SQL Server Public Access
Risk Level: HIGH
Description:
This plugin prevents SQL Servers from granting public access. SQL Server instances should not have a public endpoint and should only be accessed from within a VNET unless there is a compelling business necessity. A firewall is a network security device that monitors incoming and outgoing network traffic and allows or disallows data packets according to a set of security rules.
SentinelOne CNS strongly recommends ensuring that the firewall of each SQL Server is configured to prohibit traffic from the public internet.
About the Service :
Azure SQL is a set of managed, secure, and intelligent SQL Server database solutions that run in the Azure cloud. Because Azure SQL is based on the well-known SQL Server engine, applications can be easily transferred while keeping the existing tools, languages, and resources.
Impact :
A high level of visibility into Azure SQL Server firewall activity is an important component of security and operational best practices, and it helps you safeguard SQL database access.
Steps to Reproduce :
- Sign in to your Azure portal with your Azure account.
https://portal.azure.com/#home
- Navigate to Azure’s All Resources.
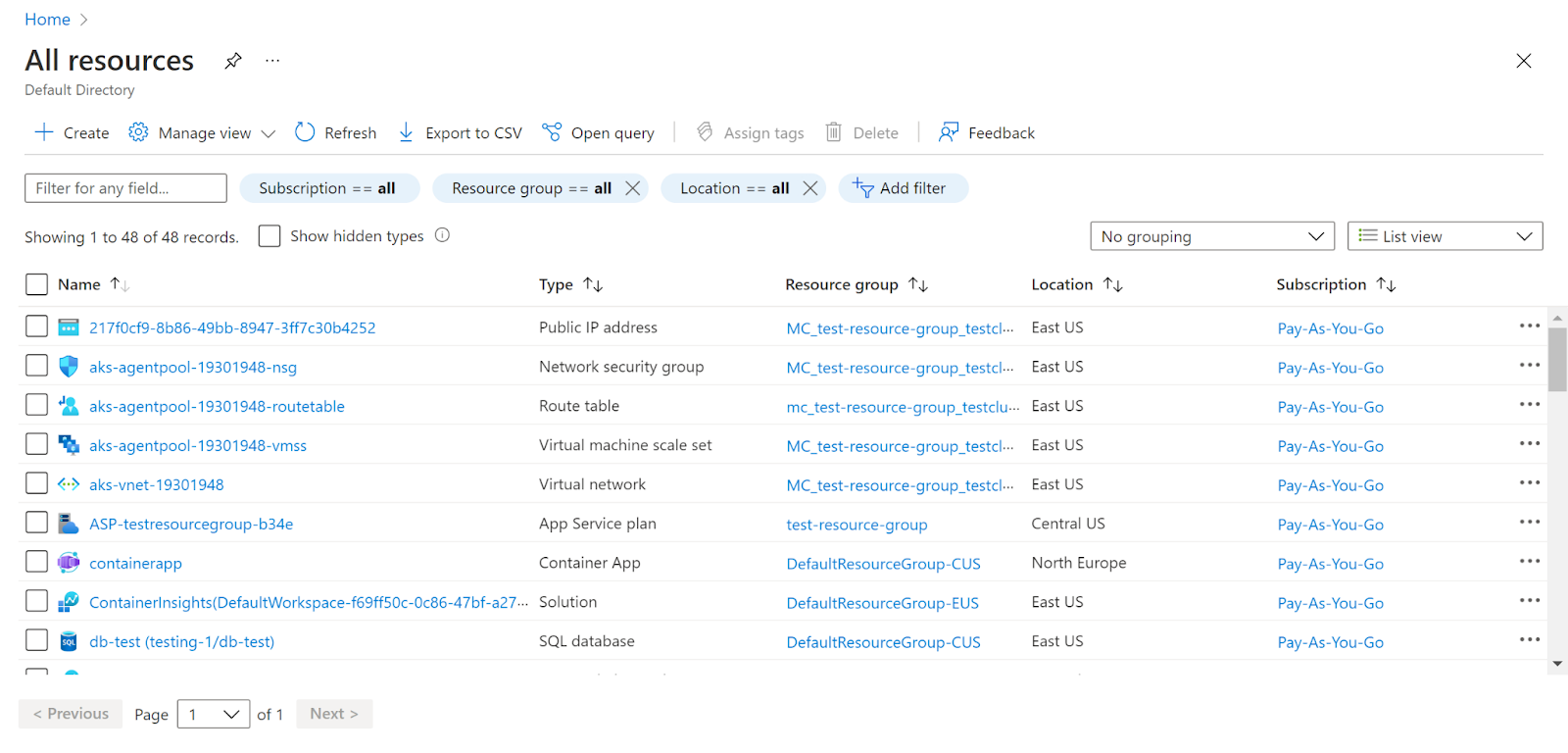
- In the Type filter select the value as SQL Servers and click Apply.
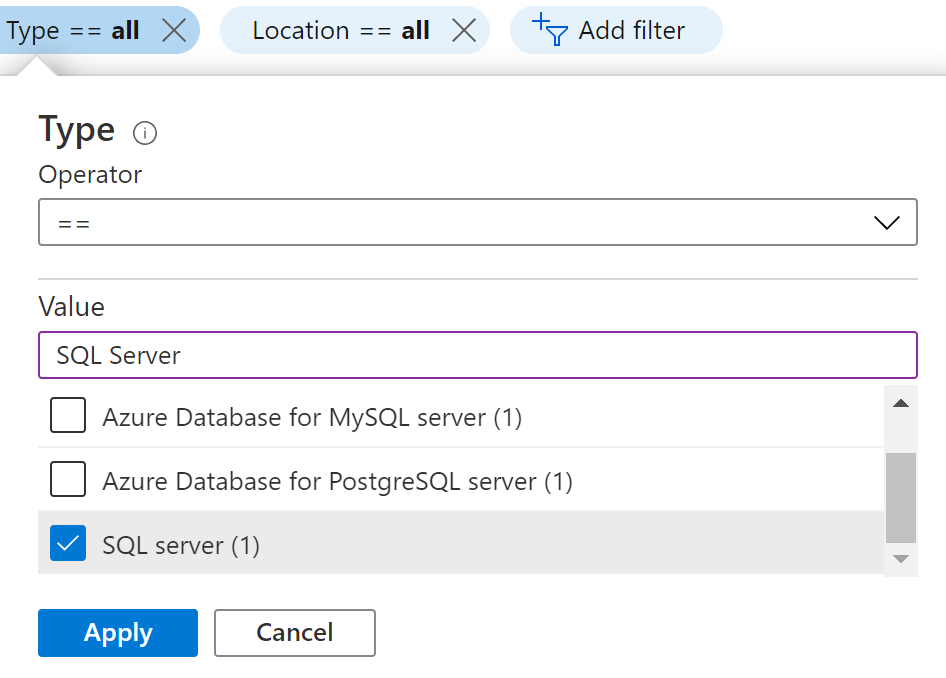
- Next, select the SQL Server that you want to examine.
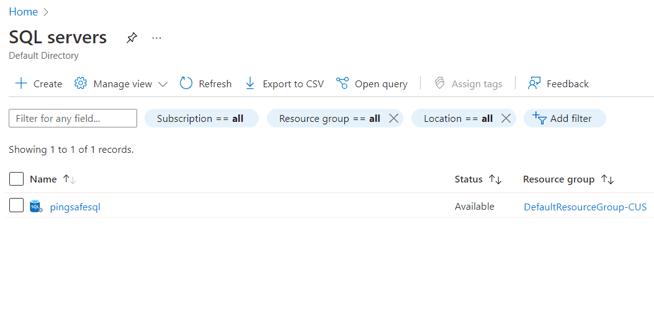
- Click on Networking under Security in the navigation pane.
- Check if the firewall rules are configured to prohibit traffic from the public internet (e.g. startIpAddress - 0.0.0.0 & endIpAddress - 255.255.255.255).
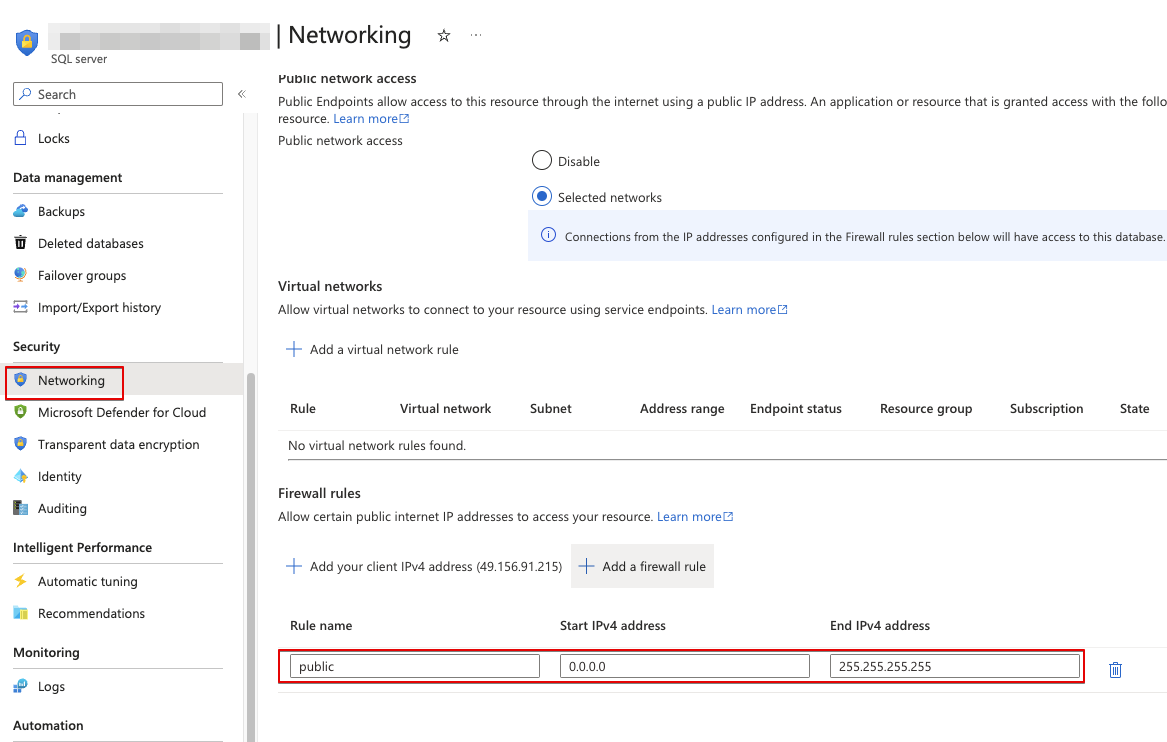
- Repeat the same steps for other servers as well.
Steps for remediation :
- Sign in to your Azure portal with your Azure account.
https://portal.azure.com/#home
- Navigate to Azure’s All Resources.

- In the Type filter select the value as SQL Servers and click Apply.

- Next, select the SQL Server that you want to examine.
- Click on Networking under Security in the navigation pane.
- Check if the firewall rules are configured to prohibit traffic from the public internet (e.g. startIpAddress - 0.0.0.0 & endIpAddress - 255.255.255.255).

- Click on Add a virtual network rule to add new network as per your requirement under Virtual networks. And configure IP whitelisting under Firewall rules. Select Exceptions value as required for the organization. Click on Save.
- Repeat the same steps for other servers as well.
References :