SQS Public Access
This plugin prevents SQS queues from being accessed by the public.
Risk Level: High
Description:
This plugin prevents SQS queues from being accessed by the public. To prevent unwanted activity, SQS queues should not be publicly accessible.
Configuration Parameters
SQS Queue Policy Allowed Condition Keys: This parameter denotes a comma-separated list of AWS SQS Queue condition keys that should be allowed. If the policy statement is vulnerable and these keys are present, the issue will not be generated.
By default, the condition keys mentioned are 'aws:PrincipalArn','aws:PrincipalAccount', 'aws:PrincipalOrgID','aws:SourceAccount', 'aws:SourceArn', 'aws:SourceOwner', 'kms:CallerAccount', 'kms:ViaService', therefore all the statements consisting of these keys will not be scanned.
About the Service :
SQS (Amazon Simple Queue Service) is a fully managed message queuing service for decoupling and scaling microservices, distributed systems, and serverless applications. SQS removes the complexity and overhead of managing and operating message-oriented middleware, allowing developers to concentrate on work that is unique. You may send, store, and receive messages across software components using SQS at any volume without losing messages or necessitating the availability of other services.
Impact: ‘
Allowing anonymous users access to your SQS queues might lead to unauthorized operations such as message interception, deletion, and transmission. When the queue owner sets the Principal to "Everybody (*)" while testing the queue system setup, the insecure set of permissions makes it into production.
Steps to reproduce :
- Sign in to your AWS Management Console.
- Navigate to the SQS dashboard at: https://console.aws.amazon.com/sqs/
- Select the SQS queue that you want to examine.
- Under the Access Policy panel, Access Policy ( Permission ), check the value of the Principal attribute.
- If the value of the Principal attribute is set to “*” i.e. to all, the queue is exposed to anonymous access.
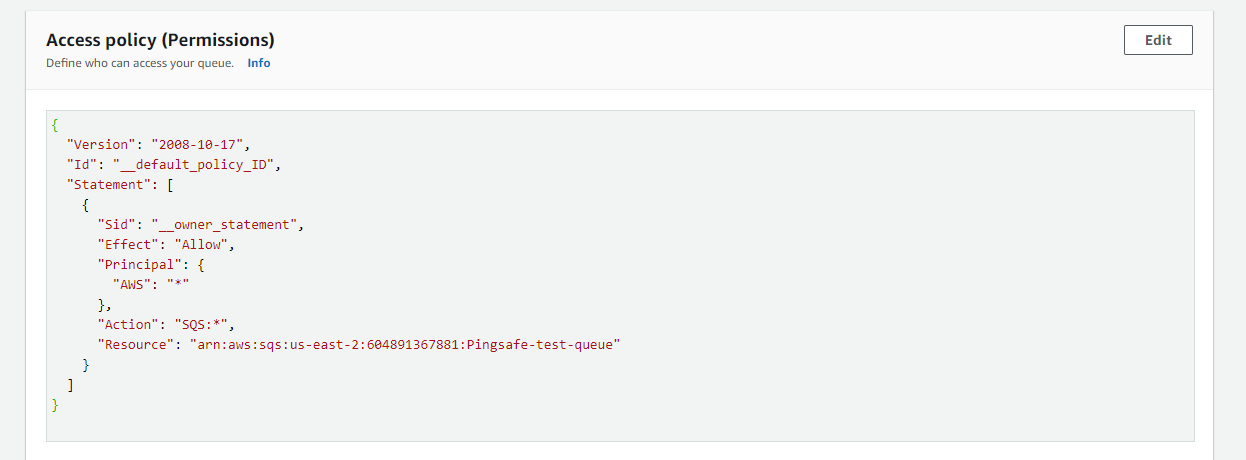
- Repeat steps no. 3-5 for each SQS present in the current region as well as for other regions.
Steps for remediation :
- Sign in to your AWS Management Console.
- Navigate to the SQS dashboard at: https://console.aws.amazon.com/sqs/
- Select the SQS queue that you want to examine.
- Under the Access Policy panel, Access Policy ( Permission ), click on Edit.
- In the code of the access policy, replace “*” with the arn of the service or the user to which the access is to be granted.
- Click on Save changes to apply the new permissions.
- Repeat steps no. 3-6 for each SQS present in the current region as well as for other regions.
References: