User With IAM Service Account User Role
RISK LEVEL
Low
DESCRIPTION
This plugin ensures that no users have the Service Account User role. Under the GCP Identity and Access Management (IAM) project, the Service Account User role gives users access to all service accounts of that project exclusively. This can result in an elevation of privileges, and various heights of advantages, which is not recommended.
ABOUT THE SERVICE
Google Cloud IAM:
IAM, which is an acronym for Identity and Access Management, is the Google Cloud policy. This policy is responsible for specifying access controls for Google Cloud resources. Basically, IAM allows heads to approve who can make a move on explicit assets, giving you full control and permeability to oversee Google Cloud assets halfway. For undertakings with complex hierarchical designs, many workgroups, and many activities, IAM gives a bound together view into security strategy across your whole association, with worked in evaluating to ease consistency processes. For more information, click here.
IMPACT
Cloud Identity and Access Management (IAM) administration give roles to the user accounts, including custom, primitive & predefined.
- Primitive roles provide options like view, edit, and own options existed for the introduction to cloud IAM.
- Predefined roles are jobs made and kept up with my Google, that give granular admittance to explicit Google Cloud Platform (GCP) assets and deny undesirable admittance to different assets.
- Custom roles are client-characterized jobs that permit you to package at least one upheld authorization to meet your particular requirements.
The Service Account User role gives users access to all service accounts of a project. This can eventually result in an up-gradation of privileges, which is not recommended. Thus, this plugin ensures that no users have the Service Account User role.
STEPS TO REPRODUCE
Using GCP Console-
Ensure that if there exists any number of IAM identities that uses the IAM primitive roles of GCP services, just by following the given simple steps:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.
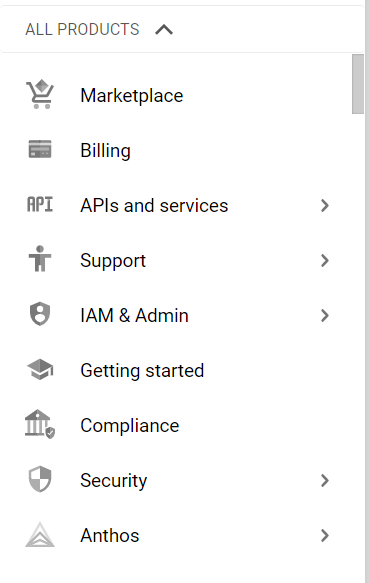
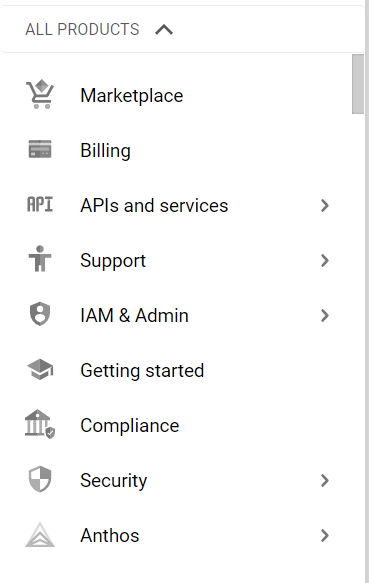
- From the Navigation Menu on the left, you may find IAM & Admin section under All Products Section, click on it.
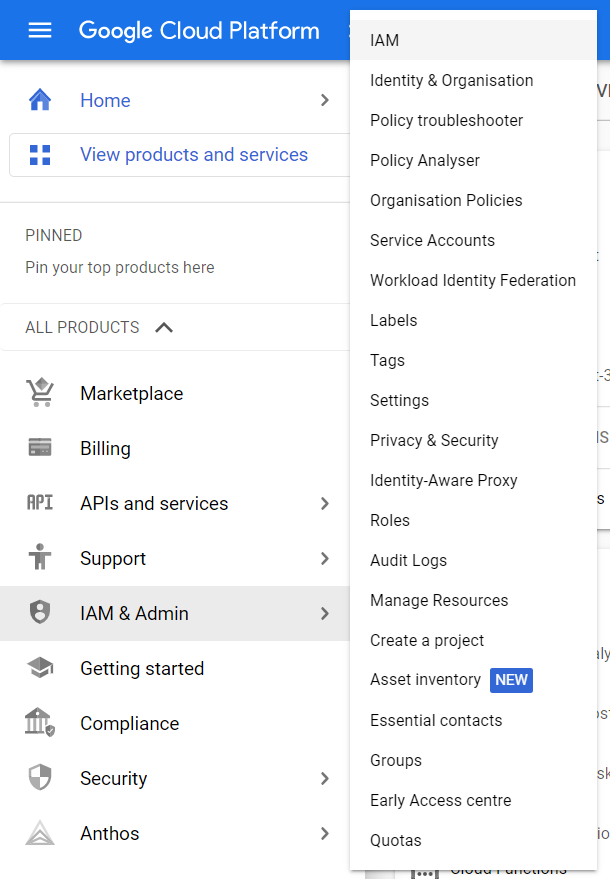
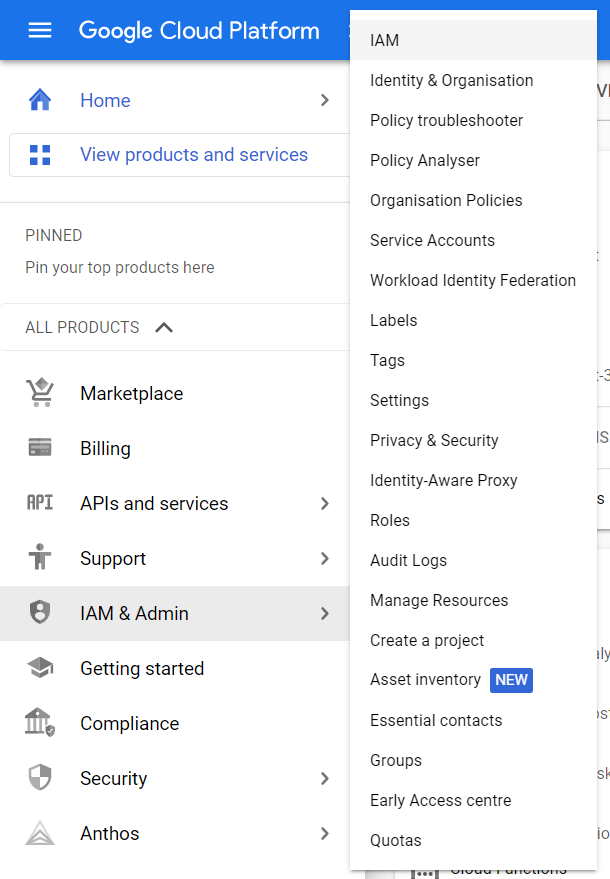
- Under IAM & Admin section, click on the IAM button. Thence, a new IAM Page will appear.
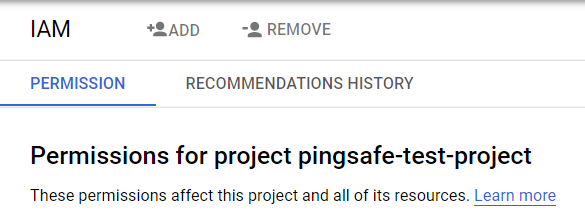
- After selecting the IAM button, click on the Permissions Tab available on the IAM Page.
- Under Peermissions tab, there is an option available as VIEW BY, click on the ROLES or MEMBERS. This will list all the available and working members or the accounts available for your selected GCP Project.
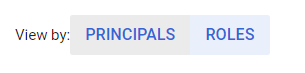
- Under the VIEW BY section you will find a Filter option, click on it.
- Select ROLE and type Owner in filter option, press Enter and you will find the IAM members with Owner Role.
- Select ROLE and type Editor in filter option, press Enter and you will find the IAM members with Editor Role.
- Select ROLE and type Viewer in filter option, press Enter and you will find the IAM members with Viewer Role.
- This way you can check out if there exists any number of IAM identities that uses the IAM primitive roles of GCP services.
- Repeat the steps mentioned above for reviewing accounts in other folders/projects associated with other GCP organizations deployed within your record.
STEPS FOR REMEDIATION
Using GCP Console-
In order to secure the access to yor GCP projects and cancel the roles including, Owner, Editor, Viewer Roles for IAM members accounts, follow the steps given below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.
- From the Navigation Menu on the left, you may find IAM & Admin section under All Products Section, click on it.
- Under IAM & Admin section, click on the IAM button. Thence, a new IAM Page will appear.
- After selecting the IAM button, click on the Permissions Tab available on the IAM Page.
- Under Peermissions tab, there is an option available as VIEW BY, click on the ROLES or MEMBERS. This will list all the available and working members or the accounts available for your selected GCP Project.
- Select the IAM member you want to change settings of. Click on the Edit (PENCIL) icon to access the permissions of that member.
- Click on EDIT Permissions, then click on ADD ANOTHER ROLE.
- Select a Role from the dropdown list to assign or attach the associated primitive role to that particular IAM identity or IAM member. Again use ADD ANOTHER ROLE to assign any other role.
- Now, Click on the SAVE button to save your done changes.
- You may repeat the above steps for other GCP Projects under your organization.