Service Account Keys Not Generated By Google
Risk Level: Low
Description
About the Service
Google Cloud IAM:
IAM, which is an acronym for Identity and Access Management, is the Google Cloud policy. This policy is responsible for specifying access controls for Google Cloud resources. Basically, IAM allows heads to approve who can make a move on explicit assets, giving you full control and permeability to oversee Google Cloud assets halfway. For undertakings with complex hierarchical designs, many workgroups, and many activities, IAM gives a bound together view into security strategy across your whole association, with worked in evaluating to ease consistency processes. For more information, click here.
Impact
Steps To Reproduce
Using GCP Console-
In order to ensure that, the service account keys are managed by Google or not in GCP Projects, follow the steps given below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate.

- From the Navigation Menu on the left, you may find IAM & Admin section under All Products Section, click on it.
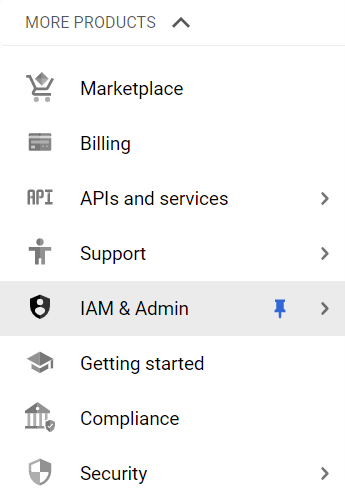
- Under IAM & Admin section, click on the Service Accounts button. Thence, a new Service Accounts Page will appear.
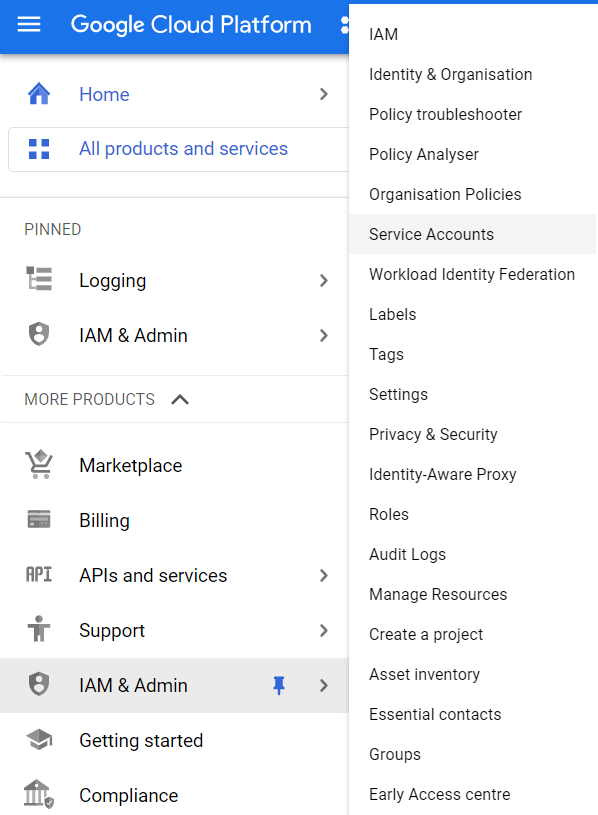
- You will find a list of all the Service Accounts available in your current GCP Project.
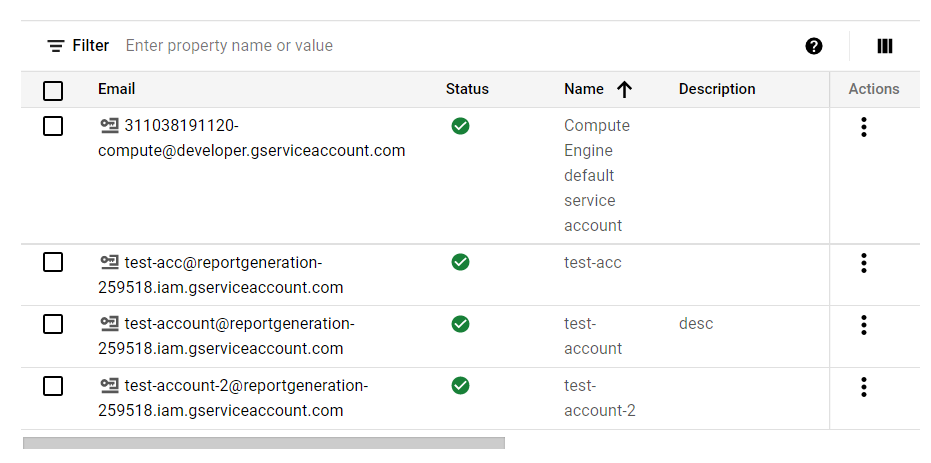
- Click on the Email Address of the service account you want to examine or check for.
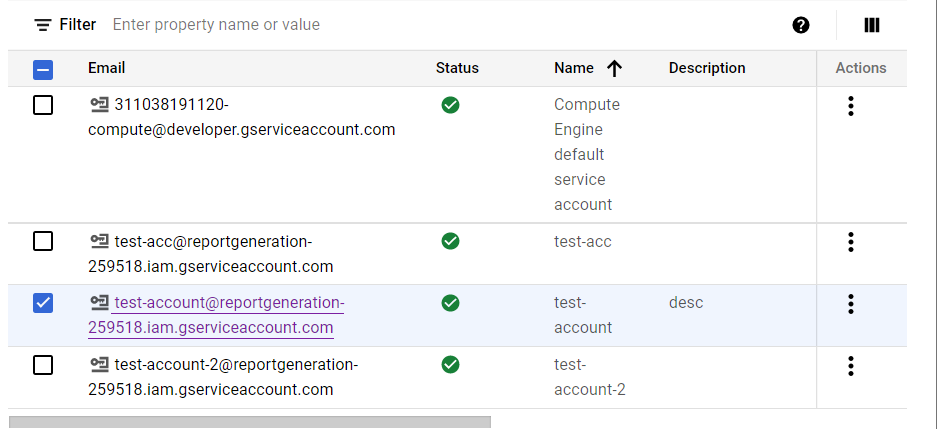
- A new page with all the details about that service account will be opened up. Click on the Keys Nav link available on the top.
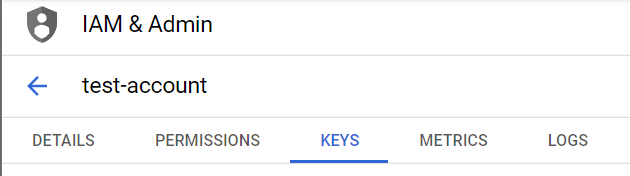
- A list of all the keys will be displayed there, with all the details, for eg., Key Creation date, Key expiry date, key Name, Key Type, etc.
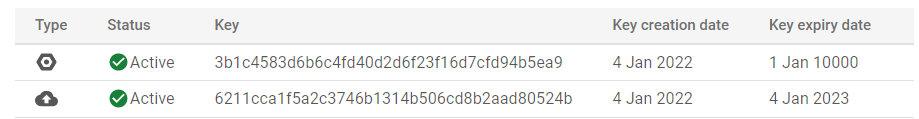
- Under the Type Column, check out for the symbol available. If it shows Generated Key Icon, that means the key is generated by Google. If it shows Uploaded Key Icon, that means the key is uploaded and not generated by Google.
- If the Type of key is Uploaded, this means that they are unsecured. This way you can check out the service accounts keys are managed by Google or not.
- Repeat the steps mentioned above for reviewing accounts in other folders/projects associated with other GCP organizations deployed within your record.
Steps For Remediation
Using GCP Console-
In order to reconfigure the settings to service account keys are managed by Google, follow the below-mentioned steps:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find IAM & Admin section under All Products Section, click on it.

- Under IAM & Admin section, click on the Service Accounts button. Thence, a new Service Accounts Page will appear.

- You will find a list of all the Service Accounts available in your current GCP Project.

- Click on the Email Address of the service account you want to examine or check for.

- A new page with all the details about that service account will be opened up. Click on the Keys Nav link available on the top.

- A list of all the keys will be displayed there, with all the details, for eg., Key Creation date, Key expiry date, key Name, Key Type, etc.

- Under the Type Column, check out for the symbol available. If it shows Generated Key Icon, that means the key is generated by the Google. If it shows Uploaded Key Icon, that means the key is uploaded and not generated by the Google.

- If the Type of key is Uploaded, this means that they are unsecured. Thus, you need to delete that key by clicking on the Delete Icon available at the right of the key row.
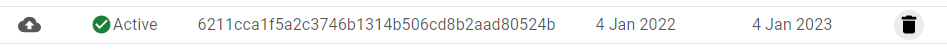
- Now, in order to reconfigure the settings to manage Service Account key by Google, you need to add a new Key.
- Click on the Add Key Button, a dropdown menu will be opened up. Select Create new Key option from the dropdown menu.
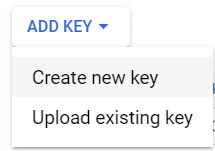
- A new dialog box will be opened up. Select the JSON radio button in it.
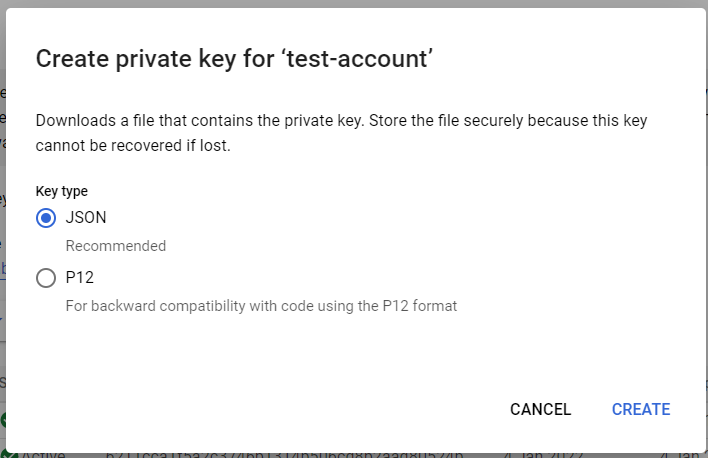
- Now, click on the Create button available at the bottom of the dialog box.

- A new key will be created and a dialog box will appear with a confirmation. Also, a json file will be downloaded with the key info. Now, Click on the Close option.
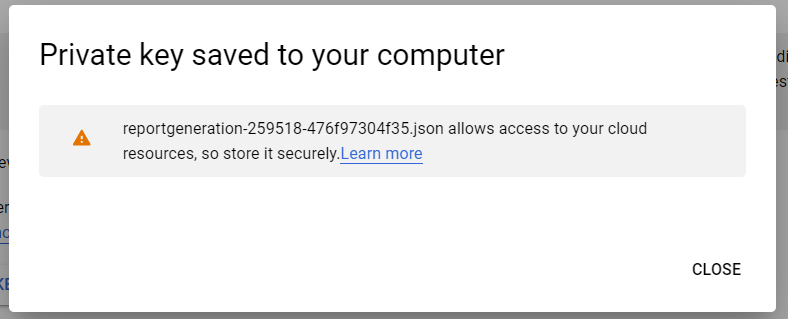
- You may now go back and check the newly created key in the list.
- You may repeat the above steps for other GCP Projects under your organization.