VM Data Disk Encryption Disabled
Risk Level: Medium
Description
This plugin guarantees that Data Disk Encryption is empowered for virtual machines. Encoding VM Data Disks (non-boot volume) guarantees that its whole substance is completely unrecoverable without a key, shielding the volume from inappropriate peruses or unwarranted reads.
About the Service
Azure Virtual Machine:
Azure Virtual Machines (VM) is one of several forms of scalable, on-demand computing resources offered by Azure. VMs are typically used when you require more control over the computing environment than the other options provide. This article explains what you should think about before creating a virtual machine, how to construct one, and how to administer one. For more information, click here.
Impact
At the point when your cloud applications work with touchy information like PII (Personally Identifiable Information), it is firmly prescribed to empower encryption to shield this information from unapproved access and satisfy consistent prerequisites for information very still encryption inside your association. By scrambling your Azure virtual machine non-boot volumes, you have the assurance that your whole VM information is completely unrecoverable without the shielded key and thusly gives security from unapproved peruses.
Steps to Reproduce
In order to determine, if encryption is enabled for Azure Virtual Machine Data Disk Volumes, follow the steps given below:
Using Azure Console-
- Firstly, sign in to the Azure Management Console with your registered organization email address.
- Under Azure Services, choose Subscriptions.
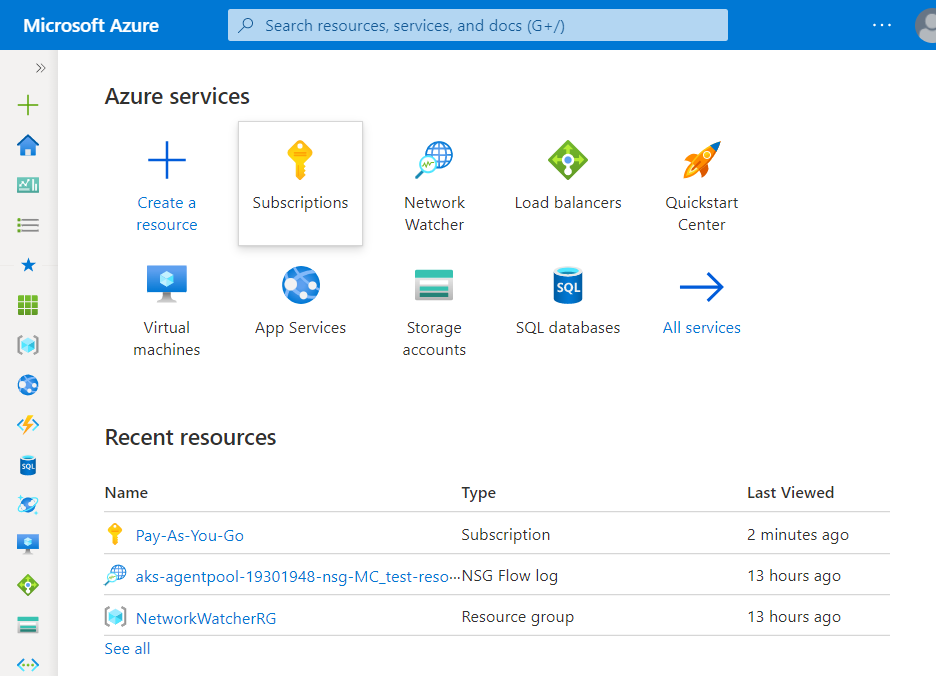
- A new Subscription page will be opened up. Choose the subscription for which the issue has to be examined.
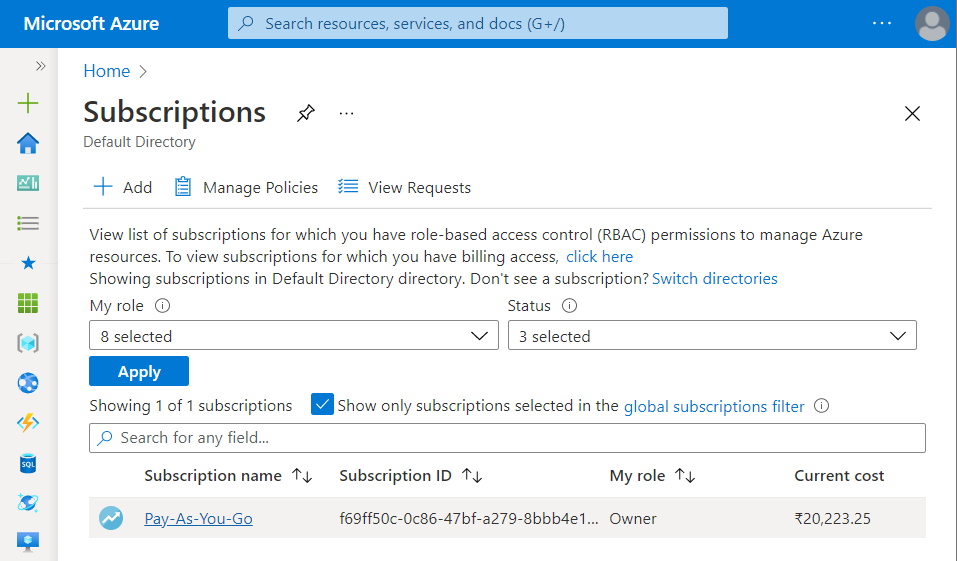
- Now, in the Filter Type Box, search for Virtual Machines.
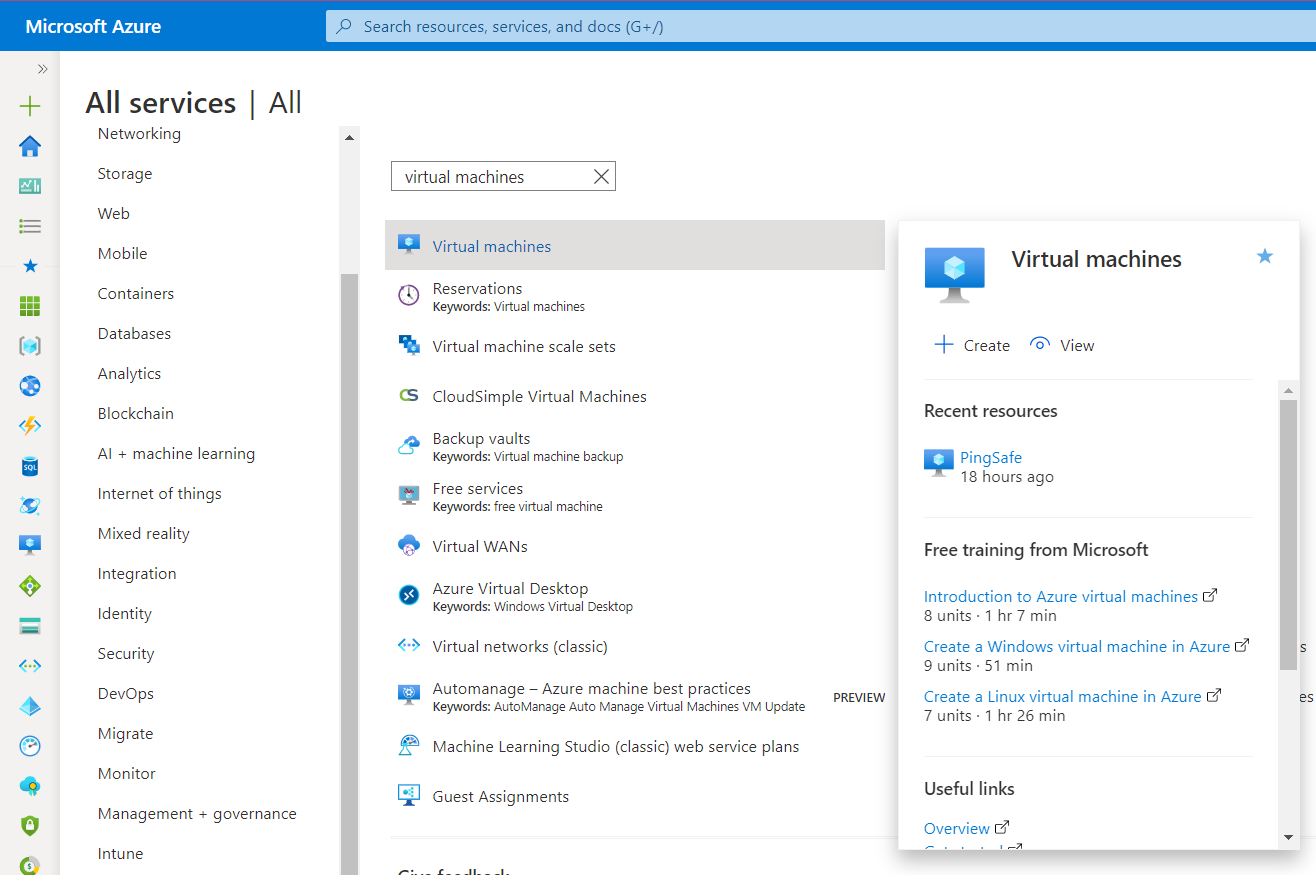
- Click on the Virtual Machines nav link. A list of all the virtual machines (VMs) in your selected subscription will be displayed on the screen.
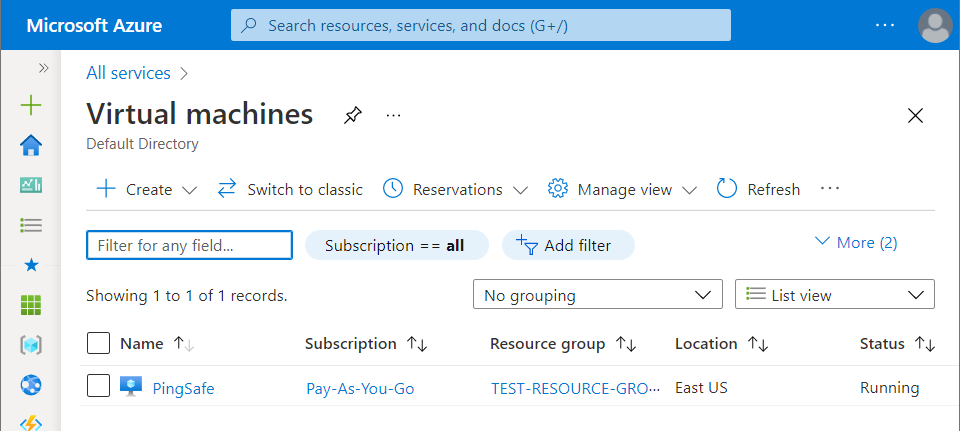
- Click on the Name of the Virtual Machine, for which you want to examine.
- A detailed view of your selected virtual machine will be displayed. Now, in the navigation panel, under Settings, click on the Disks blade.
- A detailed Disk page will appear. On that page, under Data disks check for the disk volume encryption status, under the Encryption column.
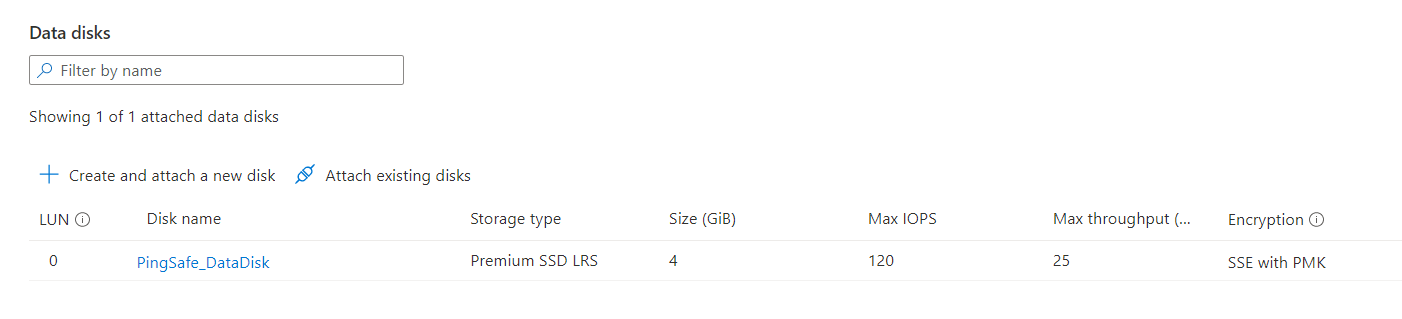
- If the encryption status is set to Not Enabled, then the non-boot (data) volume attached to the selected VM is not encrypted, and needs to be encrypted.
- Follow the steps above, for other Azure Virtual Machines (VMs) in the current subscription as well as in other subscriptions in your Azure Cloud.
Steps for Remediation
In order to reconfigure Azure Virtual Machine (VM) to enable encryption VM non-boot data disk volumes, follow the steps given below:
Note: Currently, Azure Console does not permit to encrypt VM non-boot data disk, this can be done using the Azure CLI.
Using Azure CLI-
- Firstly, run keyvault create command to create the MS Azure Key Vault, in which the generated disk encryption key will be placed.
- Make sure to set the –enabled-for-disk-encryption parameter to be true.
az keyvault create
--name cc-disk-encryption-vault
--resource-group cloud-shell-storage-westeurope
--location westeurope
--enable-soft-delete true
--enable-purge-protection true
--enabled-for-disk-encryption true - The command output must return the configurations for the newly created MS Azure Key Vault:
{
"id": "/subscriptions/abcdabcd-1234-abcd-1234-abcd1234abcd/resourceGroups/cloud-shell-storage-westeurope/providers/Microsoft.KeyVault/vaults/cc-disk-encryption-vault",
"location": "westeurope",
"name": "cc-disk-encryption-vault",
"properties": {
"accessPolicies": [
{
"applicationId": null,
"objectId": "1234abcd-1234-abcd-1234-abcd1234abcd",
"permissions": {
"certificates": [
"get",
"list",
"delete",
"create",
"import",
"update",
"managecontacts",
"getissuers",
"listissuers",
"setissuers",
"deleteissuers",
"manageissuers",
"recover"
],
"keys": [
"get",
"create",
"delete",
"list",
"update",
"import",
"backup",
"restore",
"recover"
],
"secrets": [
"get",
"list",
"set",
"delete",
"backup",
"restore",
"recover"
],
"storage": [
"get",
"list",
"delete",
"set",
"update",
"regeneratekey",
"setsas",
"listsas",
"getsas",
"deletesas"
]
},
"tenantId": "1234abcd-1234-abcd-1234-abcd1234abcd"
}
],
"createMode": null,
"enablePurgeProtection": true,
"enableSoftDelete": true,
"enabledForDeployment": false,
"enabledForDiskEncryption": true,
"enabledForTemplateDeployment": null,
"networkAcls": null,
"provisioningState": "Succeeded",
"sku": {
"name": "standard"
},
"tenantId": "1234abcd-1234-abcd-1234-abcd1234abcd",
"vaultUri": "https://cc-disk-encryption-vault.vault.azure.net/"
},
"resourceGroup": "cloud-shell-storage-westeurope",
"tags": {},
"type": "Microsoft.KeyVault/vaults"
} - Now, run the vm encryption enable command using the Azure VM ID, that you want to reconfigure as an identifier parameter, to enable encryption at rest for the non-boot data disk volume attached to the selected Azure virtual Machine in your selected subscription.
az vm encryption enable
--ids "/subscriptions/abcdabcd-1234-abcd-1234-abcd1234abcd/resourceGroups/CLOUD-SHELL-STORAGE-WESTEUROPE/providers/Microsoft.Compute/virtualMachines/cc-warehouse-app-server"
--disk-encryption-keyvault cc-disk-encryption-vault
--volume-type DATA - The command output must return the confirmation message:
The encryption request was accepted. Please use 'show' command to monitor the progress. - Now, run the vm encryption show command using the Azure VM ID, that you want to reconfigure as an identifier parameter, to confirm the encryption process attached to the selected Azure virtual Machine in your selected subscription.
az vm encryption show
--ids "/subscriptions/abcdabcd-1234-abcd-1234-abcd1234abcd/resourceGroups/CLOUD-SHELL-STORAGE-WESTEUROPE/providers/Microsoft.Compute/virtualMachines/cc-warehouse-app-server" - The command output must return the encryption configuration information:
-
{
"disks": [
{
"encryptionSettings": [
{
"diskEncryptionKey": {
"sourceVault": {
"id": "/subscriptions/abcdabcd-1234-abcd-1234-abcd1234abcd/resourceGroups/CLOUD-SHELL-STORAGE-WESTEUROPE/providers/Microsoft.Compute/virtualMachines/cc-warehouse-app-server"
}
},
"enabled": true,
"keyEncryptionKey": null
}
],
"name": "cc-warehouse-app_DataDisk_0",
"statuses": [
{
"code": "EncryptionState/encrypted",
"displayStatus": "Encryption is enabled on disk",
"level": "Info",
"message": null,
"time": null
}
]
}
],
"status": [
{
"code": "ProvisioningState/succeeded",
"displayStatus": "Provisioning succeeded",
"level": "Info",
"message": "Encryption succeeded for data volumes",
"time": null
}
],
"substatus": [
{
"code": "ComponentStatus/Microsoft.Azure.Security.AzureDiskEncryptionForLinux/succeeded",
"displayStatus": "Provisioning succeeded",
"level": "Info",
"message": "{\"os\": \"EncryptionInProgress\", \"data\": \"NotMounted\"}",
"time": null
}
]
} - Follow the steps above, for other not encrypted Azure Virtual Machines in the current subscription as well as in other subscriptions in your Azure Cloud.