Secrets Manager Weakly Encrypted Secrets
Risk Level: Low
Description
This plugin ensures Secrets Manager secrets are encrypted strongly. This allows their values to be used by approved systems, while restricting access to other users of the account. Secrets Manager supports both default encryption based on an AWS-managed KMS key as well as encryption using a customer-managed key. It is recommended to use at least CMKs to encrypt the secrets but the settings can be modified on the CNS dashboard as per the requirements.
Configuration Parameters
Secrets Manager Secret Minimum Encryption Level: This parameter specifies the encryption level provided by the KMS key associated with the resource. The values it can take are: (lowest to highest) sse=Default Encryption; awskms=AWS-managed KMS; awscmk=Customer managed KMS; externalcmk=Customer managed externally sourced KMS; cloudhsm=Customer managed CloudHSM sourced KMS.
By default, its value is set to awskms, therefore it will generate a vulnerability alert if the KMS key is not provided or not enabled.
About the Service
AWS Secrets Manager: As the name suggests, Secrets Manager enables you to replace hard coded credentials in your code, with an API call to Secrets Manager to retrieve the secret programmatically. This ensures that the sensitive information secured by the credentials cannot be accessed by the attacker even if the code gets compromised. It manages the access control to the secrets so that only authorized systems can access the secrets.
Impact
In the absence of proper encryption, the secrets containing sensitive and critical information about cloud infrastructure/organization can be visible to the attacker in case of any compromise. Therefore, to avoid visible exposure of the data, it is necessary to encrypt the secrets appropriately.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the Amazon Secrets Manager Console. You can use this link (https://console.aws.amazon.com/secretsmanager) to navigate directly if already logged in.
- Scroll down and select Secrets from the left pane.
- A list of secrets will appear. Choose the secret you want to examine by clicking on its Name.
- In the Secret Details section check the Encryption Key. Proceed if there exists a key ARN and copy the ARN.
- Copy the Key ARN and move to the KMS console.
- In the Customer-managed keys section, paste the key arn you have copied before. If no keys are found, the vulnerability exists.
- Repeat steps for all the secrets you want to investigate.
Steps for Remediation
Encrypt Secrets Manager Secrets to use encryption of the desired level.
- Log In to your AWS Console.
- Open the Amazon Secrets Manager Console. You can use this link (https://console.aws.amazon.com/secretsmanager) to navigate directly if already logged in.
- Scroll down and select Secrets from the left pane.

- A list of secrets will appear. Choose the vulnerable secret by clicking on its Name.
- In the Secret Details section from the Actions menu, select the Edit Encryption key option.
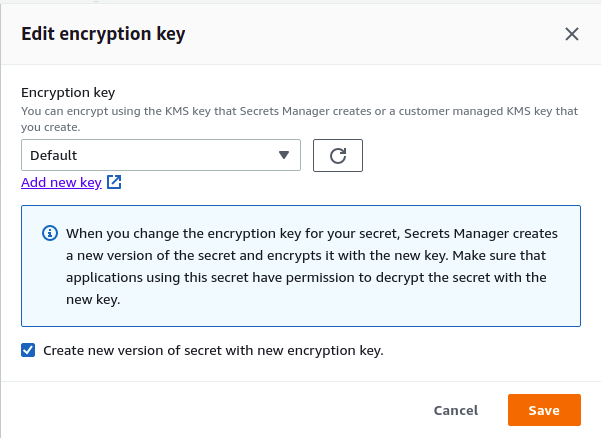
- Select a valid KMS key from the drop-down menu of the desired level. Finally click on Save.
- Repeat steps for all the secrets you want to investigate.