S3 Buckets With Logging Disabled
Ensure that logging is enabled for all S3 Buckets to track all the requests
Risk Level: Low
Description
This plugin identifies the S3 buckets where logging is disabled. With S3 buckets logging enabled, you can track the requests made to access and modify S3 buckets, and with the logs generated, identify potential security threats by monitoring unusual requests. As good security practice, SentinelOne CNS recommends enabling logging for S3 buckets.
About the Service
Amazon S3: Amazon Simple Storage Service, popularly known as Amazon S3, is a storage space available on the cloud. Using Amazon S3, you can store and retrieve any amount of data. It offers various features such as logging, using which you can keep a track of requests made. You can read more about logging here.
Impact
Logs are important for keeping a track of requests made to the S3 bucket. It is recommended to regularly keep a close eye on the logs for any unusual activity. In the event of data compromise, generated logs will be useful to identify unusual or unauthorized access. It can eventually lead to the attacker's details. Without logs, the security team will not have any information to begin the investigation.
Compliances covered
PCI: PCI requires logging of all network access to environments containing cardholder data. To comply with PCI standards, you must enable logging of the Amazon S3 bucket.
HIPAA: Health Insurance Portability and Accountability Act of 1996 (HIPAA) requires strict auditing controls around data access. S3 logging helps ensure these controls are met by monitoring access to all bucket objects. Logs should be stored in a secure, remote location.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the S3 Management Console. You can use this link (https://console.aws.amazon.com/s3) to navigate directly if already logged in.
- Select the S3 bucket you wish to investigate and click on the Properties tab from the top navigation bar.
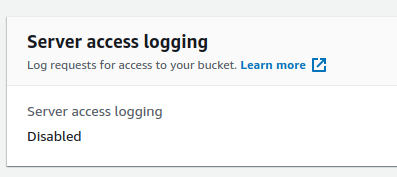
- Move to the Server access logging section in the Properties Tab and examine whether it is enabled or disabled for the bucket. If it is disabled, you might not be able to monitor unusual requests and track the user involved in case of unauthorized access.
- Repeat steps 3 to 4 for all the S3 buckets you want to investigate.
Steps for Remediation
The steps to enable logging are-
- Log In to your AWS Console.
- Open the S3 Management Console. You can use this link (https://console.aws.amazon.com/s3) to navigate directly if already logged in.
- Select the S3 bucket you wish to investigate and click on the Properties tab from the top navigation bar.
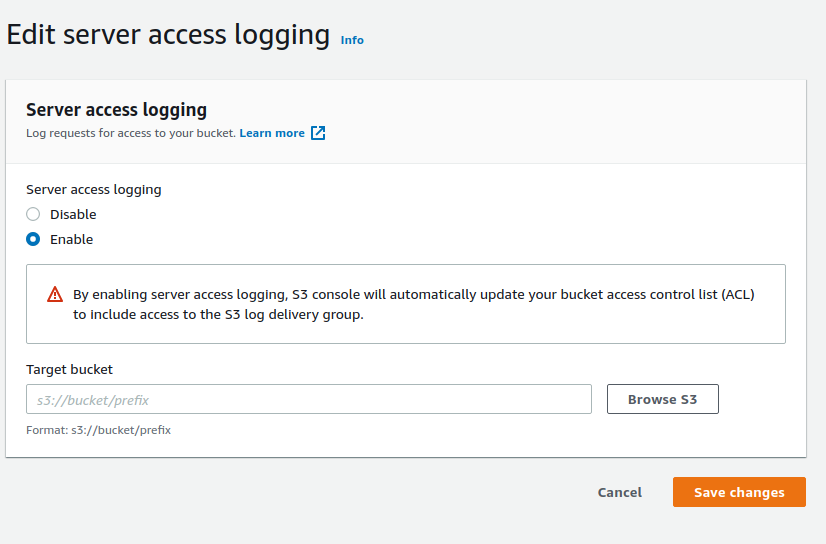
- Move to the Server access logging section in the Properties Tab and select the Edit option beside the section title.
- In the edit option, select the Enable option and enter the Target bucket where the logs will be stored in the format “s3://bucket/prefix”. Prefix stands for the subdirectory of the selected bucket. Alternatively, you can also browse to select the path. Finally, click on Save Changes.
- Repeat steps 3 to 5 for all the vulnerable S3 buckets.