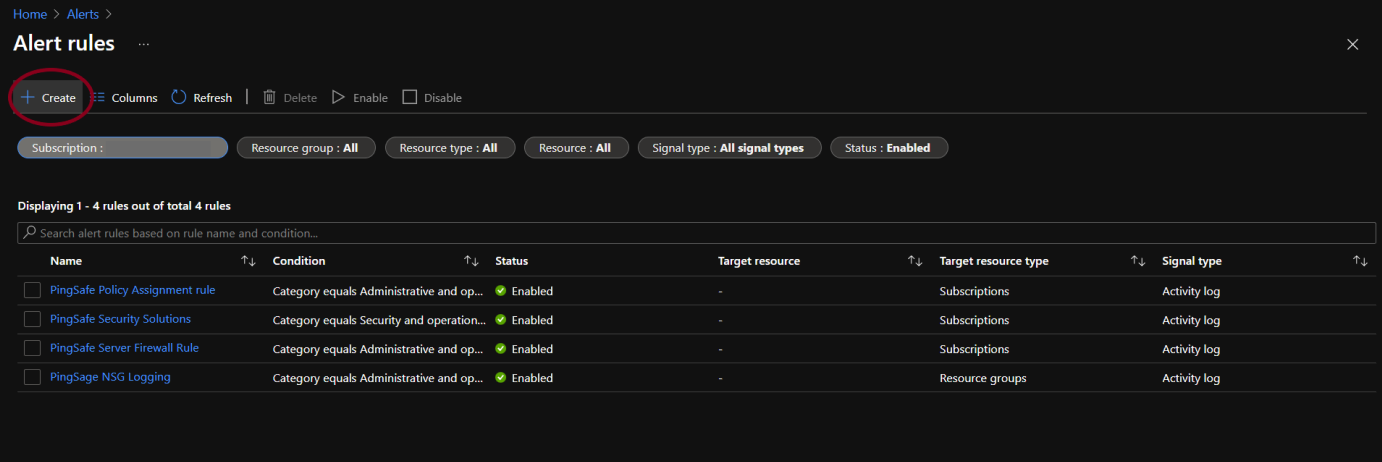
- Select the target resource by clicking on the Select Resource option.
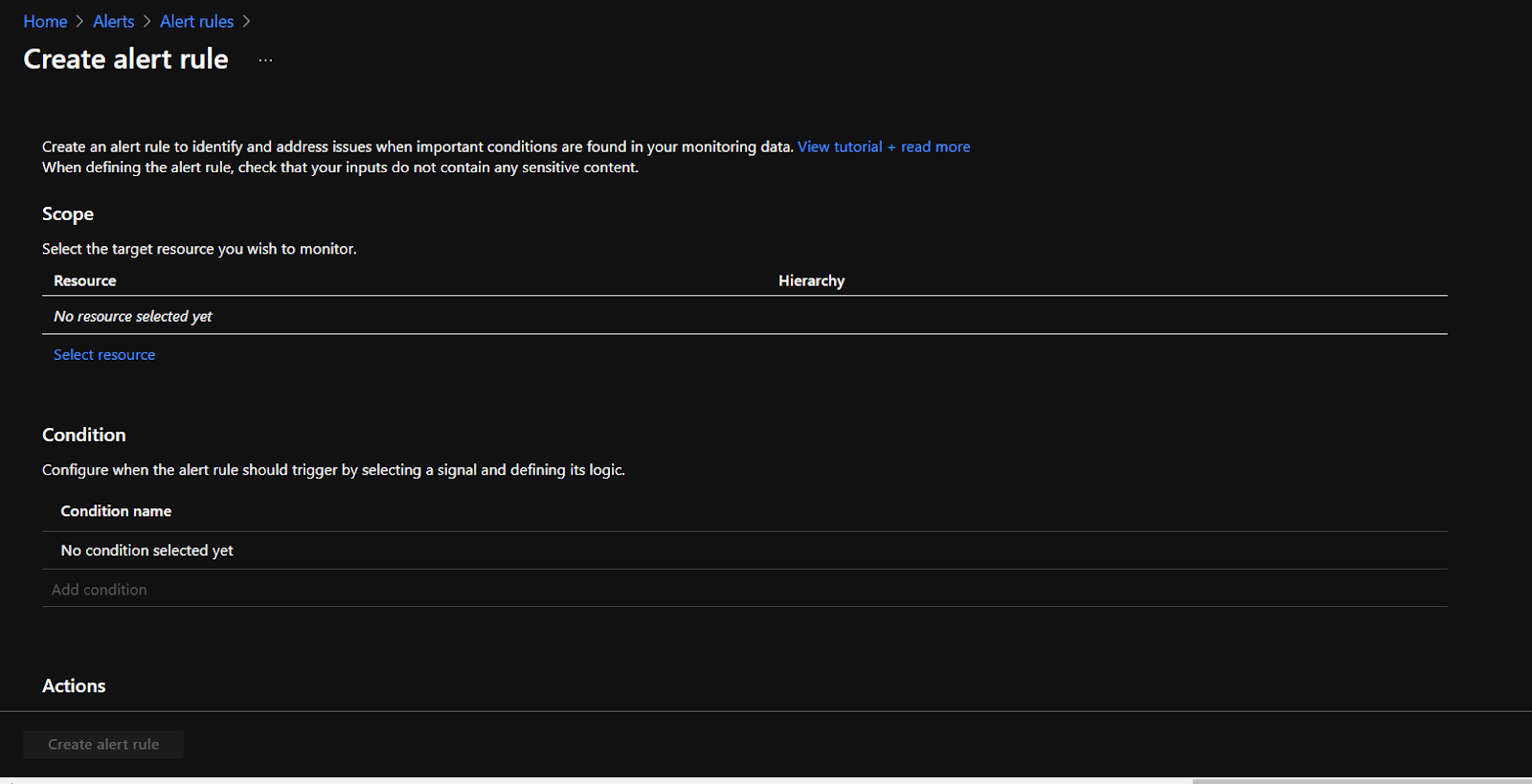
- Under the Conditions section, click on Add condition.
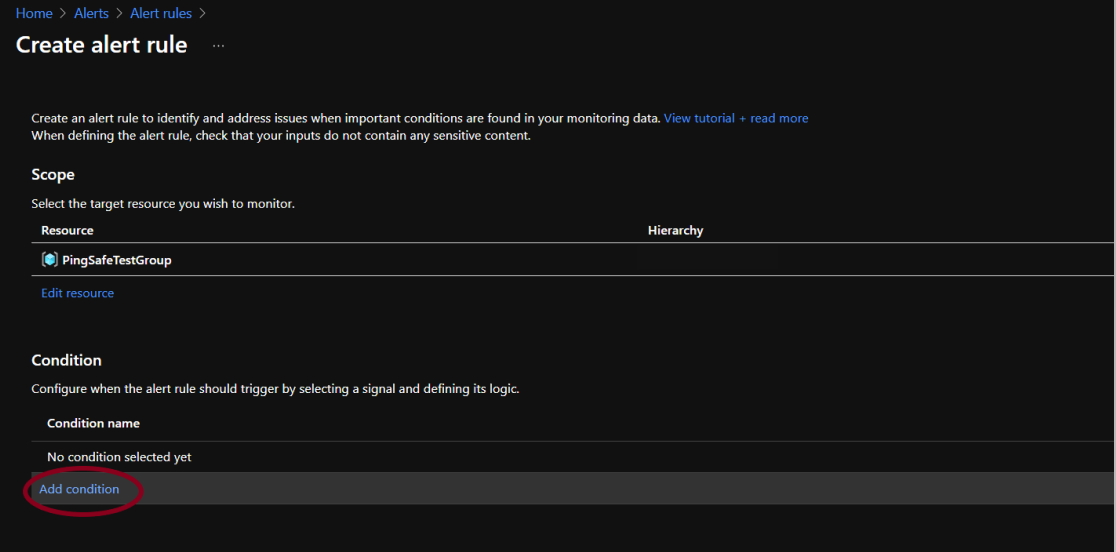
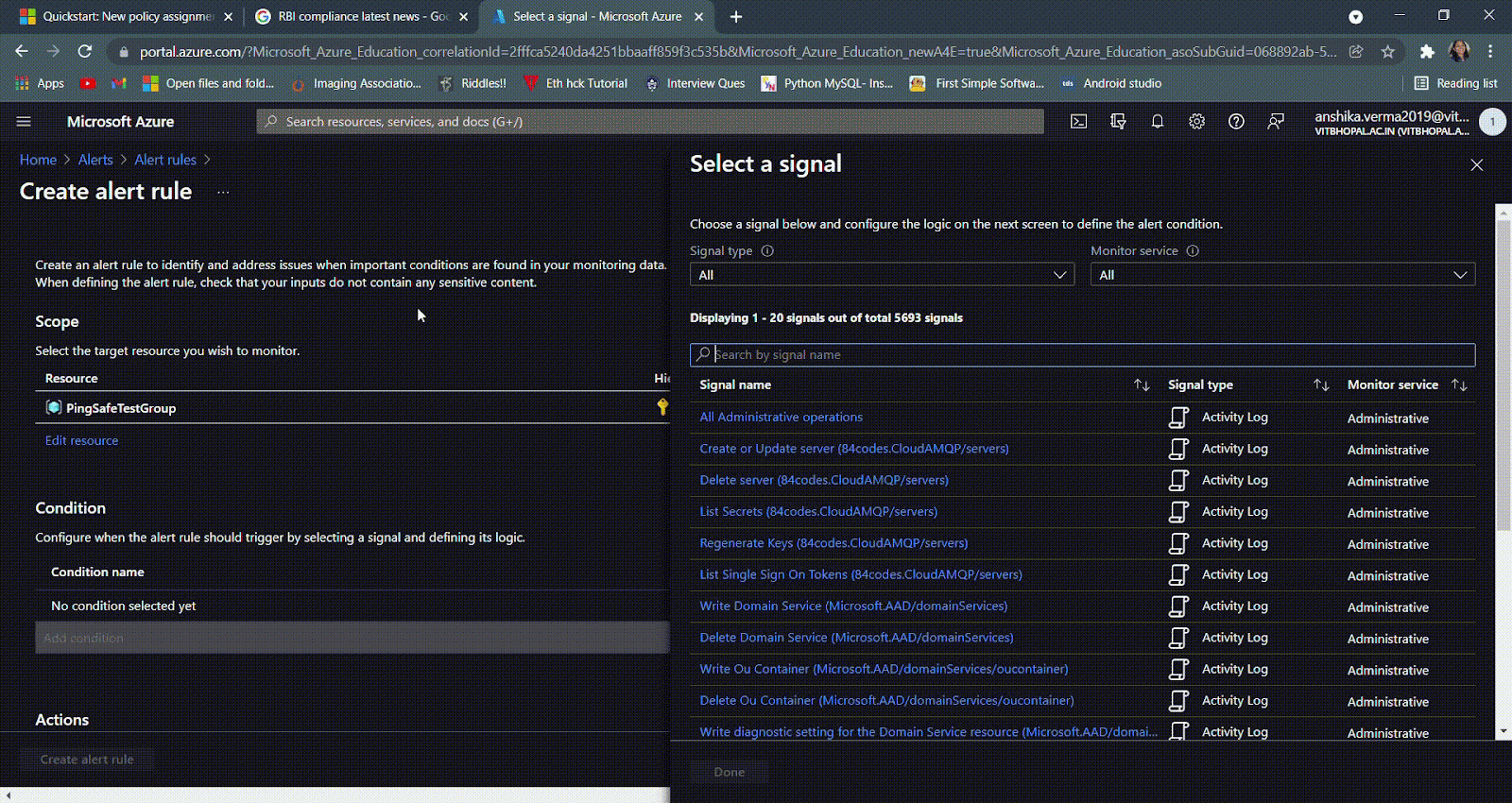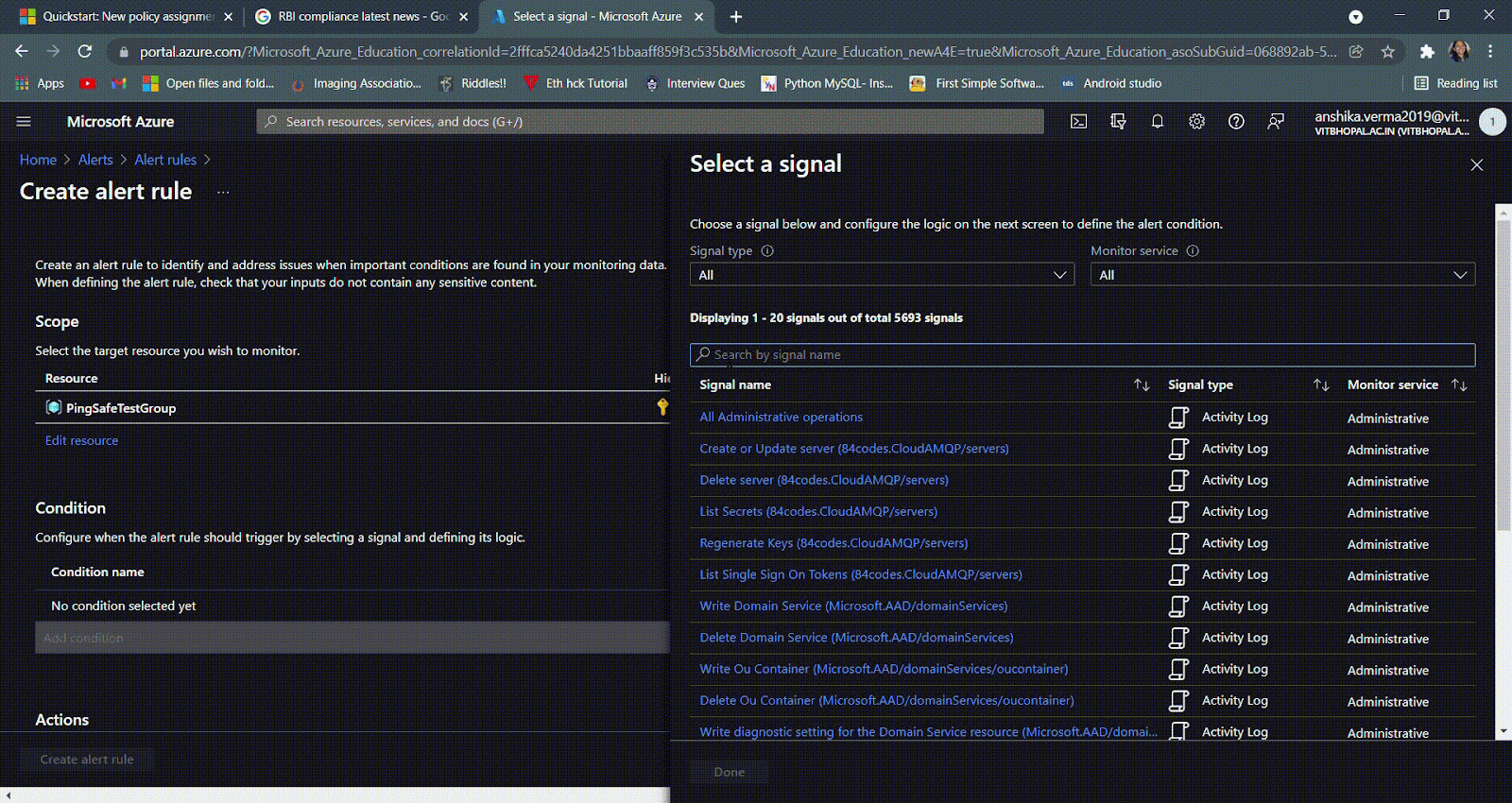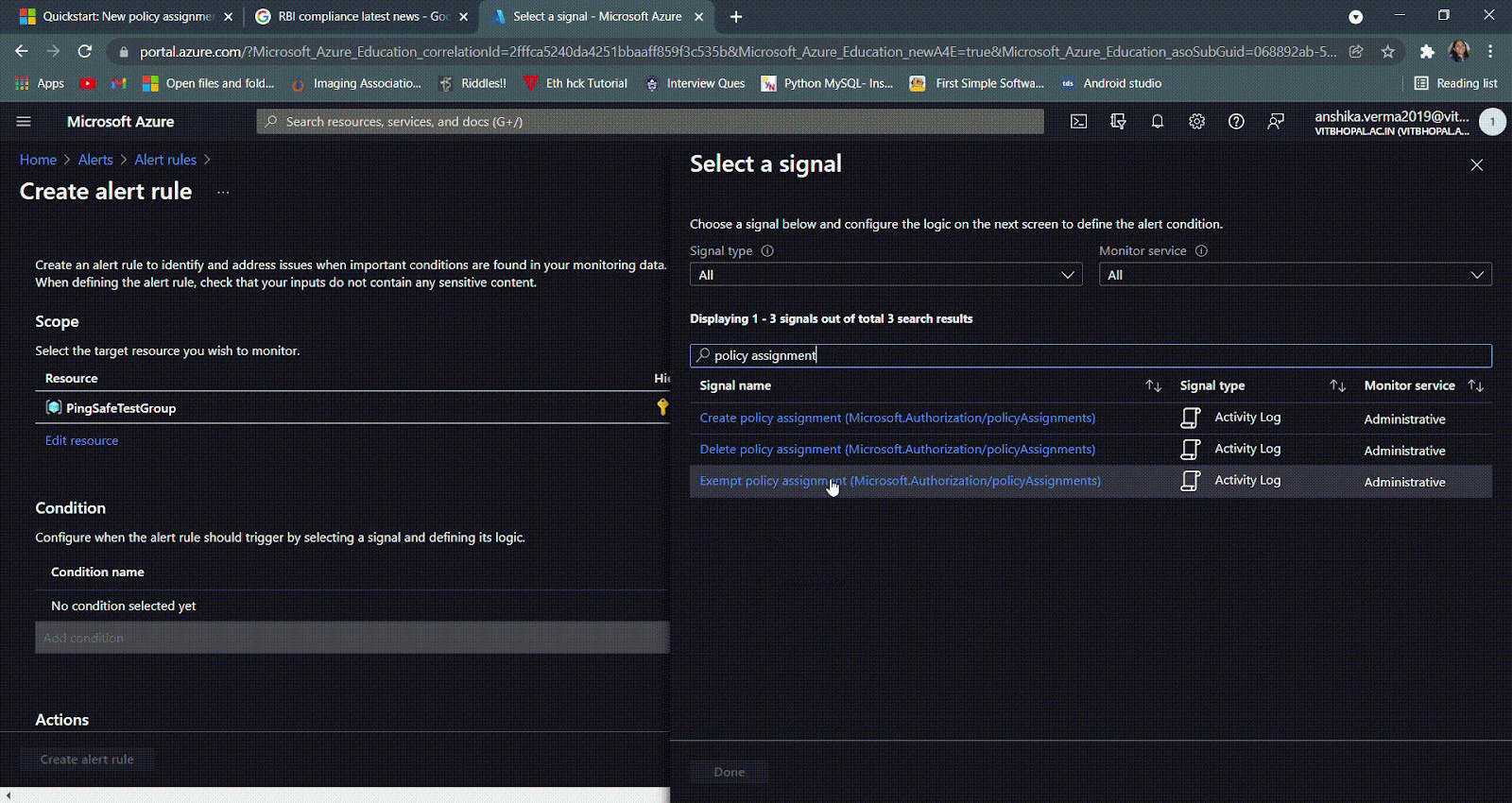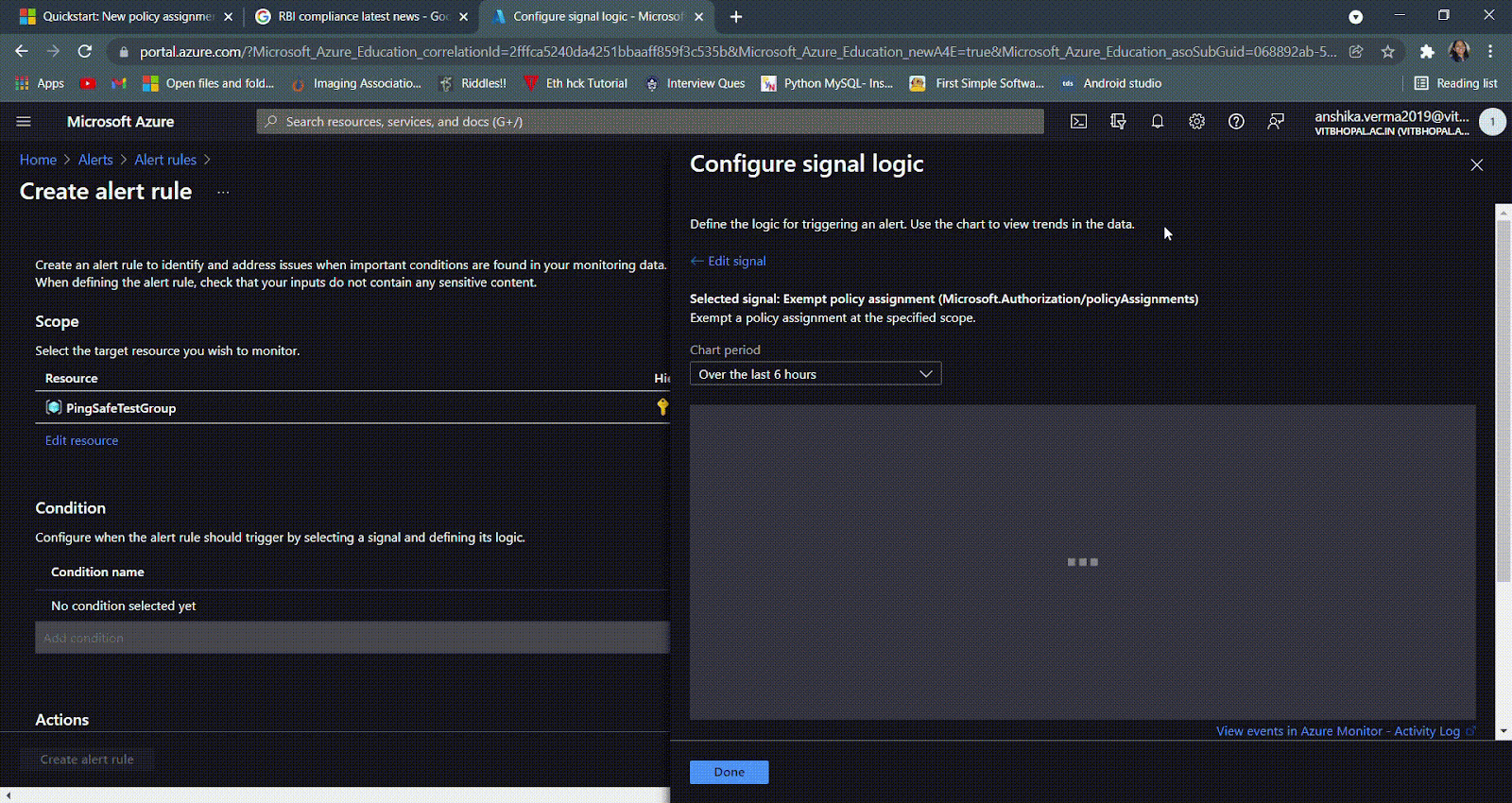
- Click on the search bar and type “Policy Assignment”, now depending on the organizational requirement, select a suitable and appropriate condition for triggering of the alert rule. Here, we are choosing the signal “Exempt policy assignment (Microsoft.Authorization/policyAssignments)”. Click on Done.
- NOTE: It is suggested to create a policy assignment alert rule for all the given conditions, i.e., create, delete and exempt.
- Users can then select an action group(optional). Next, provide the alert rule name as desired and give a little description to it for later reference (optional).
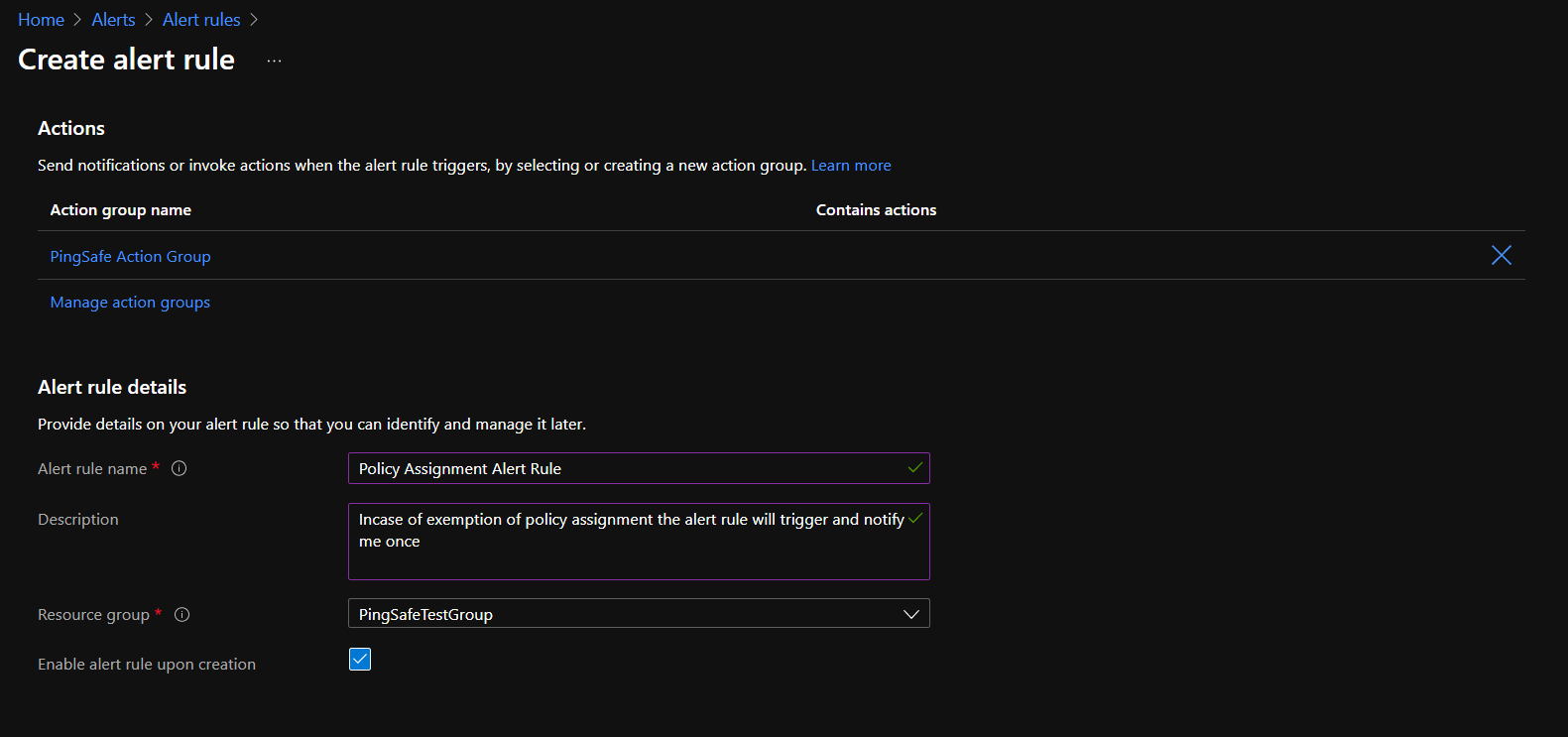
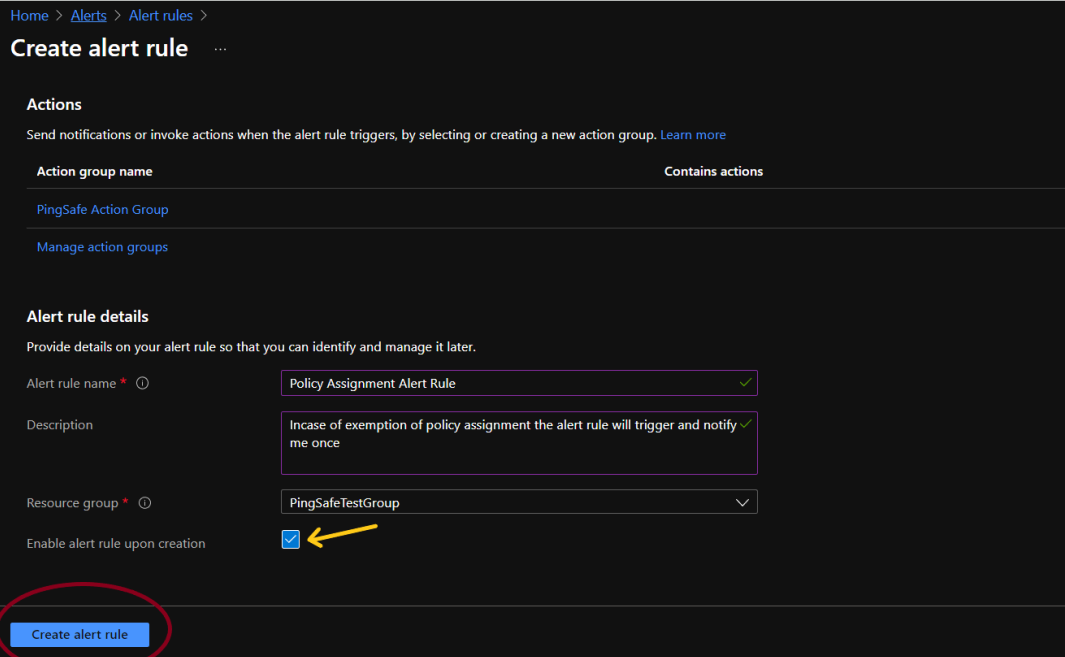
- By default, the alert rule is enabled but it is recommended to cross verify it and then click on Create alert rule.
Enable Alert Rule:
- Login to the Azure account.
- From Azure services, select Alerts.

- The Alerts page will open, select the Alert rules option.

- The alerts rule page will appear. By default, only the enabled alert rules are shown on the screen.

- To check the list of disabled alert rules as well, go to the Status option and click on Select all.

- To find alert rule based on:
- Rule name: Type in the policy assignment alert rule provided at the time of policy creation in the search bar.

- Condition name: To find the alert rule using policy, type “Microsoft.Authorization/policyAssignments/”.

- Rule name: Type in the policy assignment alert rule provided at the time of policy creation in the search bar.
- Now, select all the disabled alert rules by clicking on the checkbox.
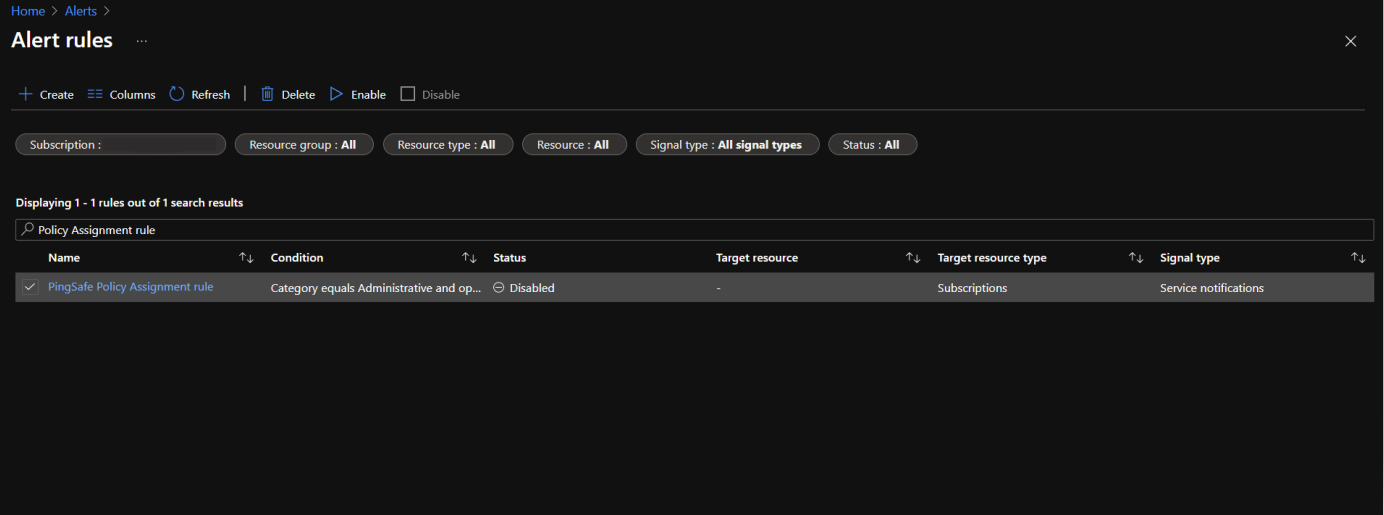
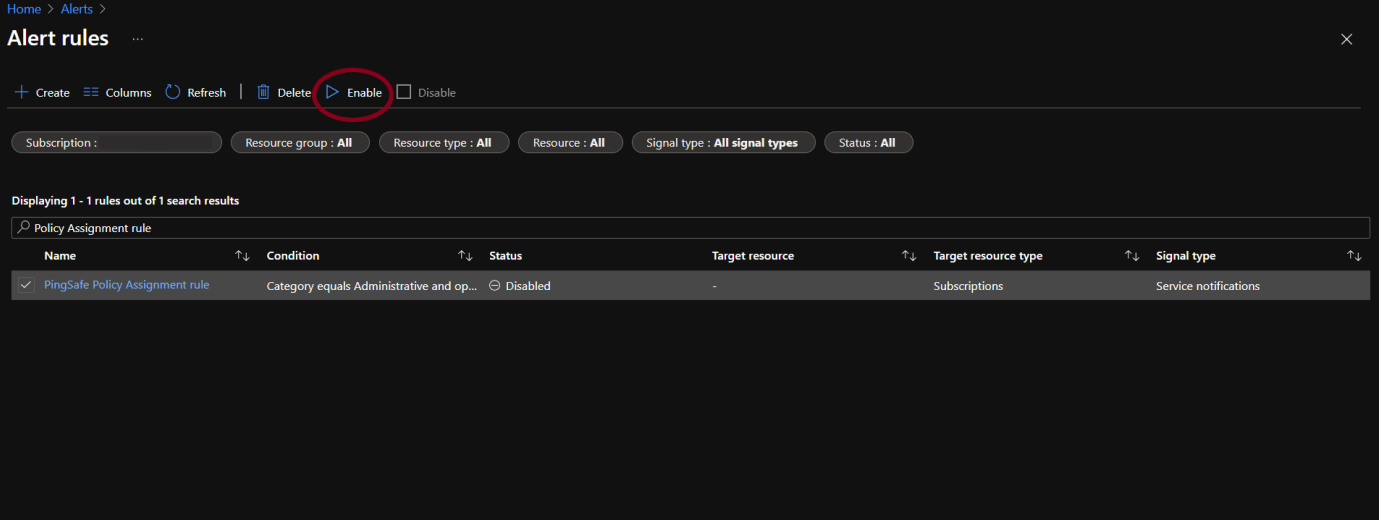
- Click on Enable and wait on the changes to save.
Please feel free to reach out to support@pingsafe.ai with any questions that you may have.
Thanks
PingSafe Support