RDS Publicly Accessible
This plugin ensures Amazon RDS instances are not launched into the public cloud.
Risk Level: High
Description
This plugin ensures Amazon RDS instances are not launched into the public cloud. A private connection can be established between the Amazon RDS API and the VPC using a VPC interface that enables only the connection points within the VPC to access the API. Unless absolutely necessary, Amazon RDS instances must not be made public.
About the Service
Amazon RDS: Amazon RDS is a scalable relational database service for the cloud. It provides a fast, secure and highly scalable database server. As explained by the AWS docs, Amazon RDS is a managed relational database service that provides you six familiar database engines to choose from, including Amazon Aurora, MySQL, MariaDB, Oracle, Microsoft SQL Server, and PostgreSQL.
Impact
Whitelisting all the IP addresses and allowing public access to the RDS instance can allow anyone over the internet to establish a connection with the database.
This can lead to data breaches or data loss. It is highly recommended to establish only a private connection with the RDS instance.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the Amazon RDS Console. You can use this link (https://console.aws.amazon.com/rds/) to navigate directly if already logged in.
- From the left navigation pane, click on Databases from the left panel.
- A list of databases will be displayed. Select the database you want to examine by clicking on it’s DB Identifier.
- Move to the Connectivity and security tab.
- In the Security section, scroll down to find Publicly accessible. If it is enabled, the vulnerability exists.
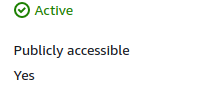
- Repeat steps 3 to 6 for all the database instances you wish to examine.
Steps for Remediation
Remove the public endpoint from the RDS instance
- Log In to your AWS Console.
- Open the Amazon RDS Console. You can use this link (https://console.aws.amazon.com/rds/) to navigate directly if already logged in.
- From the left navigation pane, click on Databases from the left panel.

- A list of databases will be displayed. Select the vulnerable database by clicking on it’s DB Identifier.
- Click on Modify from the top-right corner.
- In the Connectivity section, expand the Additional Configuration section.
- Select the option of Not Publicly Accessible. Click on Continue to apply the changes.
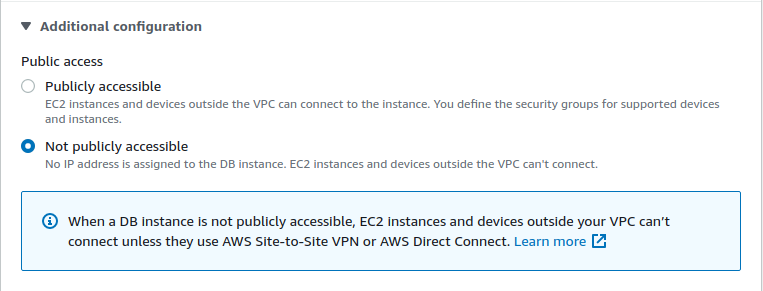
- Repeat steps 3 to 7 for all the vulnerable database instances.