Private Access Disabled
RISK LEVEL
Low
DESCRIPTION
This plugin ensures Private Google Access is enabled for all Subnets. This has to be taken care of, to keep a check on an extra layer of security over the VPC Network. Private Google Access allows VM instances on a subnet to reach Google APIs and services without an IP address. This creates a more secure network for internal communication.
ABOUT THE SERVICE
Google Cloud VPC:
According to Google definitions, VPC which stands for a Virtual Private Network is a virtual version of a physical layer, implemented inside of Google’s Production Network, using Andromeda. The Virtual Private Network offers various features including, connectivity for your Compute Engine Virtual Machine (VM) instances, Google Kubernetes Engine (GKE) clusters, etc. It helps to load balancing and proxy systems for internal system affairs. It even allows assistance in the traffic from Google Cloud external load to backends. Users can have the advantage of containing multiple VPC Networks over a single GCP Project. Various default features are already enabled with VPC Networks, for instance, logging metadata is incorporated into your Virtual Private Cloud (VPC) firewall log files. Click here to read more about Google Cloud VPC Networks.
IMPACT
A subnet, or subnetwork, is a fragmented piece of a bigger organization. All the more explicitly, subnets are an intelligent parcel of an IP network into various, more modest organization fragments. One objective of a subnet is to part a huge organization into a gathering of more modest, interconnected organizations to assist with limiting traffic. Private Google Access is enabled on a per subnet basis, and therefore there is a need to have a VPC Network. This creates a vulnerability for the VPC Network, hence the issue message arises as private access is disabled for VPC sub-networks. This module guarantees Private Google Access is empowered for all Subnets. This must be dealt with, to keep a mind an additional layer of safety over the VPC Network. Private Google Access permits VM occasions on a subnet to arrive at Google APIs and administrations without an IP address. This makes a safer organization for interior correspondence.
STEPS TO REPRODUCE
Using GCP Console-
In order to determine if Private Google Access is enabled for all the subnets of Google Cloud Platform VPC Networks in your project, follow the steps mentioned below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.
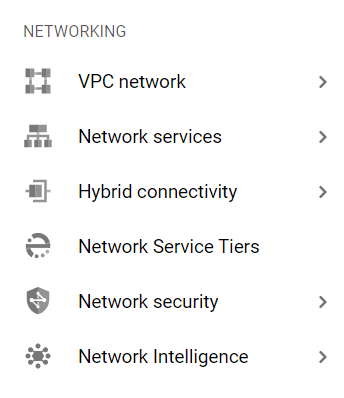
- From the Navigation Menu on the left, you may find the Networking section.
- Click on the VPC Network subsection under Networking.
- Under the VPC Network navigation panel, you may find VPC Networks as shown in the figure below.
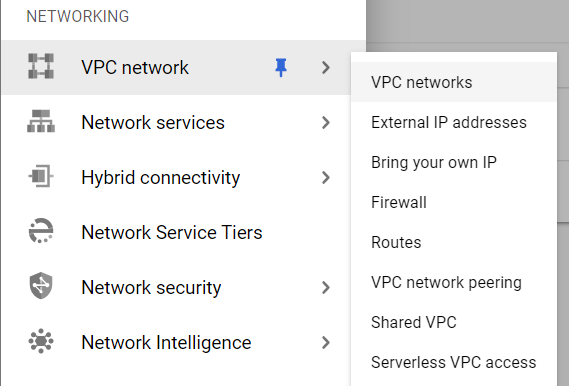
- Click on the VPC Networks navigation link and a VPC Networks dashboard will appear on the screen. Click to open directly from here.
- Click on the Refresh button present in the top Nav bar, to recollect or load the data present in VPC Networks of your GCP Project.
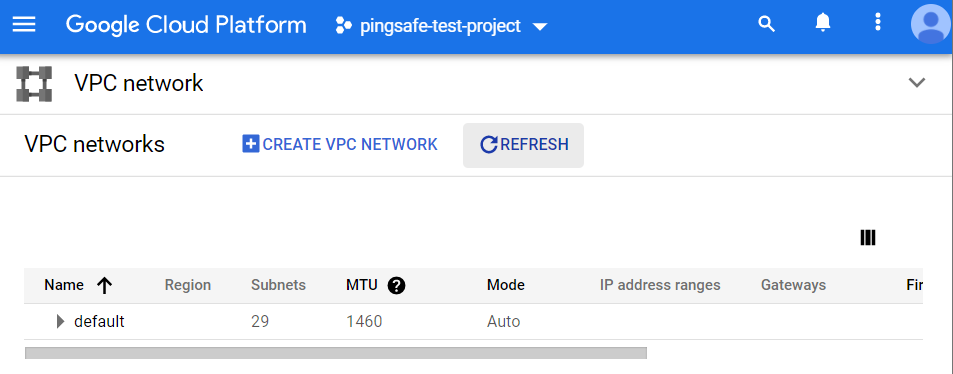
- Now, click on the Name of the VPC Network to expand that, i.e. default VPC Network, (or whatever name you have given to your VPC Networks).
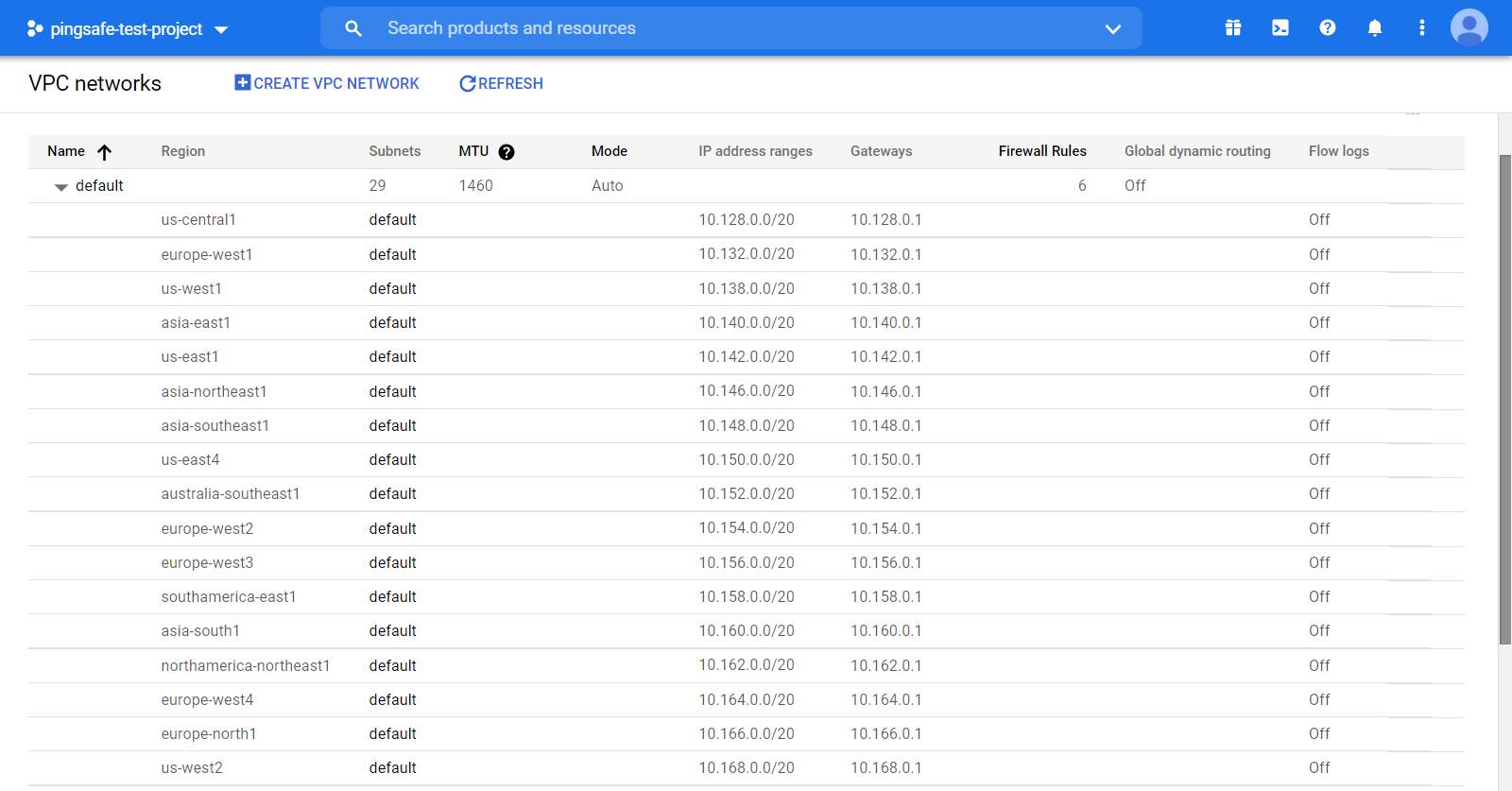
- Now, click on the default option under Subnets column of a particular region.
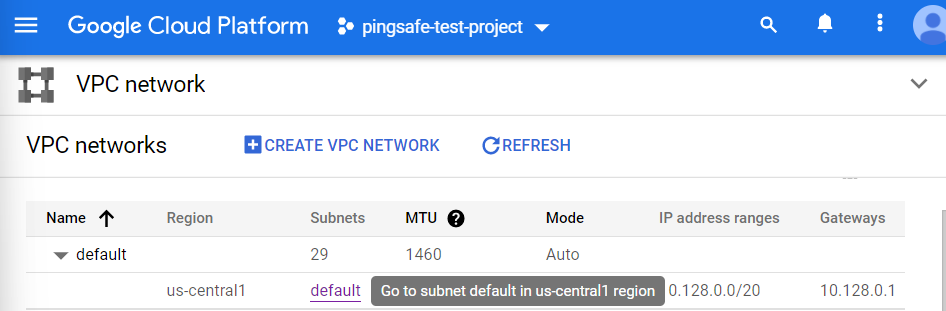
- A new page will be opened showing all the Subnet Details of the subnet of that particular region.
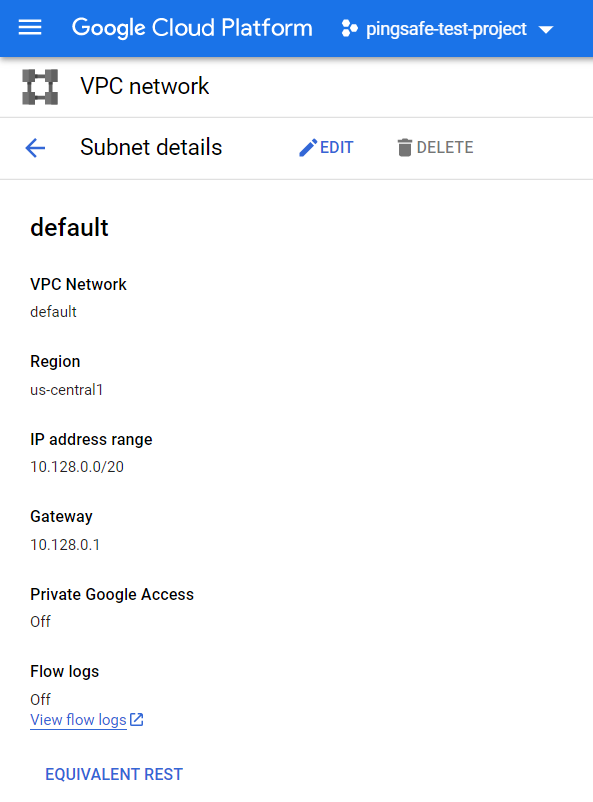
- Check for the Private Google Access option under Subnet Details Page. If the Private Google Access is set to Off, this means PGA is disabled for that subnet of VPC Network.
- You may go back to the previous page and repeat steps 9-11 for subnets of other regions.
- You may repeat steps 7-12 for other VPC Networks in your current GCP Project.
- Repeat the steps mentioned above for reviewing accounts in other folders/projects associated with other GCP organizations deployed within your record.
STEPS FOR REMEDIATION
Using GCP Console-
In order to enable Private Google Access for all the subnets of Google Cloud Platform VPC Networks in your project, follow the steps mentioned below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find the Networking section.
- Click on the VPC Network subsection under Networking.

- Under the VPC Network navigation panel, you may find VPC Networks as shown in the figure below.

- Click on the VPC Networks navigation link and a VPC Networks dashboard will appear on the screen. Click to open directly from here.
- Click on the Refresh button present in the top Nav bar, to recollect or load the data present in VPC Networks of your GCP Project.

- Now, click on Name of the VPC Network to expand that, i.e. default VPC Network, (or whatever name you have given to your VPC Networks).

- Now, click on the default option under Subnets column of a particular region.

- A new page will be opened showing all the Subnet Details of the subnet of that particular region.

- If the Private Google Access is set to OFF, which you must have checked in the earlier section. Click on the Edit button present on the top Navbar of the subnet details page.
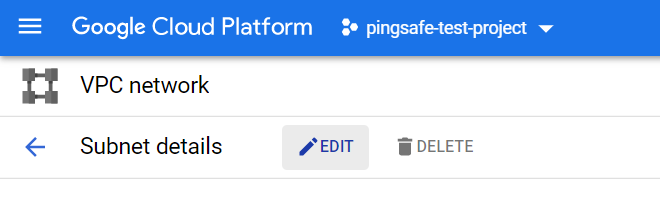
- On the Edit Page, under the Private Google Access, set it to ON option.

- After ensuring your entered details click on the Save button.
- You may go back to the previous page and repeat the steps 9-13 for subnets of other regions.
- You may repeat steps 7-13 for other VPC Networks in your current GCP Project.
- Repeat the steps mentioned above for reviewing accounts in other folders/projects associated with other GCP organizations deployed within your record.